Brute force attack involves systematically trying every possible password or key combination to gain unauthorized access to a system or data. This method exploits weak security measures and can be mitigated by using strong, complex passwords and multi-factor authentication. Discover how to protect your digital assets from brute force attacks in the rest of this article.
Table of Comparison
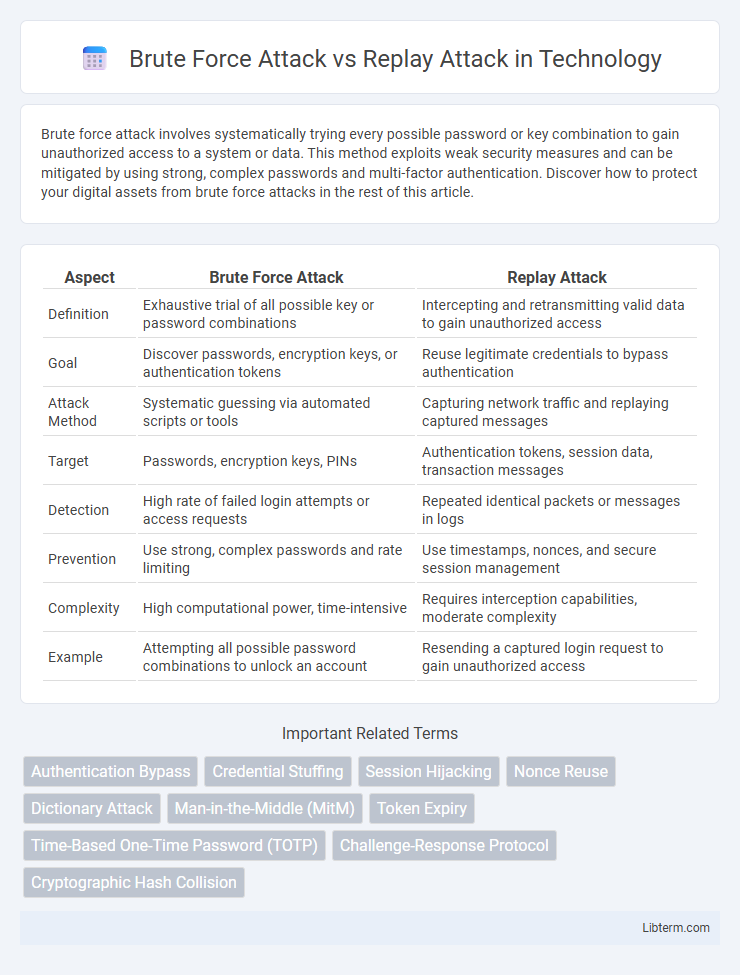
| Aspect | Brute Force Attack | Replay Attack |
|---|---|---|
| Definition | Exhaustive trial of all possible key or password combinations | Intercepting and retransmitting valid data to gain unauthorized access |
| Goal | Discover passwords, encryption keys, or authentication tokens | Reuse legitimate credentials to bypass authentication |
| Attack Method | Systematic guessing via automated scripts or tools | Capturing network traffic and replaying captured messages |
| Target | Passwords, encryption keys, PINs | Authentication tokens, session data, transaction messages |
| Detection | High rate of failed login attempts or access requests | Repeated identical packets or messages in logs |
| Prevention | Use strong, complex passwords and rate limiting | Use timestamps, nonces, and secure session management |
| Complexity | High computational power, time-intensive | Requires interception capabilities, moderate complexity |
| Example | Attempting all possible password combinations to unlock an account | Resending a captured login request to gain unauthorized access |
Introduction to Brute Force and Replay Attacks
Brute force attacks involve systematically trying every possible key or password combination until the correct one is found, exploiting weak credential security. Replay attacks intercept and retransmit valid data transmissions to deceive systems into unauthorized actions, targeting authentication and session protocols. Both techniques emphasize vulnerabilities in authentication mechanisms and require robust encryption and time-sensitive tokens to prevent exploitation.
Defining Brute Force Attacks
Brute Force Attacks involve systematically attempting every possible password or encryption key combination until the correct one is found, exploiting computational power to bypass security measures. These attacks rely heavily on the length and complexity of passwords, making weak or common passwords particularly vulnerable. Unlike Replay Attacks, which capture and reuse valid data transmissions, Brute Force Attacks generate new attempts and do not depend on intercepted communications.
Understanding Replay Attacks
Replay attacks involve intercepting and retransmitting valid data to gain unauthorized access or manipulate communications, often targeting authentication protocols. Unlike brute force attacks that exhaustively attempt passwords or keys, replay attacks exploit captured valid data packets without needing to decrypt or alter content. Effective prevention strategies include implementing nonce values, timestamps, and session tokens to ensure each authentication request is unique and cannot be reused.
Key Differences Between Brute Force and Replay Attacks
Brute force attacks exploit computational power to systematically guess credentials or encryption keys by trying every possible combination, while replay attacks intercept and retransmit valid data to gain unauthorized access without decrypting it. Brute force targets the password or key directly, focusing on cracking security through exhaustive trial, whereas replay attacks exploit the communication protocol by resending legitimate authentication data. The primary difference lies in brute force attacking cryptographic strength, while replay attacks manipulate transmission vulnerabilities without altering the original data.
Common Targets and Vulnerabilities
Brute force attacks commonly target authentication systems by exploiting weak or reused passwords, making login portals and encrypted data highly vulnerable. Replay attacks focus on intercepting and re-sending valid data transmissions, often targeting communication protocols and financial transaction systems that lack effective nonce or timestamp mechanisms. Both attack types exploit insufficient security controls, with brute force undermining credential strength and replay attacks exploiting the absence of message freshness verification.
Methods of Detection for Both Attacks
Brute force attack detection relies on monitoring abnormal login attempts, such as multiple failed authentication tries from a single IP address, and implementing rate limiting or account lockouts to prevent unauthorized access. Replay attack detection involves analyzing packet timings and validating unique session tokens or nonces to identify repetitive or duplicated messages within secure communication channels. Both methods benefit from real-time monitoring tools and anomaly detection algorithms to enhance security against these distinct cyber threats.
Prevention Strategies for Brute Force Attacks
Brute force attacks can be mitigated by implementing account lockout mechanisms after a defined number of failed login attempts, which prevents automated tools from continuously guessing passwords. Employing multi-factor authentication (MFA) significantly strengthens access security by requiring additional verification beyond just a password. Utilizing strong password policies combined with rate limiting and CAPTCHA challenges further reduces the risk of brute force attacks by limiting the ability to automate repeated login attempts.
Prevention Strategies for Replay Attacks
Replay attack prevention strategies include implementing timestamp validation, nonce usage, and session tokens to ensure message freshness and uniqueness. Secure cryptographic protocols like TLS and mutual authentication mechanisms help verify the legitimacy of communication participants. Network monitoring and anomaly detection systems also play a vital role in identifying and mitigating replay attempts.
Real-World Examples and Case Studies
Brute force attacks, like the 2012 LinkedIn breach where attackers cracked millions of weak passwords, exploit exhaustive trial-and-error methods to gain unauthorized access. Replay attacks, demonstrated by the 2010 Kavorka ATM fraud case, involve intercepting and retransmitting valid data to execute unauthorized transactions. These real-world incidents underscore the importance of strong password policies and the use of challenge-response authentication mechanisms to defend against such exploit techniques.
Conclusion: Enhancing Security Against Cyber Attacks
Brute force attacks exploit repeated attempts to guess passwords, while replay attacks capture and reuse valid authentication data, both posing significant cybersecurity risks. Implementing multi-factor authentication and employing robust encryption methods enhance defenses against these attack vectors. Continuous monitoring and adaptive security protocols further strengthen protection by identifying and mitigating suspicious activities in real-time.
Brute Force Attack Infographic
 libterm.com
libterm.com