Credential stuffing is a cyberattack method where hackers use stolen login credentials from one breach to gain unauthorized access to accounts on other platforms. This exploitation exploits people's tendency to reuse usernames and passwords across multiple sites, increasing the risk of widespread data breaches. Discover how to protect your online identity and prevent credential stuffing attacks in the rest of this article.
Table of Comparison
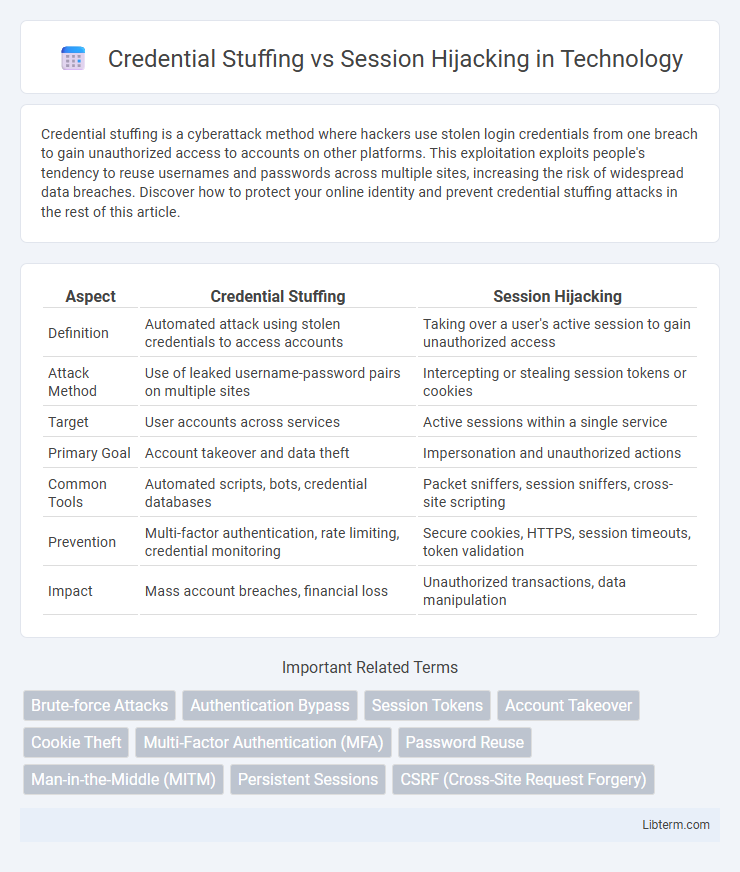
| Aspect | Credential Stuffing | Session Hijacking |
|---|---|---|
| Definition | Automated attack using stolen credentials to access accounts | Taking over a user's active session to gain unauthorized access |
| Attack Method | Use of leaked username-password pairs on multiple sites | Intercepting or stealing session tokens or cookies |
| Target | User accounts across services | Active sessions within a single service |
| Primary Goal | Account takeover and data theft | Impersonation and unauthorized actions |
| Common Tools | Automated scripts, bots, credential databases | Packet sniffers, session sniffers, cross-site scripting |
| Prevention | Multi-factor authentication, rate limiting, credential monitoring | Secure cookies, HTTPS, session timeouts, token validation |
| Impact | Mass account breaches, financial loss | Unauthorized transactions, data manipulation |
Introduction to Credential Stuffing and Session Hijacking
Credential stuffing involves attackers using automated tools to exploit large databases of breached usernames and passwords to gain unauthorized access to user accounts. Session hijacking is a cyberattack technique where an attacker intercepts or takes over a valid user session to steal information or impersonate the user. Both methods compromise account security but target different stages of the authentication and session management processes.
What is Credential Stuffing?
Credential stuffing is a cyberattack technique where attackers use automated tools to inject large volumes of stolen username and password combinations into login forms, exploiting reused credentials across multiple sites. This method relies heavily on data breaches exposing millions of login credentials, making it possible to gain unauthorized access to user accounts without guessing passwords. Unlike session hijacking, which targets active user sessions, credential stuffing focuses on initial access by validating stolen credentials against authentication systems.
Understanding Session Hijacking
Session hijacking involves cybercriminals stealing or predicting a valid user's session ID to gain unauthorized access to their online accounts without needing a username or password. Unlike credential stuffing, which relies on exploiting stolen login credentials across multiple sites, session hijacking targets active user sessions by intercepting cookies or session tokens during transmission. Understanding session hijacking is critical for securing web applications through measures like secure cookie attributes, encrypted connections (HTTPS), and timely session expiration.
Key Differences Between Credential Stuffing and Session Hijacking
Credential stuffing involves attackers using automated tools to inject stolen username and password pairs into login forms, exploiting reused credentials across multiple sites. Session hijacking targets active user sessions by stealing or intercepting session tokens, allowing attackers to bypass authentication without needing login credentials. The key difference lies in credential stuffing attacking the authentication process itself, while session hijacking exploits vulnerabilities in session management after authentication.
Attack Vectors and Techniques
Credential stuffing exploits large databases of stolen login credentials using automated scripts to gain unauthorized access to user accounts by leveraging reused passwords. Session hijacking involves intercepting active user sessions through techniques such as session fixation, cross-site scripting (XSS), or man-in-the-middle attacks to assume control over authenticated sessions. Both attack vectors target user authentication but differ in focus: credential stuffing attacks compromised credentials en masse, while session hijacking exploits vulnerabilities in session management and communication protocols.
Real-World Examples of Credential Stuffing
Credential stuffing involves attackers using leaked username and password combinations to gain unauthorized access to multiple accounts, as seen in the 2021 Twitch breach where over 125GB of data, including credentials, were exposed. Major companies like Microsoft and Sony have also been targeted by credential stuffing attacks, resulting in account takeovers and financial losses. This contrasts with session hijacking, which manipulates active user sessions rather than exploiting stolen credentials.
Notable Session Hijacking Incidents
Notable session hijacking incidents include the 2009 Twitter hack, where attackers exploited session tokens to take over user accounts and spread spam, and the 2011 PlayStation Network breach, which compromised millions of sessions, leading to prolonged outages and data theft. In contrast to credential stuffing, which relies on stolen username-password pairs, session hijacking targets active user sessions by intercepting or stealing session cookies, bypassing traditional login credentials. High-profile cases underscore the importance of securing session management protocols, such as implementing HTTPS, secure cookies, and frequent session expiration.
Identifying Signs of Each Attack
Credential stuffing attacks often manifest through numerous failed login attempts and unusual IP addresses attempting to access multiple accounts simultaneously, signaling automated bot activity. Session hijacking is identified by sudden changes in session behavior, such as unexpected geographic locations, simultaneous logins from different devices, or anomalous session token usage. Monitoring login patterns and session integrity through security analytics tools helps detect both attack types effectively.
Prevention and Mitigation Strategies
Credential stuffing prevention includes implementing multi-factor authentication (MFA), deploying rate limiting and IP blacklisting, and continuously monitoring for unusual login patterns using advanced threat detection systems. Session hijacking mitigation involves securing session cookies with HttpOnly and Secure flags, enforcing strict user session timeouts, and utilizing encrypted communication protocols such as TLS to safeguard data in transit. Both strategies emphasize proactive security measures, continuous monitoring, and user education to reduce vulnerabilities and enhance overall cybersecurity posture.
Conclusion: Protecting Against Credential Stuffing and Session Hijacking
Protecting against credential stuffing and session hijacking requires robust security measures, including multi-factor authentication (MFA) and continuous monitoring of login activities. Enforcing strong password policies and implementing anomaly detection systems help mitigate the risks of automated bot attacks and unauthorized session access. Regularly updating software and educating users on phishing prevention further strengthen defenses against these prevalent cyber threats.
Credential Stuffing Infographic
 libterm.com
libterm.com