SecOps integrates security practices into IT operations, enhancing threat detection and response efficiency while minimizing risks to your infrastructure. By fostering collaboration between security and operations teams, it ensures continuous monitoring, incident management, and compliance adherence. Discover how implementing SecOps can transform your organization's security posture throughout this article.
Table of Comparison
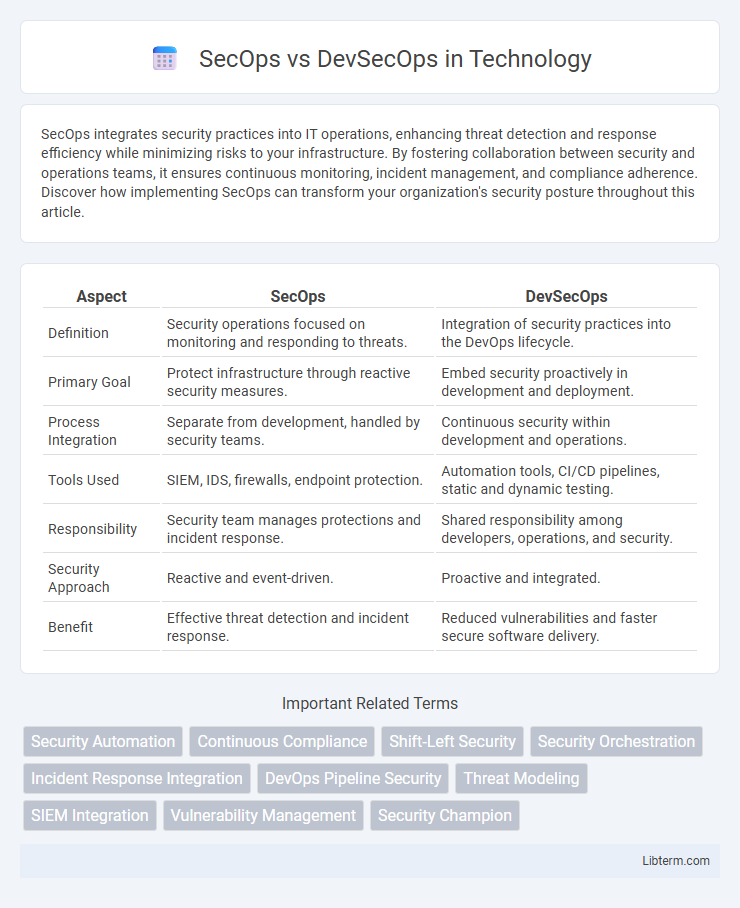
| Aspect | SecOps | DevSecOps |
|---|---|---|
| Definition | Security operations focused on monitoring and responding to threats. | Integration of security practices into the DevOps lifecycle. |
| Primary Goal | Protect infrastructure through reactive security measures. | Embed security proactively in development and deployment. |
| Process Integration | Separate from development, handled by security teams. | Continuous security within development and operations. |
| Tools Used | SIEM, IDS, firewalls, endpoint protection. | Automation tools, CI/CD pipelines, static and dynamic testing. |
| Responsibility | Security team manages protections and incident response. | Shared responsibility among developers, operations, and security. |
| Security Approach | Reactive and event-driven. | Proactive and integrated. |
| Benefit | Effective threat detection and incident response. | Reduced vulnerabilities and faster secure software delivery. |
Introduction to SecOps and DevSecOps
SecOps integrates security practices directly into IT operations to ensure continuous monitoring and rapid response to threats, prioritizing collaboration between security and operations teams. DevSecOps expands this approach by embedding security within the entire software development lifecycle, automating security checks in CI/CD pipelines to detect vulnerabilities early. Both methodologies aim to reduce risks and enhance system resilience, with DevSecOps emphasizing proactive security in agile environments and SecOps focusing on operational security enforcement.
Core Principles of SecOps
SecOps centers on integrating security measures directly into IT operations, emphasizing continuous monitoring, incident response, and vulnerability management to protect infrastructure and data integrity. Its core principles include collaboration between security and operations teams, automation of security processes, and real-time threat detection to minimize risks. SecOps aims to maintain system stability and compliance by embedding security practices throughout the operational lifecycle.
Core Principles of DevSecOps
DevSecOps integrates security practices directly into the development and operations lifecycle, emphasizing automation, continuous monitoring, and collaboration between development, security, and operations teams. Core principles of DevSecOps include embedding security from the design phase, implementing continuous security testing and compliance checks, and fostering a shared responsibility culture for security across all stakeholders. This approach contrasts with traditional SecOps by proactively addressing vulnerabilities early in the development process rather than reacting to threats after deployment.
Key Differences Between SecOps and DevSecOps
SecOps centers on integrating security teams with IT operations to streamline incident response and vulnerability management, emphasizing reactive protection. DevSecOps embeds security practices directly into the software development lifecycle, fostering proactive security through continuous integration and automated testing. The key difference lies in DevSecOps' shift-left approach that treats security as a shared responsibility from development to deployment, whereas SecOps focuses primarily on securing operational environments post-deployment.
Roles and Responsibilities in SecOps vs DevSecOps
SecOps roles primarily focus on monitoring, detecting, and responding to security threats within IT operations, emphasizing incident management, vulnerability assessments, and compliance enforcement. DevSecOps integrates security responsibilities directly into the development lifecycle, requiring developers, operations, and security teams to collaborate on secure coding practices, automated security testing, and continuous risk assessment. The shared responsibility model in DevSecOps contrasts with the traditionally siloed SecOps approach, promoting proactive security integration from design through deployment.
Security Integration in Traditional IT vs Modern DevOps
SecOps integrates security as a separate function within traditional IT environments, often leading to slower response times and isolated risk management processes. DevSecOps embeds security directly into the continuous integration and continuous delivery (CI/CD) pipelines of modern DevOps, enabling proactive vulnerability detection and automated compliance within development workflows. This shift enhances collaboration between development, operations, and security teams, ensuring security is a shared responsibility and reducing the risk of breaches during rapid software releases.
Benefits of Adopting DevSecOps Over SecOps
Adopting DevSecOps integrates security practices directly into the software development lifecycle, enabling faster identification and remediation of vulnerabilities compared to traditional SecOps, which operates primarily post-deployment. DevSecOps fosters enhanced collaboration between development, security, and operations teams, resulting in continuous security assessments and reduced risk of breaches. This proactive approach significantly improves compliance adherence and accelerates secure software delivery, driving higher overall organizational resilience.
Challenges and Limitations of SecOps and DevSecOps
SecOps faces challenges such as limited integration between development and security teams, resulting in slower threat detection and response times, and difficulty adapting to the rapid pace of software development. DevSecOps, while addressing these integration issues by embedding security into the CI/CD pipeline, encounters limitations in balancing security automation with development velocity, potentially causing deployment delays and false positives. Both methodologies require continuous collaboration and advanced tooling to effectively manage evolving cyber threats and maintain compliance without disrupting agile workflows.
Best Practices for Transitioning from SecOps to DevSecOps
Transitioning from SecOps to DevSecOps requires integrating security processes early in the development lifecycle through automated testing and continuous monitoring. Implementing Infrastructure as Code (IaC) and embedding security checkpoints within CI/CD pipelines enhance collaboration between development, operations, and security teams. Establishing a culture of shared responsibility and ongoing training ensures rapid detection and remediation of vulnerabilities, optimizing both security posture and development velocity.
Future Trends in Security Operations and DevSecOps
Future trends in SecOps highlight the integration of advanced AI and machine learning to enhance threat detection and automated response capabilities. DevSecOps is evolving toward embedding continuous security practices directly into the CI/CD pipeline using Infrastructure as Code (IaC) and automated compliance checks. Both approaches emphasize collaboration between development, security, and operations teams to accelerate secure software delivery and adapt to increasingly sophisticated cyber threats.
SecOps Infographic
 libterm.com
libterm.com