Cipher is a method of transforming text to conceal its meaning, commonly used in cryptography for secure communication. Various types of ciphers, such as substitution and transposition, play crucial roles in protecting sensitive information from unauthorized access. Explore the rest of this article to understand how ciphers work and enhance your knowledge of data security.
Table of Comparison
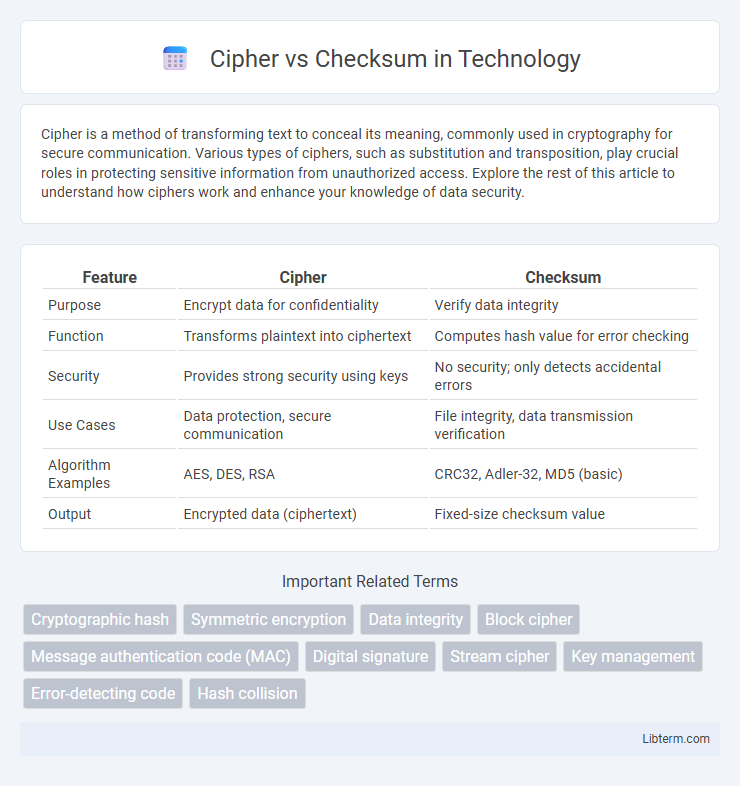
| Feature | Cipher | Checksum |
|---|---|---|
| Purpose | Encrypt data for confidentiality | Verify data integrity |
| Function | Transforms plaintext into ciphertext | Computes hash value for error checking |
| Security | Provides strong security using keys | No security; only detects accidental errors |
| Use Cases | Data protection, secure communication | File integrity, data transmission verification |
| Algorithm Examples | AES, DES, RSA | CRC32, Adler-32, MD5 (basic) |
| Output | Encrypted data (ciphertext) | Fixed-size checksum value |
Understanding Ciphers: Definition and Purpose
Ciphers are algorithms designed to transform readable data into an unreadable format through encryption, ensuring data confidentiality and security. They utilize keys to systematically alter plaintext into ciphertext, preventing unauthorized access and maintaining information integrity during transmission or storage. Unlike checksums, which detect errors in data, ciphers actively protect data by concealing its true content from potential attackers.
What is a Checksum?
A checksum is a fixed-size numeric value generated from a data set using a specific algorithm, primarily to detect errors in data transmission or storage. It enables verification of data integrity by comparing the computed checksum value before and after data transfer, ensuring no unintended modifications have occurred. Unlike ciphers that encrypt data for confidentiality, checksums provide a simple method for error detection without offering data protection against malicious attacks.
Key Differences Between Cipher and Checksum
A cipher is an algorithm used for encrypting and decrypting data to ensure confidentiality, relying on secret keys to transform plaintext into ciphertext and back. A checksum is a value computed from data to detect errors or alterations, primarily used for data integrity verification without involving any secret keys. The key difference lies in purpose: ciphers secure data by encryption requiring keys, while checksums validate data integrity through error detection without encryption.
Use Cases of Ciphers in Data Security
Ciphers are essential in data security for encrypting sensitive information, ensuring confidentiality and protecting against unauthorized access during transmission and storage. They are deployed in secure communication protocols like SSL/TLS, safeguarding online transactions, email encryption, and VPNs. Unlike checksums, which primarily detect data corruption, ciphers provide robust defense against data breaches by transforming readable data into unreadable ciphertext.
Applications of Checksums in Data Integrity
Checksums play a crucial role in verifying data integrity by detecting errors in files or messages transmitted over networks or stored on devices. Commonly used in network communications, storage systems, and software distribution, checksums quickly identify accidental corruption without the computational complexity of cryptographic ciphers. Algorithms like CRC32 and MD5 enable efficient error-checking by generating unique hash values that ensure data remains unaltered during transfer or storage.
How Ciphers Work: Basic Mechanisms
Ciphers work by transforming plaintext into ciphertext through algorithms that use keys to ensure data confidentiality. Symmetric ciphers use the same key for encryption and decryption, while asymmetric ciphers employ a public key for encryption and a private key for decryption. These mechanisms rely on complex mathematical functions such as substitution, permutation, and modular arithmetic to secure information against unauthorized access.
How Checksums Work: Generation and Verification
Checksums function by generating a fixed-size string or number derived from the content of a data set using algorithms such as CRC32 or MD5, enabling error detection. During verification, the same checksum algorithm processes the received data to produce a new checksum, which is then compared to the original; discrepancies indicate potential data corruption or tampering. This process ensures data integrity but lacks encryption capabilities, distinguishing it from ciphers that transform data for confidentiality.
Advantages and Limitations of Ciphers
Ciphers provide strong data confidentiality by transforming plaintext into unreadable ciphertext, ensuring secure communication against unauthorized access. They offer resistance to brute-force attacks depending on key complexity and algorithm strength but require substantial computational resources and key management. Limitations include vulnerability to side-channel attacks and potential weaknesses if improper key lengths or outdated algorithms are used.
Benefits and Drawbacks of Checksums
Checksums provide a fast and simple method to detect errors in data transmission or storage, making them efficient for integrity verification in low-resource environments. However, their main drawback lies in limited security, as checksums are vulnerable to intentional tampering and collisions, unlike cryptographic ciphers which offer robust encryption and data protection. The simplicity of checksums results in lower computational overhead but also restricts their effectiveness against sophisticated cyber threats and malicious modifications.
Cipher vs Checksum: Choosing the Right Solution
Cipher encryption transforms data into a secure format using algorithms like AES or RSA, ensuring confidentiality and protection against unauthorized access. Checksums, generated through hash functions such as MD5 or CRC, verify data integrity by detecting accidental errors during transmission or storage. Selecting between a cipher and a checksum depends on whether the priority is securing data privacy or validating data accuracy.
Cipher Infographic
 libterm.com
libterm.com