Proxy servers act as intermediaries between your device and the internet, enhancing privacy by masking your IP address and enabling access to restricted content. They improve security by filtering malicious traffic and can boost browsing speed through caching frequently accessed websites. Explore the rest of the article to understand how proxy servers can optimize your online experience and which type suits your needs best.
Table of Comparison
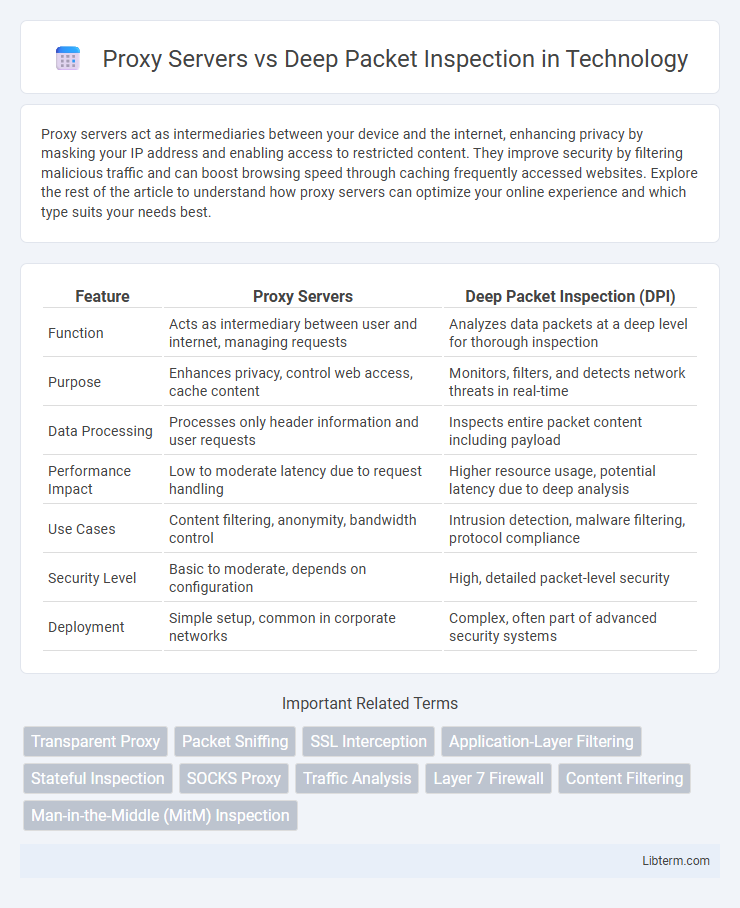
| Feature | Proxy Servers | Deep Packet Inspection (DPI) |
|---|---|---|
| Function | Acts as intermediary between user and internet, managing requests | Analyzes data packets at a deep level for thorough inspection |
| Purpose | Enhances privacy, control web access, cache content | Monitors, filters, and detects network threats in real-time |
| Data Processing | Processes only header information and user requests | Inspects entire packet content including payload |
| Performance Impact | Low to moderate latency due to request handling | Higher resource usage, potential latency due to deep analysis |
| Use Cases | Content filtering, anonymity, bandwidth control | Intrusion detection, malware filtering, protocol compliance |
| Security Level | Basic to moderate, depends on configuration | High, detailed packet-level security |
| Deployment | Simple setup, common in corporate networks | Complex, often part of advanced security systems |
Introduction to Proxy Servers and Deep Packet Inspection
Proxy servers act as intermediaries between users and the internet, routing requests to mask IP addresses and enhance privacy. Deep Packet Inspection (DPI) involves analyzing the data part of packets traversing a network to detect, filter, or log specific types of data for security or traffic management purposes. Both technologies serve critical roles in network security, with proxies focusing on anonymity and access control, while DPI provides granular traffic analysis and threat detection.
Core Functions of Proxy Servers
Proxy servers primarily function as intermediaries that forward client requests to target servers, enhancing privacy, security, and content filtering by masking IP addresses and controlling access. They cache frequently accessed web content to reduce bandwidth usage and improve response times for users. Unlike deep packet inspection, which examines data packets at a granular level for monitoring or filtering, proxy servers operate mainly by managing HTTP or HTTPS requests at the application layer.
Understanding Deep Packet Inspection Technology
Deep packet inspection (DPI) technology analyzes the data portion and header of packets passing through a network to identify, classify, and manage traffic based on protocol, content, and application. Unlike proxy servers that act as intermediaries by forwarding and caching requests, DPI inspects the actual payload of each packet for detailed traffic filtering, security, and data monitoring. DPI is essential for advanced network security measures such as intrusion detection, bandwidth management, and content filtering by enabling granular control over internet traffic at the packet level.
Key Differences Between Proxy Servers and DPI
Proxy servers act as intermediaries that route user requests through a separate network to mask IP addresses and cache content, enhancing privacy and performance. Deep Packet Inspection (DPI) analyzes the actual data within network packets to detect malware, enforce policies, or filter traffic at a granular level. Unlike proxy servers, which primarily manage traffic at the application layer, DPI operates at multiple layers of the OSI model, providing deeper inspection for security and traffic management.
Security Implications: Proxy vs DPI
Proxy servers enhance security by masking user IP addresses and filtering web traffic to block malicious sites, offering a layer of privacy and control over internet access. Deep Packet Inspection (DPI) provides granular visibility by analyzing packet contents, enabling detection of malware, intrusions, and policy violations at the application layer. While proxies primarily protect against external threats and maintain anonymity, DPI delivers comprehensive threat detection and network monitoring, but with potential privacy concerns due to its deep data inspection capabilities.
Privacy Considerations and User Anonymity
Proxy servers provide a level of privacy by masking user IP addresses and routing traffic through intermediary servers, but they can still log user activity and may not encrypt data, making anonymity partial. Deep Packet Inspection (DPI) analyzes the contents of data packets passing through a network, allowing for detailed monitoring and potential identification of users, which raises significant privacy concerns and reduces anonymity. Users seeking strong privacy protection should be aware that while proxies offer some obfuscation, DPI's intrusive scrutiny can compromise user anonymity unless combined with robust encryption methods like VPN or Tor.
Performance Impact and Network Latency
Proxy servers typically introduce moderate performance impact and slight network latency due to traffic rerouting and content caching processes. Deep Packet Inspection (DPI) often causes higher latency and increased CPU load because it analyzes packet payloads in real-time, leading to potential bottlenecks in high-throughput networks. Optimizing hardware acceleration and load balancing can mitigate DPI's performance degradation, whereas proxy servers benefit from efficient cache management to maintain low latency levels.
Use Cases: When to Use Proxy Servers
Proxy servers excel in scenarios requiring user privacy, content filtering, or bypassing geo-restrictions by masking IP addresses and caching web content. They are ideal for organizations enforcing access controls, enhancing performance, or monitoring employee internet usage without decrypting traffic. Proxy servers serve well in environments where speed and basic security suffice without the complexity of inspecting the entire packet payload as done in Deep Packet Inspection.
Use Cases: When to Use Deep Packet Inspection
Deep Packet Inspection (DPI) is essential for network security and traffic management when in-depth analysis of data packets is required to detect malware, prevent data leaks, or enforce application-level policies. Unlike proxy servers that primarily handle traffic routing and caching, DPI examines the actual content of packets in real-time, making it ideal for intrusion detection systems, monitoring encrypted traffic, and prioritizing critical applications. Use DPI in environments demanding granular visibility, such as enterprise networks, ISPs, and government agencies aiming to safeguard sensitive data and ensure regulatory compliance.
Choosing the Right Solution for Your Network
Proxy servers efficiently manage and control internet traffic by routing user requests and hiding IP addresses, offering basic security and privacy for network users. Deep Packet Inspection (DPI) analyzes the content of data packets at a granular level, enhancing threat detection, data filtering, and traffic management but requires significant processing power and compliance considerations. Selecting the right solution depends on network size, security needs, and performance requirements, with proxy servers suited for general web filtering and DPI ideal for environments requiring detailed traffic analysis and advanced threat prevention.
Proxy Servers Infographic
 libterm.com
libterm.com