A Demilitarized Zone (DMZ) serves as a neutral buffer area between two or more military forces to prevent accidental or intentional conflict, often enforced by international agreements. In network security, a DMZ acts as a separate subnetwork that exposes external-facing services while protecting the internal network from potential cyber threats. Explore the rest of the article to understand how implementing a DMZ can enhance your security infrastructure.
Table of Comparison
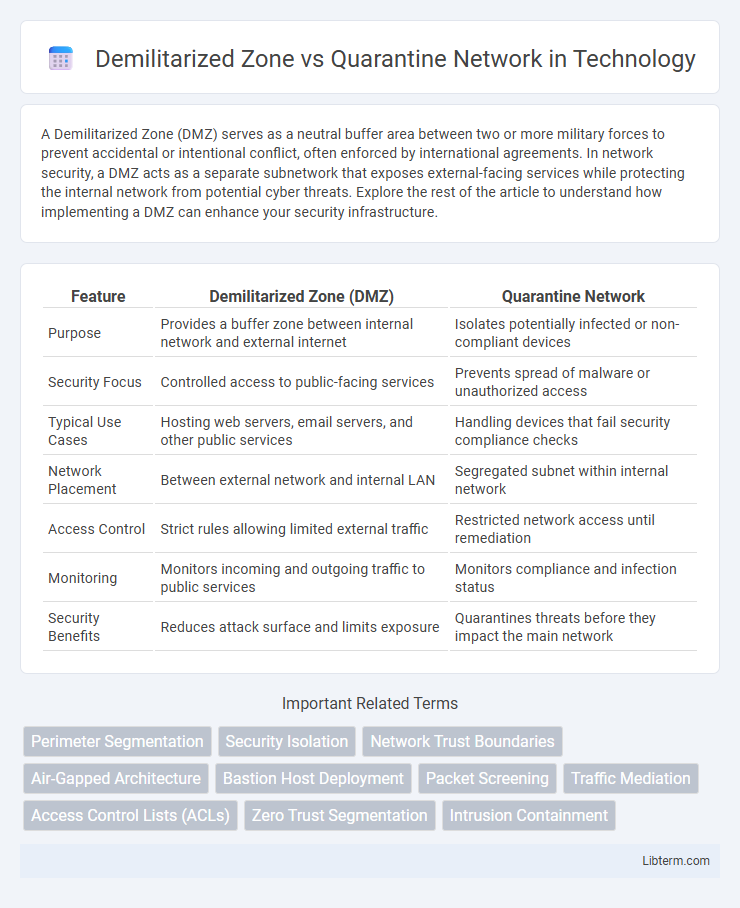
| Feature | Demilitarized Zone (DMZ) | Quarantine Network |
|---|---|---|
| Purpose | Provides a buffer zone between internal network and external internet | Isolates potentially infected or non-compliant devices |
| Security Focus | Controlled access to public-facing services | Prevents spread of malware or unauthorized access |
| Typical Use Cases | Hosting web servers, email servers, and other public services | Handling devices that fail security compliance checks |
| Network Placement | Between external network and internal LAN | Segregated subnet within internal network |
| Access Control | Strict rules allowing limited external traffic | Restricted network access until remediation |
| Monitoring | Monitors incoming and outgoing traffic to public services | Monitors compliance and infection status |
| Security Benefits | Reduces attack surface and limits exposure | Quarantines threats before they impact the main network |
Introduction to Demilitarized Zones (DMZ) and Quarantine Networks
A Demilitarized Zone (DMZ) is a network segment that acts as a buffer zone between an organization's internal network and untrusted external networks, typically the internet, designed to host public-facing services while minimizing security risks. A Quarantine Network isolates potentially compromised or non-compliant devices to prevent threats from spreading within the main internal network, often used during endpoint verification or malware remediation. Both DMZs and Quarantine Networks enhance security posture by segmenting traffic according to trust levels, but they serve different purposes: DMZs protect external-facing systems, whereas Quarantine Networks contain and assess risky internal devices.
Defining Demilitarized Zone (DMZ) in Network Security
A Demilitarized Zone (DMZ) in network security is a physical or logical subnetwork that separates an internal local area network (LAN) from untrusted external networks, typically the internet, to add an extra layer of protection. It hosts external-facing services such as web, email, and DNS servers, allowing public access while safeguarding the internal network from direct exposure. The DMZ uses firewalls and access control rules to tightly control traffic between the external network, DMZ, and internal network.
Understanding Quarantine Network Architecture
Quarantine Network architecture isolates suspicious or compromised devices by restricting their access to critical network resources, thereby preventing potential threats from spreading. It employs segmentation techniques such as VLANs or firewalls to control traffic flow and enforce strict access policies based on device health checks. Understanding Quarantine Network design is essential for enhancing cybersecurity posture by minimizing lateral movement of malware within enterprise environments.
Key Security Objectives of DMZ vs. Quarantine Network
A Demilitarized Zone (DMZ) primarily aims to expose external-facing services to the internet while protecting the internal network from unauthorized access, ensuring both security and controlled access. A Quarantine Network focuses on isolating potentially compromised or non-compliant devices to prevent the spread of malware and enforce security policy compliance before granting access to the main network. The key security objective of a DMZ is segmentation and controlled exposure of services, whereas a Quarantine Network's objective is containment and remediation of threats within the network.
Core Components and Topologies Compared
A Demilitarized Zone (DMZ) in network security typically comprises perimeter firewalls, intrusion detection systems (IDS), and proxy servers arranged in a three-tier topology to isolate external services from internal networks. In contrast, a Quarantine Network focuses on isolating compromised or untrusted devices using network access control (NAC), VLAN segmentation, and endpoint security solutions within an internal segmentation topology. While DMZs prioritize controlled exposure of public-facing servers, Quarantine Networks enable dynamic containment and remediation of threats through strict internal access restrictions.
Typical Use Cases for DMZ and Quarantine Network
A Demilitarized Zone (DMZ) typically hosts public-facing services such as web servers, email servers, and DNS servers to provide controlled external access while protecting the internal network from direct exposure. Quarantine networks are primarily used to isolate and contain potentially compromised or non-compliant devices, preventing them from accessing critical resources until they meet security policies. Organizations employ DMZs to enhance security for internet-facing applications, whereas quarantine networks support endpoint health enforcement and malware containment during network access control processes.
Threat Mitigation: DMZ vs. Quarantine Strategies
Demilitarized Zone (DMZ) and Quarantine Network are pivotal in threat mitigation, where DMZ establishes a buffer zone separating untrusted external networks from secure internal systems, limiting attackers' lateral movement. Quarantine Networks isolate suspicious devices or compromised endpoints immediately upon detection to prevent the spread of malware or unauthorized access within the corporate environment. Deploying both strategies enhances overall cybersecurity posture by controlling exposure points and enforcing strict containment measures against threats.
Advantages and Limitations of Each Approach
A Demilitarized Zone (DMZ) offers enhanced security by isolating external-facing services from the internal network, reducing the risk of breaches spreading internally, but it requires complex configuration and maintenance. A Quarantine Network effectively contains potentially infected or untrusted devices, preventing lateral movement of threats within the main network, though it may disrupt business operations and requires robust monitoring to manage quarantined assets. Both approaches serve distinct security needs: DMZs focus on controlled exposure to external users, while quarantine networks emphasize containment and remediation of internal threats.
Implementation Best Practices
Implementing a Demilitarized Zone (DMZ) requires strict segmentation between external and internal networks using firewalls to control traffic and prevent unauthorized access effectively. Best practices for a Quarantine Network include isolating infected or suspicious devices with limited network permissions until they are verified safe, reducing the risk of spreading malware within the corporate environment. Both strategies demand continuous monitoring, timely patches, and adherence to security policies to maintain robust perimeter defense and minimize vulnerabilities.
Choosing Between DMZ and Quarantine Network for Your Organization
Choosing between a Demilitarized Zone (DMZ) and a Quarantine Network depends on your organization's security priorities and network architecture. A DMZ provides a buffer zone that isolates external-facing services from the internal network, enhancing protection against external threats while allowing controlled access. In contrast, a Quarantine Network is designed to isolate suspicious or compromised devices for containment and remediation, making it essential for organizations focusing on endpoint security and threat mitigation.
Demilitarized Zone Infographic
 libterm.com
libterm.com