Session hijacking exploits vulnerabilities in web sessions to gain unauthorized access by stealing or manipulating session tokens. This attack can lead to identity theft, data breaches, and compromised user accounts, severely impacting security and privacy. Explore the rest of the article to learn how to protect your online sessions from hijacking threats.
Table of Comparison
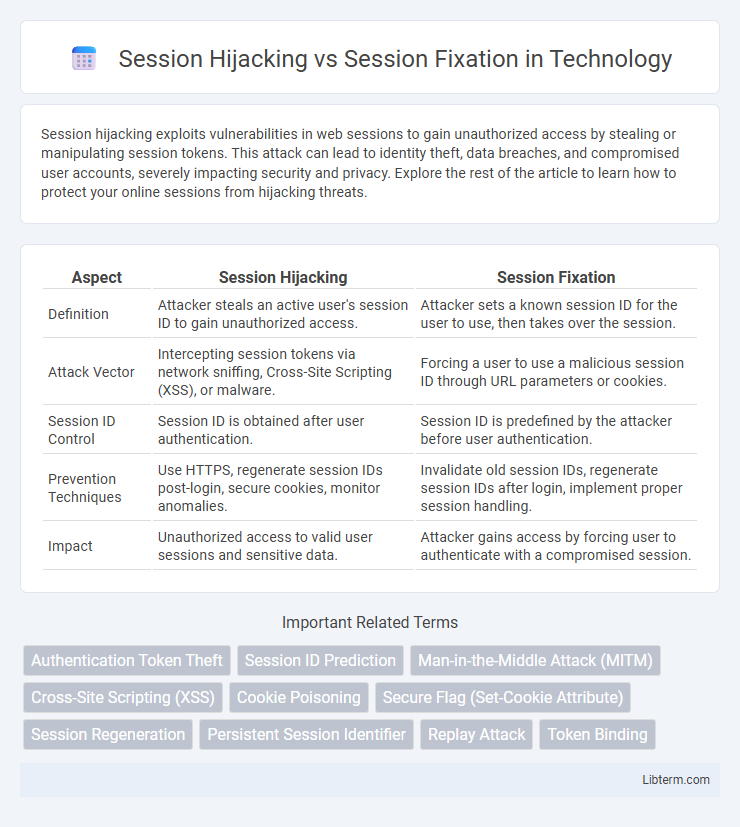
| Aspect | Session Hijacking | Session Fixation |
|---|---|---|
| Definition | Attacker steals an active user's session ID to gain unauthorized access. | Attacker sets a known session ID for the user to use, then takes over the session. |
| Attack Vector | Intercepting session tokens via network sniffing, Cross-Site Scripting (XSS), or malware. | Forcing a user to use a malicious session ID through URL parameters or cookies. |
| Session ID Control | Session ID is obtained after user authentication. | Session ID is predefined by the attacker before user authentication. |
| Prevention Techniques | Use HTTPS, regenerate session IDs post-login, secure cookies, monitor anomalies. | Invalidate old session IDs, regenerate session IDs after login, implement proper session handling. |
| Impact | Unauthorized access to valid user sessions and sensitive data. | Attacker gains access by forcing user to authenticate with a compromised session. |
Understanding Session Management in Web Security
Session hijacking exploits vulnerabilities by intercepting or stealing an active session ID to gain unauthorized access, whereas session fixation involves tricking a user into authenticating with a predefined session ID controlled by the attacker. Effective session management in web security requires regenerating session IDs after login, setting secure cookie attributes, and implementing strict timeout policies to prevent session-related attacks. Understanding these mechanisms helps protect sensitive user data and maintain the integrity of authenticated sessions.
What is Session Hijacking?
Session hijacking is a cyberattack where an attacker takes over a valid user session by stealing or predicting the session ID, allowing unauthorized access to a web application. This type of attack exploits vulnerabilities in session management to impersonate the legitimate user and gain sensitive information or control. Common methods include session sidejacking, cross-site scripting (XSS), and packet sniffing on unsecured networks.
How Session Hijacking Works
Session hijacking works by intercepting or stealing a valid user's session ID through methods such as packet sniffing, cross-site scripting (XSS), or man-in-the-middle attacks, allowing the attacker to impersonate the user and gain unauthorized access. Attackers exploit vulnerabilities in the session management mechanisms of web applications, often capturing session tokens transmitted over insecure channels or embedded in URLs. This enables attackers to bypass authentication controls, manipulate user data, and perform actions on behalf of the legitimate user without detection.
Common Techniques Used in Session Hijacking
Session hijacking commonly involves techniques such as session sniffing, where attackers intercept session tokens via network traffic, and cross-site scripting (XSS), which enables unauthorized access by injecting malicious scripts to steal session cookies. Other methods include session sidejacking, where attackers capture unencrypted session IDs over insecure Wi-Fi connections, and man-in-the-middle (MITM) attacks that intercept communication between user and server. Exploiting predictable session IDs and session replay attacks are further techniques used to gain unauthorized session access.
What is Session Fixation?
Session Fixation is a cyberattack where an attacker sets or tricks a user's browser into using a known session ID, allowing the attacker to hijack the active session once the user logs in. Unlike session hijacking, which exploits an already established session, session fixation exploits trust by forcing the user to authenticate with a predetermined session identifier. Protecting against session fixation requires regenerating session IDs after login and implementing secure cookie attributes like HttpOnly and Secure flags.
How Session Fixation Exploits Web Sessions
Session Fixation exploits web sessions by tricking the user into authenticating with a predetermined session ID chosen by the attacker, allowing unauthorized access once the user logs in. This vulnerability occurs when the web application accepts a session ID from the URL, cookies, or hidden fields without generating a new session ID upon login. Session Fixation differs from Session Hijacking, where the attacker steals an existing active session ID rather than setting it before authentication.
Key Differences Between Session Hijacking and Session Fixation
Session Hijacking involves an attacker stealing an active session token to gain unauthorized access, while Session Fixation tricks a user into authenticating with a session ID predetermined by the attacker. In Session Hijacking, the attacker intercepts or steals session IDs in transit or from storage, whereas Session Fixation relies on forcing or setting the victim's session ID before login. The primary difference lies in the timing and control of the session token: Hijacking occurs post-authentication, while Fixation occurs pre-authentication.
Real-World Examples of Session Hijacking and Session Fixation
Session hijacking incidents include the 2011 PSP data breach where attackers exploited session cookies to gain unauthorized access to user accounts, highlighting the risk of intercepted session tokens. In contrast, session fixation was notably used in the 2010 Facebook vulnerability where attackers set a session ID before login, allowing them to take over the session once the user authenticated. Both types of attacks emphasize the critical importance of secure session management practices like regenerating session IDs after login and using secure, HttpOnly cookies.
Prevention Strategies for Both Attacks
Preventing session hijacking involves implementing secure communication protocols such as HTTPS, utilizing strong session tokens, and regularly regenerating session IDs to minimize the risk of interception. In contrast, defense against session fixation centers on invalidating existing session identifiers upon user login and enforcing strict session management policies to prevent attackers from pre-setting session IDs. Both strategies benefit from multi-factor authentication and monitoring for unusual session behaviors to enhance overall session security.
Best Practices for Secure Session Management
Secure session management requires implementing strong measures to prevent session hijacking and session fixation attacks. Best practices include enforcing HTTPS to protect session tokens, using secure, HttpOnly, and SameSite cookie attributes, and regenerating session IDs after authentication to avoid fixation risks. Implementing timeouts and monitoring for unusual session activity further enhances security by reducing the window of opportunity for attackers.
Session Hijacking Infographic
 libterm.com
libterm.com