A proxy firewall acts as an intermediary between your device and the internet, filtering incoming and outgoing traffic to enhance security by preventing direct connections. It inspects data packets and blocks potentially harmful content, protecting your network from unauthorized access and cyber threats. Discover how implementing a proxy firewall can safeguard your digital environment by reading the rest of this article.
Table of Comparison
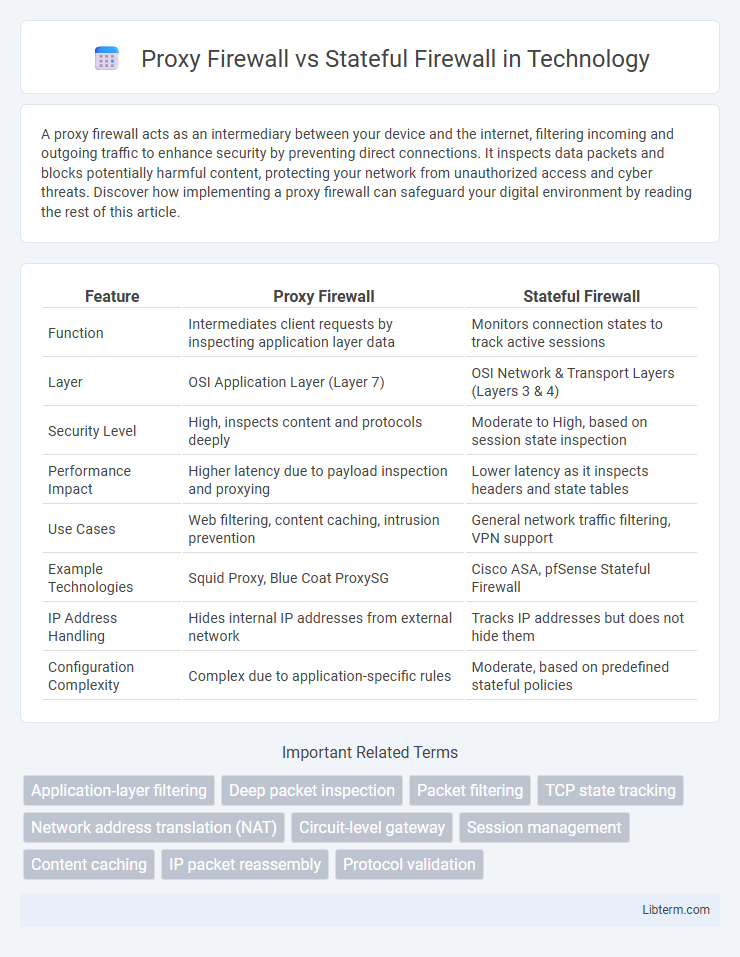
| Feature | Proxy Firewall | Stateful Firewall |
|---|---|---|
| Function | Intermediates client requests by inspecting application layer data | Monitors connection states to track active sessions |
| Layer | OSI Application Layer (Layer 7) | OSI Network & Transport Layers (Layers 3 & 4) |
| Security Level | High, inspects content and protocols deeply | Moderate to High, based on session state inspection |
| Performance Impact | Higher latency due to payload inspection and proxying | Lower latency as it inspects headers and state tables |
| Use Cases | Web filtering, content caching, intrusion prevention | General network traffic filtering, VPN support |
| Example Technologies | Squid Proxy, Blue Coat ProxySG | Cisco ASA, pfSense Stateful Firewall |
| IP Address Handling | Hides internal IP addresses from external network | Tracks IP addresses but does not hide them |
| Configuration Complexity | Complex due to application-specific rules | Moderate, based on predefined stateful policies |
Introduction to Firewalls: Purpose and Importance
Proxy firewalls and stateful firewalls serve critical roles in network security by filtering traffic to prevent unauthorized access. Proxy firewalls act as intermediaries, inspecting and validating requests at the application layer, enhancing security by masking internal addresses. Stateful firewalls track the state of active connections, allowing them to make dynamic decisions based on the context of network traffic, which improves efficiency and protection against intrusion attempts.
What is a Proxy Firewall?
A proxy firewall acts as an intermediary between end-users and the internet by intercepting all incoming and outgoing traffic to enforce security policies and hide the true network addresses. It inspects application layer data, enabling deep packet inspection for protocols like HTTP, FTP, and SMTP, which enhances protection against malware and unauthorized access. Unlike stateful firewalls that track connection states, proxy firewalls create a separate connection for each request, providing granular control and anonymity.
What is a Stateful Firewall?
A stateful firewall monitors the full state of active network connections by tracking and analyzing the state and context of packets, allowing it to make more informed filtering decisions based on connection history. Unlike a proxy firewall that acts as an intermediary between endpoints, a stateful firewall inspects traffic at the network layer, maintaining a state table for session information such as TCP handshake completion. This capability enables stateful firewalls to effectively block unauthorized access and prevent certain types of attacks by ensuring only legitimate packets belonging to established connections are allowed.
Key Features of Proxy Firewalls
Proxy firewalls operate at the application layer by intercepting and filtering incoming traffic between end-users and the internet, providing enhanced privacy and content filtering. They cache data to reduce bandwidth usage and improve response times, while hiding internal IP addresses to prevent direct exposure to potential threats. Unlike stateful firewalls, proxy firewalls perform deep packet inspection, enabling granular control over specific protocols such as HTTP, FTP, and SMTP for stronger security enforcement.
Key Features of Stateful Firewalls
Stateful firewalls monitor the state of active connections and make decisions based on the context of traffic, allowing them to efficiently track and filter packets within a session. Key features include packet inspection beyond headers, maintaining a state table to record connection status, and dynamic rule enforcement based on connection state. This enables stateful firewalls to provide enhanced security by recognizing legitimate traffic patterns and blocking unauthorized access without compromising performance.
Proxy Firewall vs Stateful Firewall: How They Work
Proxy firewalls operate by intercepting all incoming and outgoing traffic between devices and the internet, acting as an intermediary to filter requests based on application-layer protocols and content inspection. Stateful firewalls maintain a dynamic state table that tracks active connections and automatically allow or block packets based on the connection state, enabling inspection at the network and transport layers. Unlike stateful firewalls that focus on packet flows and connection states, proxy firewalls provide deeper inspection by handling traffic at the application level, offering enhanced security against unauthorized access and complex attacks.
Security Benefits of Proxy and Stateful Firewalls
Proxy firewalls enhance security by inspecting traffic at the application layer, effectively masking internal network addresses and blocking malicious payloads before they reach the network. Stateful firewalls maintain detailed state tables to monitor active connections, allowing them to detect and prevent unauthorized packets based on session context and traffic patterns. Both firewall types provide robust protection, with proxy firewalls excelling in application-level filtering and stateful firewalls offering dynamic packet inspection for comprehensive network security.
Performance and Latency Considerations
Proxy firewalls intercept and inspect entire packets at the application layer, providing robust security but introducing higher latency due to deep packet inspection and buffering. Stateful firewalls operate at the network and transport layers, tracking connection states with less overhead, resulting in better performance and lower latency for real-time traffic. For environments requiring high throughput and minimal delay, stateful firewalls are generally preferred, while proxy firewalls are suitable when security demands outweigh performance concerns.
Use Cases and Best Applications
Proxy firewalls excel in filtering and inspecting application-layer traffic, making them ideal for environments requiring deep packet inspection, such as web filtering, content caching, and enforcing user authentication. Stateful firewalls track the state of active connections and efficiently manage network traffic based on session context, making them suitable for high-throughput environments like enterprise perimeter security and VPN access control. Organizations often deploy proxy firewalls for detailed protocol analysis and stateful firewalls for scalable, low-latency network protection.
Choosing the Right Firewall for Your Network
Choosing the right firewall for your network depends on factors such as security requirements, network size, and performance needs. Proxy firewalls offer excellent application-layer filtering and anonymity by acting as intermediaries between clients and servers, making them ideal for environments requiring strong content inspection and user privacy. Stateful firewalls provide efficient packet filtering based on connection states, suitable for high-speed networks needing scalable, low-latency protection at the transport and network layers.
Proxy Firewall Infographic
 libterm.com
libterm.com