The Yellow Team symbolizes energy, optimism, and creativity, often driving innovation and enthusiasm within a group. Embracing these qualities can help your projects shine and foster a collaborative environment where ideas flourish. Discover how the Yellow Team's unique strengths can elevate your efforts by reading the rest of the article.
Table of Comparison
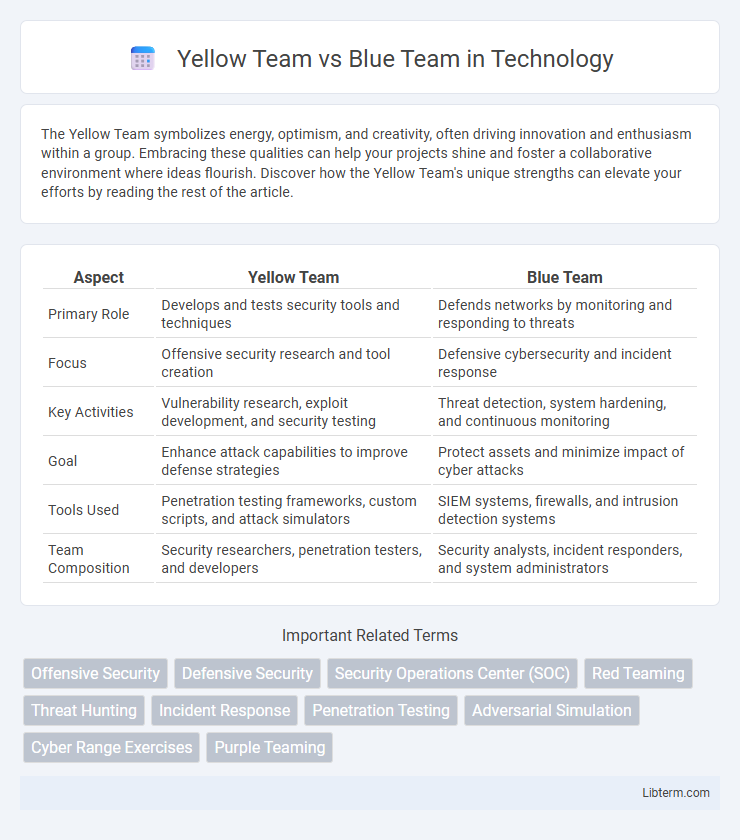
| Aspect | Yellow Team | Blue Team |
|---|---|---|
| Primary Role | Develops and tests security tools and techniques | Defends networks by monitoring and responding to threats |
| Focus | Offensive security research and tool creation | Defensive cybersecurity and incident response |
| Key Activities | Vulnerability research, exploit development, and security testing | Threat detection, system hardening, and continuous monitoring |
| Goal | Enhance attack capabilities to improve defense strategies | Protect assets and minimize impact of cyber attacks |
| Tools Used | Penetration testing frameworks, custom scripts, and attack simulators | SIEM systems, firewalls, and intrusion detection systems |
| Team Composition | Security researchers, penetration testers, and developers | Security analysts, incident responders, and system administrators |
Introduction to Yellow Team and Blue Team
Yellow Team in cybersecurity specializes in offensive strategies, focusing on penetration testing, vulnerability assessments, and simulating cyberattacks to identify security weaknesses. Blue Team is responsible for defense, continuously monitoring networks, implementing security controls, and responding to incidents to protect organizational assets from real threats. Both teams collaborate to enhance overall security posture through proactive detection and reactive defense mechanisms.
Core Objectives of Yellow Team
The Yellow Team's core objectives center on proactive threat detection, cybersecurity risk assessment, and vulnerability management to prevent security breaches. This team specializes in continuous monitoring, incident identification, and real-time alerting to minimize potential damage from cyber attacks. Their strategic focus includes enhancing the organization's security posture by implementing advanced threat intelligence and compliance measures.
Core Objectives of Blue Team
The Blue Team's core objectives center on defending organizational assets by continuously monitoring network traffic and system activities to detect and respond to cyber threats in real time. They implement robust security measures such as firewalls, intrusion detection systems, and endpoint protection to prevent unauthorized access and mitigate vulnerabilities. Regular vulnerability assessments, incident response planning, and threat intelligence analysis are critical in maintaining the integrity, confidentiality, and availability of information systems.
Key Differences Between Yellow and Blue Teams
Yellow Teams specialize in proactive defense strategies, focusing on vulnerability assessments, penetration testing, and threat hunting to identify and mitigate potential security weaknesses. Blue Teams concentrate on reactive defense measures, continuously monitoring networks, detecting intrusions, and responding to security incidents to protect assets in real time. The primary distinction lies in Yellow Teams simulating attacks to improve security posture, while Blue Teams maintain and enforce security protocols to defend against actual threats.
Roles and Responsibilities Overview
Yellow Team specializes in offensive cybersecurity measures such as penetration testing, vulnerability assessments, and red teaming exercises aimed at identifying system weaknesses before attackers do. Blue Team focuses on defensive strategies including continuous network monitoring, incident response, threat intelligence analysis, and implementing security policies to protect organizational assets. Both teams collaborate by sharing findings and insights to strengthen overall cyber resilience and ensure comprehensive protection against evolving threats.
Strategies Employed by Yellow Team
Yellow Team employs proactive threat hunting strategies that prioritize early detection of cyber threats through advanced analytics and continuous network monitoring. Their approach integrates behavioral analysis and machine learning algorithms to identify anomalies and potential breaches before they escalate. Emphasizing collaboration, the Yellow Team coordinates closely with incident response units to swiftly contain and mitigate identified risks.
Defense Techniques of Blue Team
The Blue Team employs advanced defense techniques such as network segmentation, continuous monitoring, and threat intelligence integration to detect and mitigate cyber threats in real time. Utilizing intrusion detection systems (IDS), endpoint protection, and robust incident response protocols, the Blue Team strengthens organizational cybersecurity postures against sophisticated attacks. Emphasizing proactive vulnerability management and regular security training, they minimize attack surfaces and enhance overall resilience against persistent threats.
Collaboration and Communication Dynamics
Yellow Team and Blue Team prioritize seamless collaboration and communication to enhance cybersecurity defenses and incident response effectiveness. Yellow Team specializes in threat intelligence sharing, while Blue Team focuses on real-time monitoring and defense strategies, ensuring a dynamic exchange of critical information. Their integrated communication protocols enable rapid identification, containment, and mitigation of cyber threats, significantly reducing organizational risk.
Common Challenges Faced in Cybersecurity Teams
Yellow Teams and Blue Teams in cybersecurity often face challenges such as maintaining up-to-date threat intelligence to effectively anticipate evolving cyberattacks. Coordinating communication and collaboration between offensive tactics (Yellow Team) and defensive strategies (Blue Team) proves difficult due to differing objectives and methodologies. Limited resources and time constraints further hinder continuous monitoring, vulnerability assessment, and rapid incident response, impacting overall security posture.
Future Trends in Yellow Team and Blue Team Collaboration
Future trends in Yellow Team and Blue Team collaboration emphasize increased integration of AI-driven threat detection and automated response systems to enhance real-time cyber defense capabilities. Enhanced information sharing platforms powered by blockchain technology are set to improve transparency and trust between offensive and defensive teams, enabling more effective vulnerability assessments and proactive security measures. The adoption of adaptive machine learning models will further refine attack simulations and defense strategies, fostering a dynamic and continuous improvement cycle in cybersecurity operations.
Yellow Team Infographic
 libterm.com
libterm.com