Hashing transforms data into fixed-size values called hash codes, enabling efficient data retrieval and verification in databases and cybersecurity. Understanding the mechanics of hashing algorithms can optimize your data integrity and security measures effectively. Explore the rest of this article to uncover how hashing enhances system performance and protects your digital assets.
Table of Comparison
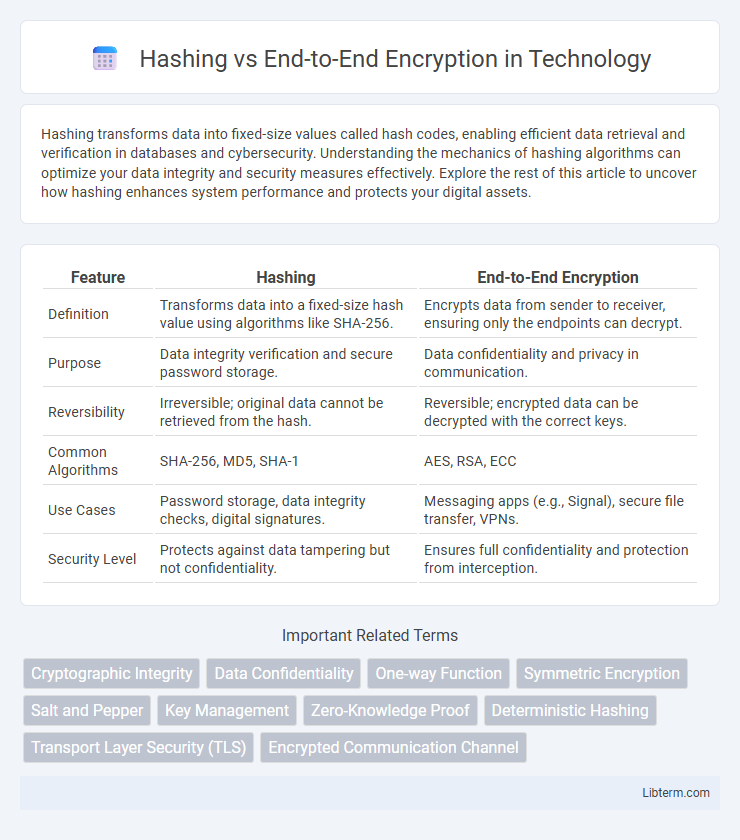
| Feature | Hashing | End-to-End Encryption |
|---|---|---|
| Definition | Transforms data into a fixed-size hash value using algorithms like SHA-256. | Encrypts data from sender to receiver, ensuring only the endpoints can decrypt. |
| Purpose | Data integrity verification and secure password storage. | Data confidentiality and privacy in communication. |
| Reversibility | Irreversible; original data cannot be retrieved from the hash. | Reversible; encrypted data can be decrypted with the correct keys. |
| Common Algorithms | SHA-256, MD5, SHA-1 | AES, RSA, ECC |
| Use Cases | Password storage, data integrity checks, digital signatures. | Messaging apps (e.g., Signal), secure file transfer, VPNs. |
| Security Level | Protects against data tampering but not confidentiality. | Ensures full confidentiality and protection from interception. |
Introduction to Hashing and End-to-End Encryption
Hashing converts data into a fixed-size string of characters, typically a hash code, used to verify data integrity without revealing the original content. End-to-end encryption secures communication by encrypting data from the sender directly to the receiver, ensuring only the intended recipient can decrypt and read the message. Both methods enhance security but serve different purposes: hashing for data verification and end-to-end encryption for confidential communication.
Core Concepts: What is Hashing?
Hashing is a cryptographic process that transforms input data of arbitrary size into a fixed-length string of characters, typically a hash value, using a hash function. This technique ensures data integrity by producing a unique fingerprint for each input, making it practically impossible to reverse-engineer the original data from the hash. Hashing is commonly used in password storage, data verification, and digital signatures due to its deterministic and collision-resistant properties.
Core Concepts: What is End-to-End Encryption?
End-to-End Encryption (E2EE) is a security mechanism that ensures only the communicating users can read the messages by encrypting data on the sender's device and decrypting it solely on the recipient's device, preventing intermediaries from accessing the content. Unlike hashing, which converts data into a fixed-size string for verification and integrity purposes, E2EE maintains data confidentiality by using encryption keys shared exclusively between the sender and receiver. This core concept guarantees privacy in messaging, email, and file sharing applications by eliminating vulnerabilities in transit or server storage.
Purpose and Applications of Hashing
Hashing transforms data into a fixed-size string of characters, primarily used for verifying data integrity and ensuring secure password storage. Unlike End-to-End Encryption, which protects data confidentiality during transmission, hashing is vital for quick data retrieval and authentication processes in systems like blockchain and digital signatures. Common applications of hashing include password hashing algorithms (e.g., bcrypt, SHA-256) and message authentication codes (MACs) that prevent data tampering.
Purpose and Applications of End-to-End Encryption
End-to-end encryption (E2EE) ensures that only communicating users can read the messages, safeguarding data from interception or unauthorized access during transmission. It is widely applied in secure messaging platforms like Signal and WhatsApp, protecting privacy in personal and business communications by encrypting data from sender to recipient. Unlike hashing, which transforms data into fixed-length representations for integrity verification or indexing, E2EE preserves the confidentiality and integrity of the original data throughout its transit.
Key Differences: Hashing vs End-to-End Encryption
Hashing transforms data into a fixed-size string of characters, which is irreversible and used primarily for data integrity verification, while end-to-end encryption ensures data confidentiality by encrypting messages so only the sender and recipient can decode them. Hashing does not require a key and outputs a unique hash value for given input, whereas end-to-end encryption relies on cryptographic keys exchanged securely between communicating parties. Key differences include the purpose, reversibility, and use cases: hashing verifies data authenticity without revealing original content, whereas end-to-end encryption protects message content from interception during transmission.
Security Implications and Threat Models
Hashing transforms data into a fixed-size string, ensuring data integrity by detecting alterations but cannot be reversed to reveal original content, making it vulnerable to preimage and collision attacks if weak algorithms are used. End-to-end encryption (E2EE) secures communication by encrypting data so only the sender and recipient can access it, protecting against interception, eavesdropping, and middleman attacks. Threat models for hashing include collision resistance failures exploited by attackers to forge data, while E2EE addresses threats from network adversaries but requires robust key management to prevent compromise by insider threats or endpoint malware.
Use Cases: Hashing in Digital Security
Hashing is crucial in digital security for verifying data integrity, storing passwords securely, and ensuring tamper-proof transmission of messages by generating fixed-length hash values from variable input data. End-to-end encryption is primarily used for securing communication channels by encrypting messages so only the sender and receiver can decrypt the content, protecting confidentiality during data transfer. Hashing is widely employed in password management systems, blockchain transactions, and digital signatures, where verification rather than confidentiality is the main objective.
Use Cases: End-to-End Encryption in Communication
End-to-end encryption (E2EE) is essential for secure communication channels such as messaging apps, video calls, and email, ensuring that only the sender and recipient can access the content. Unlike hashing, which is primarily used for data integrity and verification, E2EE protects the confidentiality of data in transit by encrypting messages with keys that are never exposed to intermediaries. Popular platforms like Signal and WhatsApp implement E2EE to prevent eavesdropping, making it crucial for privacy-sensitive communications and compliance with data protection regulations.
Choosing the Right Technique for Your Data Security Needs
Selecting between hashing and end-to-end encryption depends on your data security objectives; hashing is ideal for verifying data integrity and securely storing passwords due to its one-way function. End-to-end encryption protects data confidentiality during transmission by ensuring only authorized parties can decrypt the information. Understanding specific use cases, such as authentication versus secure communication, guides the optimal choice for safeguarding sensitive data effectively.
Hashing Infographic
 libterm.com
libterm.com