Credential stuffing exploits leaked username and password combinations to gain unauthorized access to your accounts by automating login attempts across multiple websites. This cyberattack targets repetitive password reuse, making it crucial to implement strong, unique credentials and enable multi-factor authentication. Discover effective strategies to protect your online identity from credential stuffing by reading the full article.
Table of Comparison
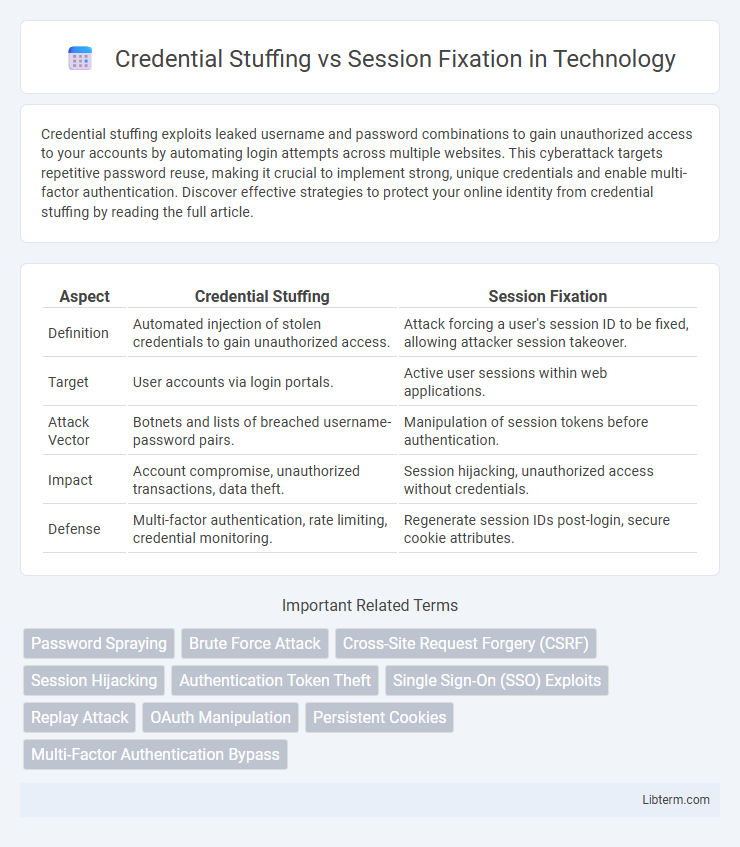
| Aspect | Credential Stuffing | Session Fixation |
|---|---|---|
| Definition | Automated injection of stolen credentials to gain unauthorized access. | Attack forcing a user's session ID to be fixed, allowing attacker session takeover. |
| Target | User accounts via login portals. | Active user sessions within web applications. |
| Attack Vector | Botnets and lists of breached username-password pairs. | Manipulation of session tokens before authentication. |
| Impact | Account compromise, unauthorized transactions, data theft. | Session hijacking, unauthorized access without credentials. |
| Defense | Multi-factor authentication, rate limiting, credential monitoring. | Regenerate session IDs post-login, secure cookie attributes. |
Understanding Credential Stuffing
Credential stuffing is a cyberattack technique where attackers use automated scripts to try large volumes of stolen username and password combinations across multiple websites to gain unauthorized access. This method exploits reused credentials from previous data breaches, allowing attackers to bypass traditional authentication mechanisms without needing to crack passwords. Understanding credential stuffing involves recognizing the importance of multi-factor authentication and proactive monitoring to prevent account takeover and data leakage.
What Is Session Fixation?
Session fixation is a web security vulnerability where an attacker tricks a user into using a specific session ID, allowing the attacker to hijack the user's authenticated session. Unlike credential stuffing, which exploits reused or stolen login credentials, session fixation targets the session management process by fixing the session ID before authentication occurs. Effective mitigation includes regenerating session IDs upon login and implementing strict session expiration policies to prevent unauthorized access.
Key Differences Between Credential Stuffing and Session Fixation
Credential stuffing exploits automated login attempts using stolen credentials to gain unauthorized access, whereas session fixation attacks manipulate a user's session ID to hijack an active session. Credential stuffing targets authentication processes with large-scale credential databases, while session fixation bypasses authentication by exploiting session management vulnerabilities. The key difference lies in the attack vector: credential stuffing compromises user credentials, whereas session fixation leverages session ID control to maintain unauthorized access.
How Credential Stuffing Attacks Work
Credential stuffing attacks leverage automated tools to rapidly test stolen usernames and passwords across multiple websites, exploiting users who reuse credentials. Attackers use lists of leaked credentials from previous data breaches to attempt unauthorized logins, bypassing security by mimicking legitimate user behavior. This technique overwhelms authentication systems and often leads to account takeover, financial fraud, and compromised personal data.
The Mechanics of Session Fixation Attacks
Session fixation attacks manipulate a victim's session ID by forcing them to use a predefined session identifier, allowing attackers to hijack the authenticated session once the victim logs in. This is achieved by tricking the victim into using the attacker's session ID through methods such as URL parameters, embedded links, or HTTP headers. The attacker gains unauthorized access by exploiting the session management mechanism that fails to regenerate session IDs post-authentication.
Common Targets and Vulnerabilities
Credential stuffing primarily targets web applications with poor password management and reused credentials, exploiting vulnerabilities in authentication systems to gain unauthorized access. Session fixation attacks focus on session management flaws, especially in web sessions where attackers fix a user's session ID to hijack active sessions. Both attack vectors commonly exploit weak security controls such as insufficient input validation, lack of multi-factor authentication, and improper session expiration settings.
Real-World Examples and Case Studies
Credential stuffing attacks exploited stolen login credentials in 2020 to breach several major retail websites, causing millions in losses and compromised user accounts. Session fixation vulnerabilities were highlighted in a 2017 banking case where attackers fixed session IDs to hijack authenticated sessions, leading to unauthorized fund transfers. These real-world incidents demonstrate the critical need for robust multi-factor authentication and secure session management practices to mitigate such threats.
Prevention Strategies for Credential Stuffing
Implement strong multi-factor authentication (MFA) to reduce the effectiveness of stolen credentials used in credential stuffing attacks. Employ IP blacklisting, rate limiting, and anomaly detection systems to identify and block suspicious login attempts rapidly. Regularly update and enforce password policies, including monitoring leaked credential databases, to ensure compromised passwords are promptly invalidated.
Protecting Against Session Fixation
Session fixation attacks manipulate user sessions by forcing a valid session ID on a victim, allowing attackers unauthorized access. Protecting against session fixation involves regenerating session IDs after user authentication and implementing secure flags like HttpOnly and Secure for cookies. Regularly invalidating sessions on logout and using robust session management frameworks significantly reduce vulnerability to such exploits.
Choosing the Right Security Solutions
Credential stuffing attacks exploit stolen username-password pairs to gain unauthorized access, while session fixation targets a user's session ID to hijack active sessions. Choosing the right security solutions involves implementing multi-factor authentication, deploying robust bot detection mechanisms, and using secure cookie attributes like HttpOnly and SameSite to prevent session fixation. Integrating real-time monitoring and anomaly detection further strengthens defenses against both credential stuffing and session fixation threats.
Credential Stuffing Infographic
 libterm.com
libterm.com