Elliptic Curve Key Exchange leverages the mathematics of elliptic curves to enable secure and efficient cryptographic key sharing over public channels. This method provides strong security with smaller key sizes compared to traditional algorithms, making it ideal for modern applications requiring high performance and low resource consumption. Explore the rest of the article to understand how this advanced technique can enhance your cryptographic security.
Table of Comparison
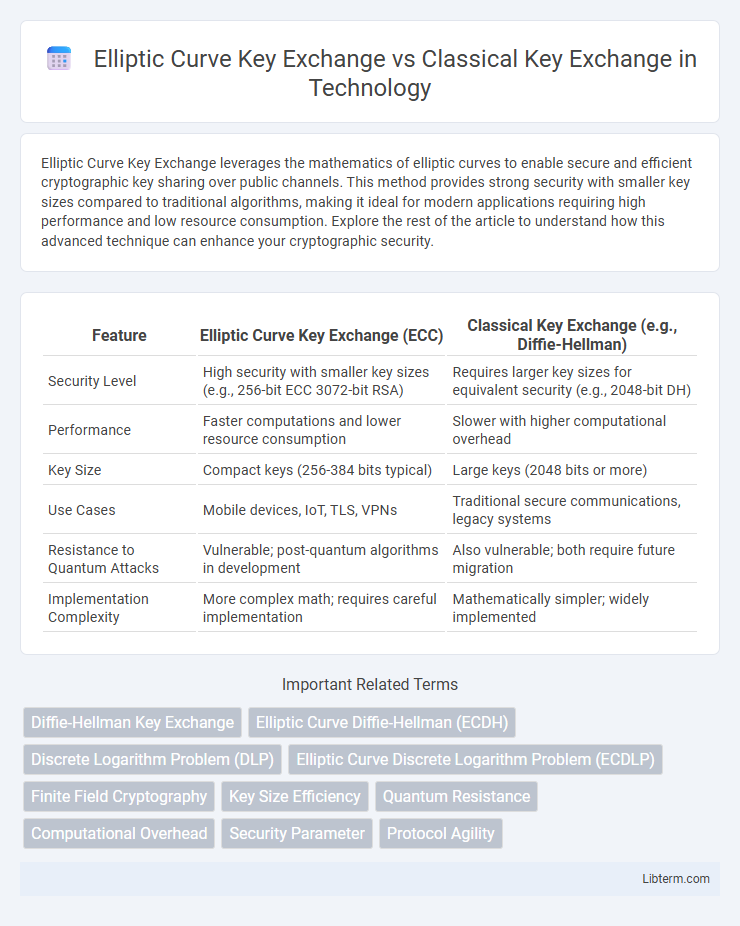
| Feature | Elliptic Curve Key Exchange (ECC) | Classical Key Exchange (e.g., Diffie-Hellman) |
|---|---|---|
| Security Level | High security with smaller key sizes (e.g., 256-bit ECC 3072-bit RSA) | Requires larger key sizes for equivalent security (e.g., 2048-bit DH) |
| Performance | Faster computations and lower resource consumption | Slower with higher computational overhead |
| Key Size | Compact keys (256-384 bits typical) | Large keys (2048 bits or more) |
| Use Cases | Mobile devices, IoT, TLS, VPNs | Traditional secure communications, legacy systems |
| Resistance to Quantum Attacks | Vulnerable; post-quantum algorithms in development | Also vulnerable; both require future migration |
| Implementation Complexity | More complex math; requires careful implementation | Mathematically simpler; widely implemented |
Introduction to Key Exchange Methods
Elliptic Curve Key Exchange utilizes the mathematical properties of elliptic curves over finite fields to enable secure, efficient cryptographic key sharing with smaller key sizes compared to classical methods. Classical Key Exchange protocols, such as Diffie-Hellman, rely on the computational difficulty of discrete logarithms in large prime modulus groups, requiring larger keys for equivalent security. The reduced key size and computational efficiency of Elliptic Curve Cryptography result in faster processing and lower resource consumption, making it highly suitable for modern applications like mobile devices and IoT systems.
Overview of Classical Key Exchange Protocols
Classical key exchange protocols, such as Diffie-Hellman and RSA, rely on the computational hardness of problems like discrete logarithms and integer factorization for secure key distribution. These methods involve exchanging public keys over insecure channels to establish a shared secret used for symmetric encryption. Their security is challenged by advancing computational power and the potential emergence of quantum computing, which motivates the shift toward elliptic curve key exchange mechanisms offering smaller key sizes and enhanced security per bit.
Fundamentals of Elliptic Curve Key Exchange
Elliptic Curve Key Exchange relies on the mathematical properties of elliptic curves over finite fields to provide secure cryptographic keys with smaller key sizes compared to classical key exchanges like Diffie-Hellman, which depend on the discrete logarithm problem in multiplicative groups. The security of Elliptic Curve Cryptography (ECC) stems from the difficulty of the Elliptic Curve Discrete Logarithm Problem (ECDLP), making it efficient and well-suited for environments with limited computational resources. ECC achieves comparable levels of security with significantly reduced computational effort and bandwidth consumption, making it a preferred choice for modern secure communication protocols.
Security Strength: Elliptic Curve vs Classical Methods
Elliptic Curve Key Exchange offers stronger security per bit compared to classical methods like RSA or Diffie-Hellman, enabling comparable cryptographic strength with smaller key sizes. The mathematical complexity of the Elliptic Curve Discrete Logarithm Problem (ECDLP) makes it highly resistant to attacks, providing efficient protection against quantum threats and conventional cryptanalysis. Classical key exchange protocols rely on larger keys and more computational resources, often leading to slower performance while maintaining equivalent security levels.
Performance and Efficiency Comparison
Elliptic Curve Key Exchange (ECDH) offers significantly better performance and efficiency compared to classical key exchange methods like RSA or Diffie-Hellman, requiring smaller key sizes to achieve equivalent security levels. ECDH's computational efficiency reduces processing time and power consumption, making it ideal for resource-constrained environments such as mobile devices and IoT systems. This efficiency translates to faster key generation and exchange processes, enhancing overall system responsiveness without compromising cryptographic strength.
Key Sizes and Computational Requirements
Elliptic Curve Key Exchange offers equivalent security to classical key exchange methods like RSA but with significantly smaller key sizes, typically 256 bits for ECC compared to 3072 bits for RSA. Smaller keys in ECC lead to reduced computational requirements, resulting in faster key generation, encryption, and decryption processes while consuming less power and bandwidth. These advantages make Elliptic Curve Cryptography highly suitable for resource-constrained environments such as mobile devices and IoT applications.
Implementation Challenges and Considerations
Elliptic Curve Key Exchange offers stronger security per bit with smaller key sizes compared to classical key exchange methods like RSA or Diffie-Hellman, reducing computational overhead and memory usage, which is crucial for resource-constrained environments. Implementation challenges include ensuring constant-time operations to prevent timing attacks, handling complex mathematical computations on elliptic curves, and managing secure generation and storage of curve parameters and keys. Considerations involve selecting widely accepted curves such as Curve25519 or P-256 for interoperability and resistance against known vulnerabilities while maintaining compliance with cryptographic standards.
Use Cases in Modern Cryptographic Systems
Elliptic Curve Key Exchange (such as ECDH) offers compact key sizes and faster computations, making it ideal for resource-constrained environments like IoT devices and mobile applications. Classical key exchange algorithms, including Diffie-Hellman over finite fields, remain prevalent in legacy systems and scenarios requiring interoperability with older infrastructure. Modern cryptographic protocols increasingly adopt Elliptic Curve methods to enhance security while minimizing latency and bandwidth in secure communications.
Future Trends in Key Exchange Technologies
Elliptic Curve Key Exchange offers stronger security with smaller key sizes compared to classical key exchange methods like RSA and Diffie-Hellman, making it a preferred choice for future-proof cryptographic protocols. Advances in quantum computing are driving research into post-quantum cryptography, with lattice-based and code-based key exchange algorithms emerging to address vulnerabilities in both classical and elliptic curve cryptography. Hybrid approaches combining elliptic curve key exchange with post-quantum algorithms are expected to dominate next-generation secure communication frameworks.
Conclusion: Choosing the Right Key Exchange Method
Elliptic Curve Key Exchange offers superior security with shorter key lengths, enhancing performance and reducing resource consumption compared to classical methods like RSA or Diffie-Hellman. Organizations requiring high efficiency and strong encryption for constrained environments should prioritize Elliptic Curve cryptography. Classical Key Exchange remains relevant for compatibility with legacy systems but often involves larger keys and slower computations.
Elliptic Curve Key Exchange Infographic
 libterm.com
libterm.com