Network monitoring ensures your systems run smoothly by continuously tracking performance, detecting bottlenecks, and identifying security threats in real time. Effective monitoring tools provide valuable insights into traffic patterns and device health, enabling swift resolution of potential issues before they impact users. Discover how implementing the right network monitoring strategies can optimize your infrastructure by reading the rest of this article.
Table of Comparison
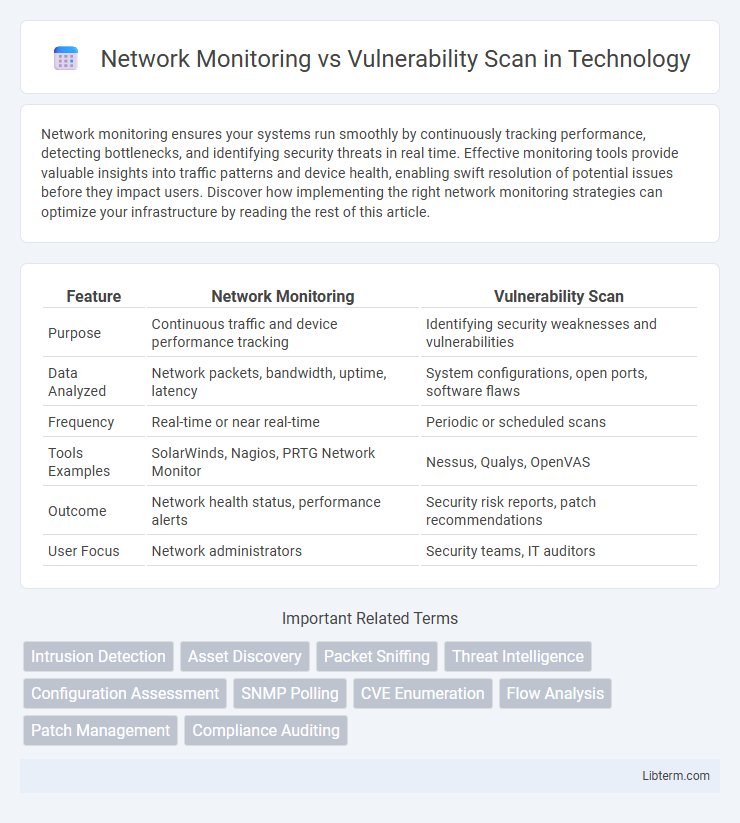
| Feature | Network Monitoring | Vulnerability Scan |
|---|---|---|
| Purpose | Continuous traffic and device performance tracking | Identifying security weaknesses and vulnerabilities |
| Data Analyzed | Network packets, bandwidth, uptime, latency | System configurations, open ports, software flaws |
| Frequency | Real-time or near real-time | Periodic or scheduled scans |
| Tools Examples | SolarWinds, Nagios, PRTG Network Monitor | Nessus, Qualys, OpenVAS |
| Outcome | Network health status, performance alerts | Security risk reports, patch recommendations |
| User Focus | Network administrators | Security teams, IT auditors |
Understanding Network Monitoring
Network monitoring involves continuously observing a network's traffic, performance, and security status to detect anomalies or failures in real-time. It uses tools like SNMP, NetFlow, and packet analyzers to gather data on network devices, traffic patterns, and connection health. This proactive approach helps in identifying issues such as bandwidth bottlenecks, device malfunctions, and potential security breaches before they impact network operations.
What Is Vulnerability Scanning?
Vulnerability scanning is an automated process that identifies security weaknesses in network devices, software, and systems by comparing configurations and software versions against a database of known vulnerabilities. Unlike network monitoring, which continuously observes network traffic and performance, vulnerability scanning proactively detects potential entry points for cyberattacks before they can be exploited. This scanning helps organizations prioritize patch management and strengthen their security posture by targeting specific vulnerabilities that pose the greatest risk.
Key Differences Between Network Monitoring and Vulnerability Scanning
Network monitoring continuously tracks network performance, availability, and traffic to identify anomalies, while vulnerability scanning systematically examines systems and devices to detect security weaknesses and potential exploits. Network monitoring provides real-time visibility into network health and operational status, whereas vulnerability scanning focuses on identifying outdated software, misconfigurations, and security loopholes. Both tools complement each other by enhancing cybersecurity posture through proactive detection and analysis of network threats and vulnerabilities.
Core Features of Network Monitoring Tools
Network monitoring tools continuously track network performance metrics such as bandwidth usage, latency, and device availability to ensure optimal operation and quick issue detection. These tools provide real-time alerts, traffic analysis, and detailed reporting, enabling proactive management and minimizing downtime. Core features include protocol analysis, device health monitoring, and automated fault detection, differentiating them from vulnerability scans that focus solely on identifying security weaknesses.
Essential Capabilities of Vulnerability Scanners
Vulnerability scanners excel at identifying security weaknesses by systematically assessing devices, applications, and networks against known threat databases and compliance standards. They provide detailed vulnerability reports highlighting risk severity, remediation guidance, and potential exploit pathways to prioritize patch management. Unlike network monitoring tools that track real-time performance and traffic anomalies, vulnerability scanners focus on proactive detection of exploitable flaws through automated and scheduled scanning.
Use Cases: When to Use Network Monitoring
Network monitoring is essential for real-time analysis of network performance, detecting traffic anomalies, and ensuring continuous uptime in enterprise environments. It is most effective during active incident response, capacity planning, and compliance auditing to promptly identify and troubleshoot connectivity issues or unauthorized access attempts. Organizations rely on network monitoring to maintain service level agreements (SLAs) and optimize bandwidth usage while minimizing downtime risks.
Use Cases: When to Use Vulnerability Scanning
Vulnerability scanning is essential for identifying security weaknesses in applications, systems, and networks before attackers can exploit them, making it ideal for routine security assessments and compliance audits. It is particularly useful in environments requiring continuous risk management, such as financial institutions and healthcare organizations handling sensitive data. This proactive approach helps prioritize remediation efforts by detecting known vulnerabilities, misconfigurations, and outdated software versions efficiently.
Integrating Network Monitoring with Vulnerability Scanning
Integrating network monitoring with vulnerability scanning enhances real-time threat detection by continuously analyzing network traffic alongside known security weaknesses. This combined approach allows organizations to promptly identify and remediate vulnerabilities that are actively being exploited within the network environment. Leveraging tools such as SIEM platforms that support both network monitoring data and vulnerability scan results improves overall security posture through comprehensive visibility and actionable insights.
Common Challenges and Best Practices
Network monitoring and vulnerability scanning both face challenges such as handling high data volumes, identifying false positives, and ensuring continuous coverage. Common best practices include integrating automated tools with manual analysis to improve accuracy, maintaining up-to-date threat intelligence to detect emerging risks, and implementing real-time alerting systems for prompt incident response. Effective coordination between monitoring and scanning processes enhances overall network security posture and reduces potential attack surfaces.
Choosing the Right Network Security Approach
Network monitoring continuously tracks network traffic and performance to detect anomalies and potential security threats in real-time, while vulnerability scanning identifies security weaknesses in systems and applications at scheduled intervals. Selecting the right network security approach depends on balancing proactive threat detection through continuous monitoring with periodic vulnerability assessments to patch exploitable flaws. Integrating both strategies enhances overall security posture by ensuring immediate threat awareness and systematic risk mitigation.
Network Monitoring Infographic
 libterm.com
libterm.com