A Message Authentication Code (MAC) ensures data integrity and authenticity by generating a unique code based on both the message content and a secret key. This cryptographic technique prevents unauthorized alterations and verifies the sender's identity, enhancing communication security. Explore the rest of the article to understand how MACs protect your sensitive information.
Table of Comparison
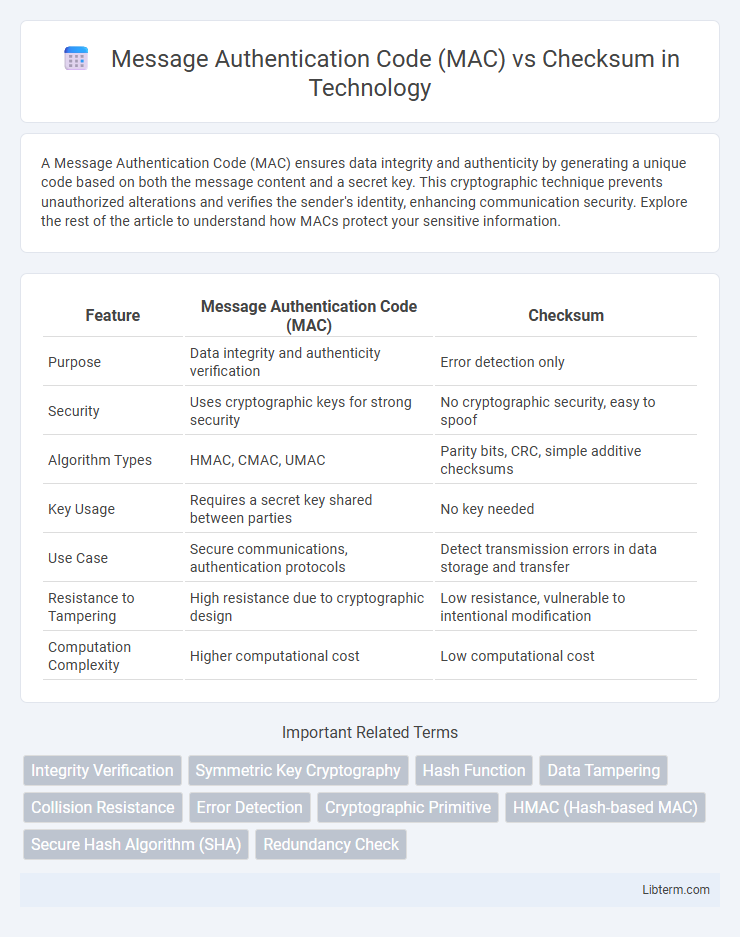
| Feature | Message Authentication Code (MAC) | Checksum |
|---|---|---|
| Purpose | Data integrity and authenticity verification | Error detection only |
| Security | Uses cryptographic keys for strong security | No cryptographic security, easy to spoof |
| Algorithm Types | HMAC, CMAC, UMAC | Parity bits, CRC, simple additive checksums |
| Key Usage | Requires a secret key shared between parties | No key needed |
| Use Case | Secure communications, authentication protocols | Detect transmission errors in data storage and transfer |
| Resistance to Tampering | High resistance due to cryptographic design | Low resistance, vulnerable to intentional modification |
| Computation Complexity | Higher computational cost | Low computational cost |
Understanding Message Authentication Codes (MAC)
Message Authentication Codes (MAC) provide data integrity and authentication by generating a unique code using a secret key and the message content, ensuring that the message has not been tampered with and verifying the sender's identity. Unlike simple checksums, which detect accidental errors but offer no security against intentional modifications, MACs use cryptographic algorithms such as HMAC (Hash-based Message Authentication Code) to resist forgery and replay attacks. Implementations of MACs are critical in secure communication protocols like TLS and IPSec, where robust authentication and message integrity are mandatory.
What is a Checksum?
A checksum is a value calculated from a data set to detect errors during transmission or storage by verifying data integrity. Unlike a Message Authentication Code (MAC), which uses a secret key to provide both data integrity and authenticity, a checksum is typically a simple error-detection code computed through algorithms like CRC or summation without cryptographic security. Checksums ensure basic error checking but cannot protect against intentional data tampering or provide authentication guarantees.
Core Differences between MAC and Checksum
Message Authentication Code (MAC) ensures data integrity and authenticity by using a cryptographic key to generate a unique code, making it resistant to tampering and forgery. In contrast, a checksum is a simple error-detecting code computed from the data without a key, primarily designed to detect accidental errors rather than malicious modifications. The core difference lies in MAC's cryptographic security and key dependency versus checksum's basic error detection without providing authentication.
How MACs Ensure Data Integrity and Authenticity
Message Authentication Codes (MACs) ensure data integrity and authenticity by generating a unique cryptographic tag using a secret key combined with the message content, making it computationally infeasible for attackers to forge valid tags without the key. Unlike simple checksums that only detect accidental errors, MACs protect against intentional alterations and verify that data originates from a trusted sender. This cryptographic verification process guarantees both the integrity and authenticity of the transmitted data in secure communication systems.
The Role of Checksums in Error Detection
Checksums serve as simple error detection mechanisms by calculating a fixed-size value from data bits to identify accidental alterations during transmission. Unlike Message Authentication Codes (MACs), which provide cryptographic integrity and authentication by incorporating secret keys, checksums merely detect unintentional errors without protecting against intentional tampering. Common checksum algorithms include CRC and simple additive methods, optimized for quick detection of transmission errors in networking and storage systems.
Security Strength: MAC vs Checksum
Message Authentication Code (MAC) provides significantly stronger security compared to checksums by incorporating a secret cryptographic key, ensuring data integrity and authenticity. Checksums are primarily designed for error detection and lack cryptographic strength, making them vulnerable to intentional tampering and forgery. Consequently, MACs are widely employed in secure communications and data verification where protection against malicious attacks is critical.
Common Algorithms for MAC and Checksum
Message Authentication Code (MAC) commonly uses algorithms such as HMAC (Hash-based Message Authentication Code) with SHA-256 and CMAC (Cipher-based Message Authentication Code) leveraging AES. Checksum algorithms primarily include CRC32 and Adler-32, designed for error detection in data transmission. MAC algorithms provide cryptographic security ensuring data integrity and authenticity, whereas checksum algorithms focus on detecting accidental errors without cryptographic guarantees.
Use Cases: When to Use MAC or Checksum
Message Authentication Code (MAC) is crucial for ensuring data integrity and authenticating the sender in secure communications, making it ideal for applications like financial transactions, secure messaging, and VPNs where security against tampering is paramount. Checksums are primarily used for error detection in data transmission and storage systems, such as verifying file integrity during downloads or within network packets, where protection against accidental corruption rather than malicious attacks is the main goal. Choosing between MAC and checksum depends on the security requirements; MACs guarantee both integrity and authenticity, while checksums offer basic error checking with minimal computational overhead.
Limitations and Vulnerabilities of Each Method
Message Authentication Code (MAC) provides strong data integrity and authenticity by using a secret key, but its security depends heavily on key management and cannot prevent attacks if the key is compromised. Checksums, designed primarily for error detection, are vulnerable to intentional tampering since they lack cryptographic protection and can be easily forged or altered without detection. Both methods have limitations: MACs require secure key distribution and pose computational overhead, while checksums fail against malicious attacks and offer no assurance of data authenticity.
Choosing the Right Method for Your Application
Message Authentication Code (MAC) offers cryptographic security by verifying both data integrity and authenticity, making it ideal for applications requiring protection against tampering and unauthorized access. Checksums detect accidental errors in data transmission but lack cryptographic strength, rendering them unsuitable for security-sensitive environments. Selecting between MAC and checksum depends on the application's need for robust security features versus simple error detection.
Message Authentication Code (MAC) Infographic
 libterm.com
libterm.com