Peer-to-peer logging enables decentralized data recording by allowing individual nodes to share and store log information collaboratively, enhancing fault tolerance and scalability. This method reduces dependency on central servers, improving real-time access and robustness in distributed systems. Discover how peer-to-peer logging can optimize your system's performance and reliability by reading the rest of the article.
Table of Comparison
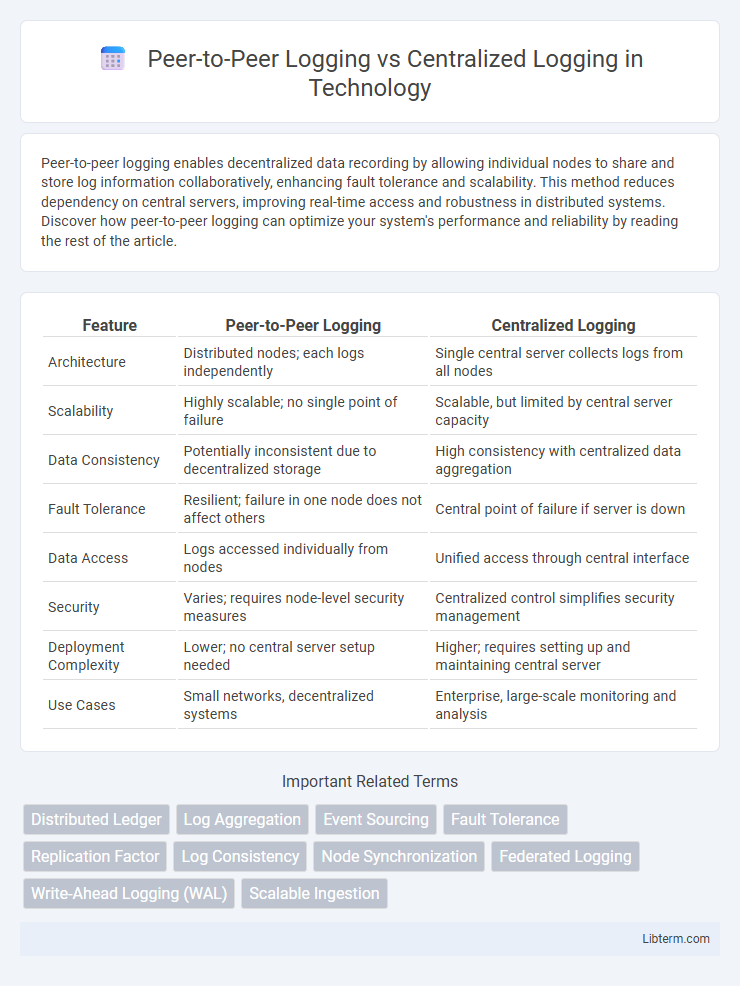
| Feature | Peer-to-Peer Logging | Centralized Logging |
|---|---|---|
| Architecture | Distributed nodes; each logs independently | Single central server collects logs from all nodes |
| Scalability | Highly scalable; no single point of failure | Scalable, but limited by central server capacity |
| Data Consistency | Potentially inconsistent due to decentralized storage | High consistency with centralized data aggregation |
| Fault Tolerance | Resilient; failure in one node does not affect others | Central point of failure if server is down |
| Data Access | Logs accessed individually from nodes | Unified access through central interface |
| Security | Varies; requires node-level security measures | Centralized control simplifies security management |
| Deployment Complexity | Lower; no central server setup needed | Higher; requires setting up and maintaining central server |
| Use Cases | Small networks, decentralized systems | Enterprise, large-scale monitoring and analysis |
Introduction to Logging Architectures
Peer-to-peer logging architecture distributes log data across multiple nodes, enhancing fault tolerance and scalability by eliminating a single point of failure. Centralized logging architecture aggregates log data into a single server or cluster, simplifying monitoring, analysis, and correlation of events across complex systems. Selecting between peer-to-peer and centralized logging depends on factors such as system size, network topology, and the required speed of log retrieval and processing.
What is Peer-to-Peer Logging?
Peer-to-Peer Logging is a decentralized approach where each node in a network independently collects, stores, and processes log data without relying on a central server. This method enhances fault tolerance and scalability by distributing the logging workload across multiple devices, reducing single points of failure. Peer-to-Peer Logging enables real-time log sharing and collaborative analysis among nodes, improving network transparency and responsiveness.
Understanding Centralized Logging
Centralized logging consolidates log data from multiple sources into a single repository, enabling efficient monitoring, analysis, and troubleshooting across distributed systems. It streamlines log management by providing unified visibility, enabling faster detection of issues and easier compliance auditing through centralized access controls and search capabilities. This approach significantly reduces complexity compared to peer-to-peer logging, which requires managing logs individually across each node, leading to potential inconsistencies and increased administrative overhead.
Key Differences Between Peer-to-Peer and Centralized Logging
Peer-to-peer logging distributes log data across multiple nodes, ensuring greater fault tolerance and real-time local analysis, whereas centralized logging consolidates all log information into a single repository for simplified management and auditing. Peer-to-peer systems excel in scalability and resilience by eliminating single points of failure, while centralized systems provide a unified view for easier compliance and troubleshooting. Key differences include data storage location, fault tolerance, scalability, and the complexity of log aggregation and processing.
Scalability Comparison: P2P vs Centralized Logging
Peer-to-peer logging offers superior scalability by distributing log data across multiple nodes, eliminating bottlenecks commonly found in centralized logging systems that rely on a single aggregator or server. In centralized logging, scalability is limited by the capacity of the central server and network bandwidth, leading to potential performance degradation as log volume increases. P2P logging systems dynamically balance load and storage, enabling seamless scaling in large distributed environments without the need for significant infrastructure upgrades.
Security Considerations in Both Logging Approaches
Peer-to-peer logging offers enhanced data privacy by distributing logs across multiple nodes, minimizing single points of failure and reducing risks of centralized data breaches. Centralized logging simplifies security management through unified access controls and streamlined monitoring but can become a high-value target for attackers if not properly secured. Implementing robust encryption, strict access policies, and regular audits is critical in both approaches to maintaining log integrity and confidentiality.
Fault Tolerance and Reliability Analysis
Peer-to-peer logging enhances fault tolerance by distributing log data across multiple nodes, eliminating single points of failure and ensuring data availability even if some nodes go offline. Centralized logging systems, while easier to manage and query, can suffer from reliability issues due to reliance on a single server or cluster, which becomes a bottleneck and risk factor during outages. Fault tolerance in peer-to-peer architectures increases overall system reliability by leveraging redundancy and decentralized storage, whereas centralized solutions depend heavily on robust infrastructure and backup mechanisms to maintain uptime.
Performance and Latency Aspects
Peer-to-peer logging distributes log generation and storage across multiple nodes, reducing bottlenecks and enabling faster, localized access, which significantly lowers latency. Centralized logging aggregates logs into a single system, potentially introducing network delays and performance degradation due to intensive data transmission and processing demands. Systems requiring real-time analysis often benefit from peer-to-peer architectures to maintain high throughput and minimal latency, whereas centralized logging may struggle with scalability under heavy load.
Use Cases Best Suited for Each Logging Model
Peer-to-peer logging excels in decentralized environments where real-time data sharing, fault tolerance, and autonomy among distributed nodes are critical, such as in blockchain networks and edge computing. Centralized logging is ideal for enterprises requiring streamlined log aggregation, comprehensive analysis, and simplified compliance across multiple systems, like large-scale IT infrastructures and cloud service providers. Selecting the appropriate model depends on the system architecture, scalability requirements, and the need for centralized oversight versus distributed resilience.
Choosing the Right Logging Strategy for Your Organization
Choosing between peer-to-peer logging and centralized logging depends on your organization's scalability, security requirements, and infrastructure complexity. Peer-to-peer logging enhances fault tolerance and reduces bottlenecks by distributing logs across multiple nodes, ideal for decentralized systems with high availability needs. Centralized logging simplifies log management and analysis by aggregating data into a single repository, making it suitable for organizations prioritizing ease of monitoring and compliance.
Peer-to-Peer Logging Infographic
 libterm.com
libterm.com