Cross-Site Request Forgery (CSRF) is a web security vulnerability that tricks users into performing unwanted actions on a trusted website where they are authenticated. Attackers exploit this by sending unauthorized commands from a user's browser, potentially compromising account security and data integrity. Explore the article to learn how to protect your applications from CSRF attacks effectively.
Table of Comparison
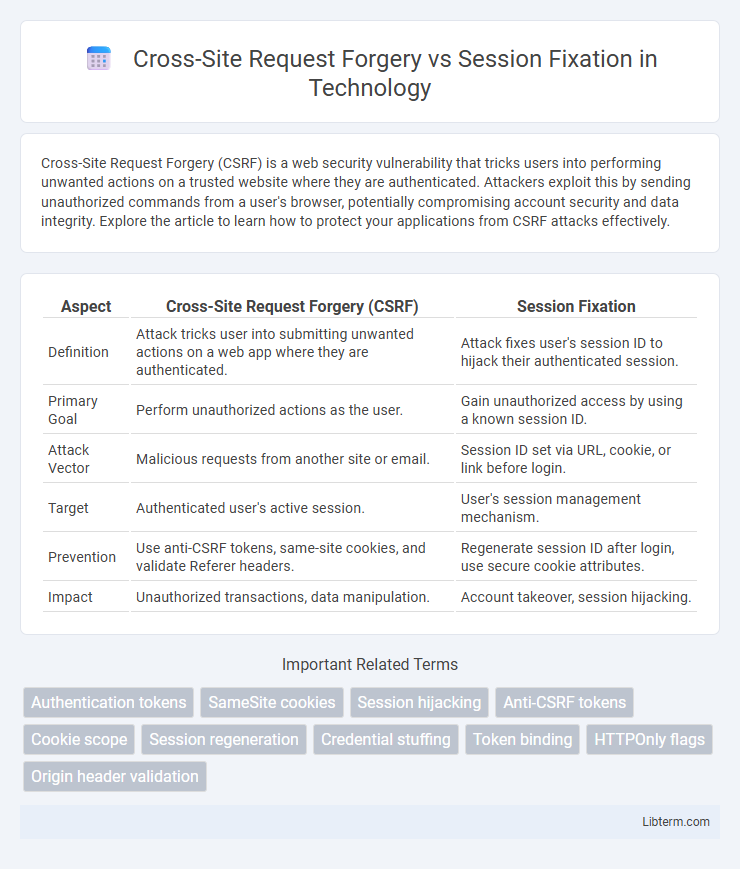
| Aspect | Cross-Site Request Forgery (CSRF) | Session Fixation |
|---|---|---|
| Definition | Attack tricks user into submitting unwanted actions on a web app where they are authenticated. | Attack fixes user's session ID to hijack their authenticated session. |
| Primary Goal | Perform unauthorized actions as the user. | Gain unauthorized access by using a known session ID. |
| Attack Vector | Malicious requests from another site or email. | Session ID set via URL, cookie, or link before login. |
| Target | Authenticated user's active session. | User's session management mechanism. |
| Prevention | Use anti-CSRF tokens, same-site cookies, and validate Referer headers. | Regenerate session ID after login, use secure cookie attributes. |
| Impact | Unauthorized transactions, data manipulation. | Account takeover, session hijacking. |
Introduction to Web Security Threats
Cross-Site Request Forgery (CSRF) exploits the trust a web application has in a user's browser by tricking the user into submitting unauthorized requests, potentially leading to unintended actions like data modification or fund transfers. Session Fixation attacks target user session identifiers by forcing a victim to use a known session ID, allowing attackers to hijack authenticated sessions and gain unauthorized access. Understanding these critical web security threats is essential for implementing robust authentication and session management mechanisms to protect web applications from exploitation.
What is Cross-Site Request Forgery (CSRF)?
Cross-Site Request Forgery (CSRF) is a web security vulnerability that tricks a user's browser into executing unwanted actions on a trusted site where they are authenticated. Attackers exploit this by crafting malicious requests that leverage the user's active session credentials without their knowledge. This differs from Session Fixation, which involves an attacker setting or manipulating a valid session ID to gain unauthorized access.
Understanding Session Fixation Attacks
Session Fixation attacks manipulate a user's session identifier to gain unauthorized access by forcing the victim to use a known session ID, which the attacker can then exploit. Unlike Cross-Site Request Forgery (CSRF), which tricks users into submitting unauthorized requests, Session Fixation targets the session management system to hijack active sessions. Understanding the mechanics of session handling in web applications, such as session ID generation and regeneration, is crucial to preventing Session Fixation vulnerabilities.
How CSRF Works: Attack Vectors
Cross-Site Request Forgery (CSRF) exploits a user's authenticated session by sending unauthorized commands from the user's browser to a web application, leveraging the victim's active login credentials. Common attack vectors include malicious links or embedded forms in emails, social media posts, or external websites that automatically send forged requests when visited. Unlike Session Fixation, which manipulates session identifiers, CSRF targets actions within an established session by deceiving the user into unknowingly initiating harmful operations.
Mechanisms Behind Session Fixation
Session fixation exploits vulnerabilities by forcing a user's session ID to a known value, enabling an attacker to hijack the session once the user logs in using the fixed ID. This attack manipulates session identifiers through URL parameters, cookies, or hidden form fields before authentication occurs, bypassing the usual session renewal processes. Preventing session fixation requires regenerating session identifiers upon authentication and enforcing secure cookie attributes to protect session integrity.
Key Differences Between CSRF and Session Fixation
Cross-Site Request Forgery (CSRF) exploits the trust a web application has in a user's browser by tricking authenticated users into submitting unauthorized requests, whereas Session Fixation targets the session identifier itself by forcing a user to use a known session ID, enabling attackers to hijack the session. CSRF attacks rely on the victim's active session and the lack of proper anti-CSRF tokens, while Session Fixation attacks exploit vulnerability in session ID management, often due to failure to regenerate session IDs after login. The key difference lies in CSRF manipulating user actions unknowingly, and Session Fixation compromising the session token, both requiring different mitigation strategies such as anti-CSRF tokens for CSRF and session ID regeneration for Session Fixation.
Real-World Examples of CSRF and Session Fixation
Real-world examples of Cross-Site Request Forgery (CSRF) include the 2007 Twitter attack where attackers exploited CSRF vulnerabilities to post unauthorized tweets from victims' accounts. Session Fixation incidents have been observed in e-commerce platforms, where attackers fixate a session ID to hijack user sessions during login, such as the vulnerability reported in early versions of phpBB forums. Both attack types highlight the critical need for proper session management and anti-CSRF tokens in web applications to prevent unauthorized actions and session hijacking.
Prevention Techniques for CSRF
Cross-Site Request Forgery (CSRF) prevention techniques primarily involve the implementation of anti-CSRF tokens, which are unique, unpredictable values included in each authenticated user's request to verify its legitimacy. Other effective measures include the use of SameSite cookies to restrict cross-origin requests and requiring re-authentication for sensitive operations. Ensuring proper validation of the HTTP Referer header and employing Content Security Policy (CSP) headers further mitigate CSRF risks by confirming request origins.
Mitigation Strategies for Session Fixation
Session Fixation mitigation strategies focus on regenerating session IDs after user authentication to prevent attackers from exploiting fixed session identifiers. Implementing secure cookie attributes such as HttpOnly, Secure, and SameSite restricts cookie exposure and unauthorized access. Enforcing strict session expiration and invalidating old sessions further reduces the risk of session hijacking and fixation attacks.
Best Practices for Securing Web Applications Against CSRF and Session Fixation
Implement strict anti-CSRF tokens in web forms to ensure requests are legitimate and originate from authenticated users, while enforcing same-site cookie attributes to prevent cross-origin requests. Employ secure session management by regenerating session IDs upon authentication and invalidating old sessions to mitigate session fixation risks. Use HTTPS for all communications, implement security headers like Content Security Policy (CSP), and regularly audit authentication flows to identify and fix vulnerabilities.
Cross-Site Request Forgery Infographic
 libterm.com
libterm.com