Pentesting identifies security weaknesses by simulating cyberattacks, while vulnerability assessment scans systems to detect and prioritize potential threats. Both methods are essential for maintaining a robust cybersecurity posture and protecting sensitive information from unauthorized access or damage. Discover how you can strengthen your defenses by exploring the full article.
Table of Comparison
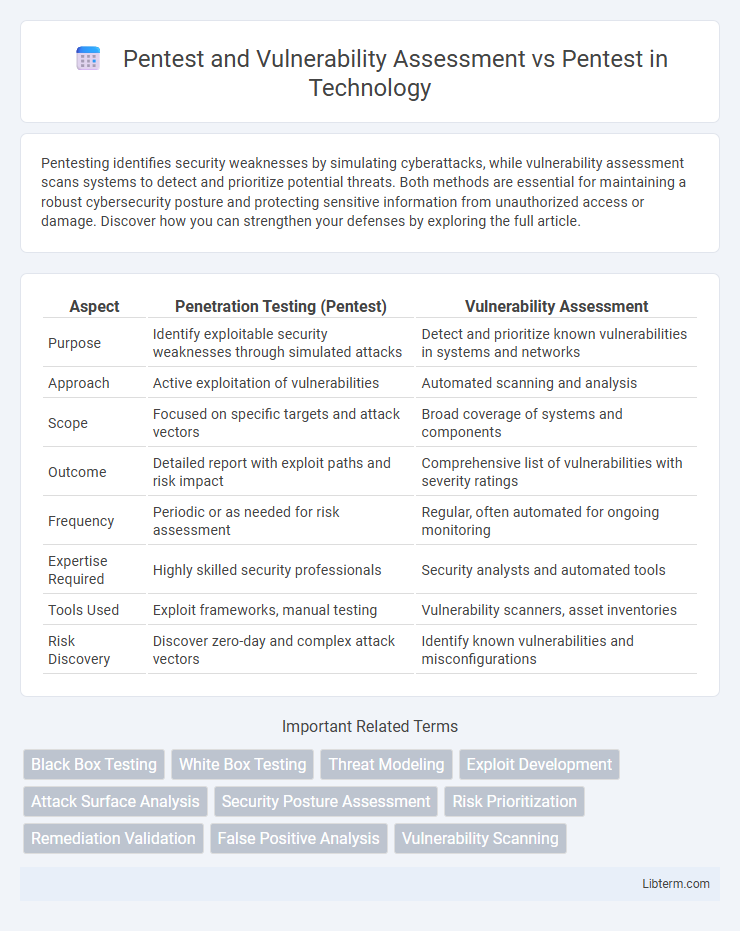
| Aspect | Penetration Testing (Pentest) | Vulnerability Assessment |
|---|---|---|
| Purpose | Identify exploitable security weaknesses through simulated attacks | Detect and prioritize known vulnerabilities in systems and networks |
| Approach | Active exploitation of vulnerabilities | Automated scanning and analysis |
| Scope | Focused on specific targets and attack vectors | Broad coverage of systems and components |
| Outcome | Detailed report with exploit paths and risk impact | Comprehensive list of vulnerabilities with severity ratings |
| Frequency | Periodic or as needed for risk assessment | Regular, often automated for ongoing monitoring |
| Expertise Required | Highly skilled security professionals | Security analysts and automated tools |
| Tools Used | Exploit frameworks, manual testing | Vulnerability scanners, asset inventories |
| Risk Discovery | Discover zero-day and complex attack vectors | Identify known vulnerabilities and misconfigurations |
Introduction to Pentesting and Vulnerability Assessments
Pentesting involves simulating cyberattacks on systems to identify security weaknesses through controlled exploitation, providing a real-world assessment of potential breaches. Vulnerability assessments systematically scan and analyze systems for known vulnerabilities without exploiting them, offering a prioritized list of security issues. Both processes are critical in identifying and mitigating security risks, with pentesting delivering deeper insights by demonstrating exploit paths, while vulnerability assessments provide a broader and faster evaluation of system weaknesses.
Defining Penetration Testing
Penetration testing, often referred to as pentesting, is a simulated cyberattack against a computer system, network, or web application to identify exploitable vulnerabilities. Unlike vulnerability assessments that primarily scan and report security weaknesses, penetration testing actively exploits these weaknesses to evaluate the real-world risk and impact. This hands-on approach provides a deeper understanding of an organization's security posture by demonstrating how attackers could breach defenses.
Exploring Vulnerability Assessment
Vulnerability assessment systematically identifies, quantifies, and prioritizes security weaknesses across network assets, providing continuous monitoring and risk insights to reduce exposure. Penetration testing simulates real-world attacks by exploiting vulnerabilities to evaluate security defenses, focusing on deep analysis during a specific point in time. Vulnerability assessment emphasizes broad, automated scanning and remediation guidance, complementing the targeted, exploit-driven approach of penetration tests.
Key Differences: Pentest vs Vulnerability Assessment
Penetration Testing (Pentest) involves simulating real-world cyberattacks to exploit vulnerabilities and assess the effectiveness of security defenses, providing detailed insights into potential attack paths and impacts. Vulnerability Assessment focuses on systematically identifying, classifying, and prioritizing security weaknesses across systems without exploiting them, offering a broad overview of the security posture. Key differences include Pentest's active exploitation and simulation of attacks versus Vulnerability Assessment's passive scanning and detection approach, with Pentests requiring higher expertise and delivering deeper contextual risk analysis.
Objectives of Pentest and Vulnerability Assessment
Pentest aims to simulate real-world attacks to identify exploitable vulnerabilities, emphasizing the effectiveness of existing security measures by demonstrating potential breaches. Vulnerability assessment systematically scans and catalogs security weaknesses, prioritizing risk identification and management without exploiting flaws. Understanding these distinct objectives helps organizations allocate resources effectively between proactive defense testing and broad vulnerability management.
Methodologies Compared: Pentesting vs Vulnerability Assessment
Penetration testing (pentest) employs simulated cyberattacks to exploit identified vulnerabilities, providing a real-world assessment of security posture, while vulnerability assessment scans and identifies known weaknesses without active exploitation. Pentest methodologies involve manual and automated techniques to mimic attacker behavior, often including social engineering and exploit development, whereas vulnerability assessments rely primarily on automated tools and databases for detection and prioritization. The depth of pentesting offers actionable insights into exploit feasibility and impact, contrasting with vulnerability assessment's broader but less intrusive scope focused on comprehensive flaw identification.
Scope and Depth of Security Evaluation
Pentest and Vulnerability Assessment differ significantly in scope and depth of security evaluation; vulnerability assessments provide a broad overview by identifying and quantifying security weaknesses across systems, networks, and applications, focusing on known vulnerabilities through automated tools. Penetration testing goes deeper, simulating real-world cyberattacks to exploit identified vulnerabilities, validating security controls, and uncovering complex business logic flaws that automated scans may miss. The targeted, in-depth nature of pentests delivers a more comprehensive understanding of an organization's security posture by demonstrating actual attack vectors and potential impacts.
Deliverables and Reporting in Both Approaches
Penetration Testing deliverables typically include detailed exploit walkthroughs, proof-of-concept demonstrations, and prioritized remediation steps highlighting active security breaches. Vulnerability Assessment reports emphasize comprehensive vulnerability inventories, risk rankings, and recommended fixes without exploit validation. Both approaches provide executive summaries, but Penetration Testing reports offer deeper insights into attack impact and system weaknesses through real-world exploitation evidence.
When to Choose Pentest, Vulnerability Assessment, or Both
Penetration testing (Pentest) is ideal when the goal is to simulate real-world cyberattacks to identify exploitable security weaknesses, particularly before launching new applications or after significant infrastructure changes. Vulnerability assessment is best suited for regular, automated scanning to discover and prioritize a wide array of security flaws and configuration issues across systems. Organizations often benefit from both approaches by using vulnerability assessments for continuous monitoring and pentests for in-depth, targeted security validation.
Best Practices for Integrating Both in Security Strategy
Integrating pentest and vulnerability assessment in a security strategy requires leveraging the complementary strengths of each: vulnerability assessments identify a broad range of weaknesses through automated scanning, while pentests simulate real-world attacks to exploit critical vulnerabilities. Best practices include scheduling regular vulnerability assessments to maintain continuous visibility of security posture and conducting targeted pentests on high-risk assets identified by these assessments. Combining both approaches enhances risk management by providing comprehensive insights from surface-level scanning to in-depth exploit validation.
Pentest and Vulnerability Assessment Infographic
 libterm.com
libterm.com