A decoy file is a cybersecurity tactic designed to mislead hackers by mimicking sensitive data without containing real information. These files help protect your actual data by diverting unauthorized users and triggering alerts when accessed. Explore the rest of the article to learn how decoy files can strengthen your security strategy.
Table of Comparison
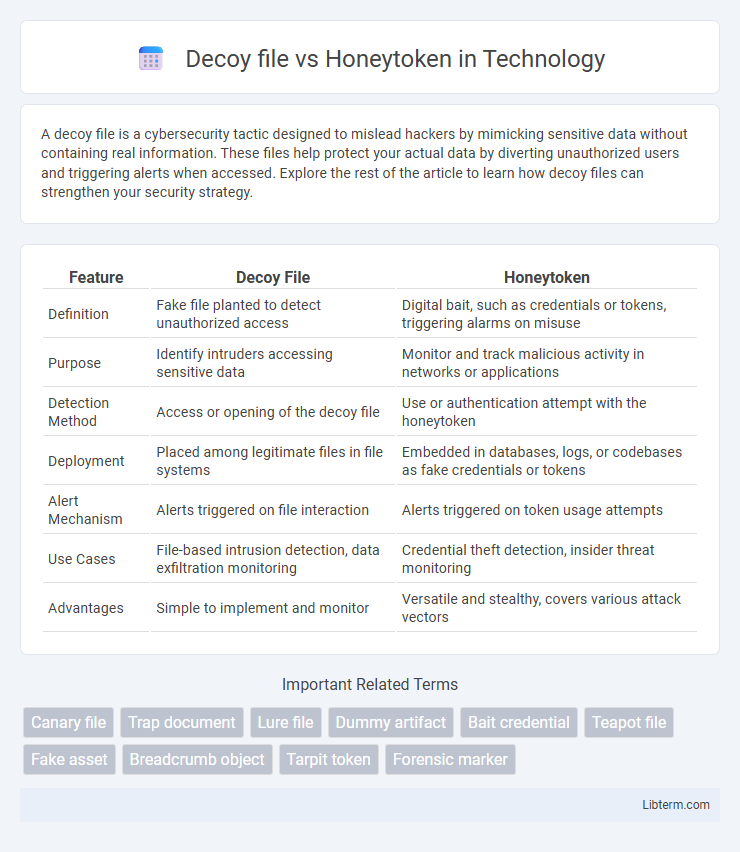
| Feature | Decoy File | Honeytoken |
|---|---|---|
| Definition | Fake file planted to detect unauthorized access | Digital bait, such as credentials or tokens, triggering alarms on misuse |
| Purpose | Identify intruders accessing sensitive data | Monitor and track malicious activity in networks or applications |
| Detection Method | Access or opening of the decoy file | Use or authentication attempt with the honeytoken |
| Deployment | Placed among legitimate files in file systems | Embedded in databases, logs, or codebases as fake credentials or tokens |
| Alert Mechanism | Alerts triggered on file interaction | Alerts triggered on token usage attempts |
| Use Cases | File-based intrusion detection, data exfiltration monitoring | Credential theft detection, insider threat monitoring |
| Advantages | Simple to implement and monitor | Versatile and stealthy, covers various attack vectors |
Introduction to Decoy Files and Honeytokens
Decoy files are fake documents designed to attract and detect unauthorized access by mimicking legitimate files, enhancing cybersecurity through deception. Honeytokens are embedded identifiers or data fragments that trigger alerts when accessed or used, providing early warning of insider threats or breaches. Both techniques serve as proactive defense measures by misleading attackers and enabling rapid incident response.
Understanding Decoy Files: Definition and Purpose
Decoy files are strategically crafted digital artifacts designed to lure cyber attackers into interacting with false data while hiding real valuable information. Unlike generic honeytokens, decoy files mimic legitimate files such as financial records or confidential documents, increasing the likelihood of detection. Their purpose centers on early threat identification and diverting malicious activity away from authentic assets, enhancing cybersecurity defense mechanisms.
What Are Honeytokens? Key Concepts Explained
Honeytokens are deceptive digital artifacts designed to detect unauthorized access or data breaches by triggering alerts when interacted with. Unlike decoy files that mimic valuable data to distract attackers, honeytokens can be any data element such as fake credentials, database entries, or API keys embedded within systems to monitor malicious activity. Effective deployment of honeytokens involves integrating uniquely identifiable markers that provide early warning signs without disrupting legitimate operations.
Differences Between Decoy Files and Honeytokens
Decoy files are fake documents designed to attract unauthorized users and monitor suspicious activity, while honeytokens are broader deceptive elements such as login credentials or database entries used to detect insider threats or breaches. Decoy files typically resemble legitimate files to lure attackers, whereas honeytokens can be any data artifact that triggers alerts when accessed or used improperly. The key difference lies in their scope: decoy files are a subset of honeytokens focused on file-based deception, whereas honeytokens encompass a diverse range of digital traps beyond just files.
Use Cases: When to Deploy Decoy Files
Decoy files are strategically deployed within networks to detect unauthorized access by mimicking sensitive data, thereby triggering alerts when accessed by intruders. Use cases for decoy files include monitoring insider threats, identifying malware activity, and protecting intellectual property by creating realistic targets that blend seamlessly with genuine files. Honeytokens, while similar, are often lightweight and embedded within databases or logs, making decoy files more suitable for environments requiring extensive file-level deception and detailed forensic analysis.
Applications of Honeytokens in Cybersecurity
Honeytokens serve as strategic cybersecurity assets designed to lure attackers by mimicking sensitive data, such as fake credentials or documents, to detect unauthorized access or insider threats. Their applications extend to fraud detection, data leak tracing, and enhancing network visibility by triggering alerts when the honeytoken is accessed or exfiltrated. Unlike decoy files, which are primarily static traps, honeytokens are dynamic and versatile, providing actionable intelligence and real-time threat response capabilities in complex cyber environments.
Benefits of Using Decoy Files vs. Honeytokens
Decoy files provide a tangible, realistic trap by mimicking valuable data, enticing attackers to interact with them and revealing unauthorized access attempts. Honeytokens, being lightweight and flexible, can be embedded in various data types such as credentials or documents, enabling broader detection without the need for complex file creation. Utilizing decoy files offers the advantage of detailed forensic analysis through file access patterns, while honeytokens excel in scalability and low maintenance, making both essential for comprehensive deception strategies.
Potential Risks and Limitations
Decoy files can be inadvertently accessed or deleted by legitimate users, causing operational disruptions and false positives in security monitoring. Honeytokens risk being detected by savvy attackers, which could lead to attackers avoiding traps or using the presence of honeytokens to mislead defenders. Both approaches have limitations in scalability, requiring continuous updates and integration with incident response systems to maintain effectiveness.
Best Practices for Implementing Decoy Files and Honeytokens
Implementing decoy files and honeytokens requires strategic placement to maximize detection without disrupting normal operations. Decoy files should mimic sensitive or critical data, be closely monitored for unauthorized access or modifications, and integrated with real-time alert systems for prompt incident response. Honeytokens benefit from unique, easily identifiable markers embedded within digital environments, ensuring any interaction triggers security alerts and enhances insider threat detection.
Future Trends in Decoy File and Honeytoken Technologies
Future trends in decoy file and honeytoken technologies emphasize advanced behavioral analytics and AI-driven anomaly detection to increase threat identification accuracy. Integration with cloud-native environments and automation platforms enhances scalability and real-time response capabilities. Enhanced encryption methods and adaptive deployment strategies improve stealth effectiveness, reducing false positives and accelerating incident response times.
Decoy file Infographic
 libterm.com
libterm.com