Symmetric encryption uses the same key for both encrypting and decrypting data, making it a fast and efficient method for securing information. It plays a crucial role in protecting your sensitive data during transmission and storage by ensuring only authorized parties can access it. Explore the rest of this article to understand how symmetric encryption works and its essential applications in cybersecurity.
Table of Comparison
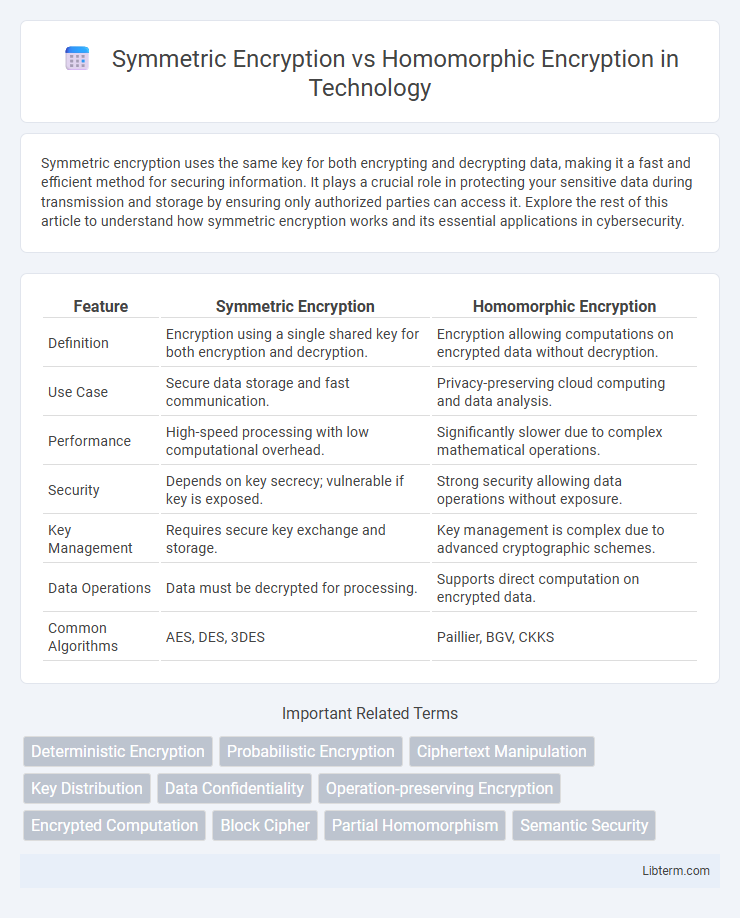
| Feature | Symmetric Encryption | Homomorphic Encryption |
|---|---|---|
| Definition | Encryption using a single shared key for both encryption and decryption. | Encryption allowing computations on encrypted data without decryption. |
| Use Case | Secure data storage and fast communication. | Privacy-preserving cloud computing and data analysis. |
| Performance | High-speed processing with low computational overhead. | Significantly slower due to complex mathematical operations. |
| Security | Depends on key secrecy; vulnerable if key is exposed. | Strong security allowing data operations without exposure. |
| Key Management | Requires secure key exchange and storage. | Key management is complex due to advanced cryptographic schemes. |
| Data Operations | Data must be decrypted for processing. | Supports direct computation on encrypted data. |
| Common Algorithms | AES, DES, 3DES | Paillier, BGV, CKKS |
Introduction to Symmetric and Homomorphic Encryption
Symmetric encryption uses a single secret key for both encryption and decryption, providing fast and efficient data protection ideal for secure communication. Homomorphic encryption enables computation on encrypted data without decryption, allowing privacy-preserving data processing and analysis in cloud computing environments. This capability makes homomorphic encryption essential for secure data outsourcing while maintaining confidentiality.
Defining Symmetric Encryption: Core Concepts
Symmetric encryption is a cryptographic method that uses a single secret key for both encryption and decryption, ensuring data confidentiality through fast and efficient processing. It relies on algorithms like AES (Advanced Encryption Standard) to transform plaintext into ciphertext, which can only be reverted with the same key. This approach is widely used in securing communications, databases, and stored data due to its simplicity and high performance.
Understanding Homomorphic Encryption: An Overview
Homomorphic encryption enables computation on encrypted data without requiring decryption, preserving privacy and security in cloud computing and data processing. Unlike symmetric encryption, which uses a single secret key for both encryption and decryption, homomorphic encryption supports operations like addition and multiplication directly on ciphertexts, producing an encrypted result matching operations on plaintexts. This feature is crucial for secure data analytics, allowing third parties to process encrypted information without access to the underlying sensitive data.
Key Differences Between Symmetric and Homomorphic Encryption
Symmetric encryption uses a single private key for both encryption and decryption, offering fast processing suitable for large data volumes, while homomorphic encryption enables computation on encrypted data without decryption, preserving data privacy during processing but with higher computational overhead. Symmetric encryption is widely used for secure communication where speed is critical, whereas homomorphic encryption supports advanced applications like secure cloud computing and privacy-preserving data analysis. Key management differs significantly as symmetric systems require secure key exchange, whereas homomorphic encryption handles keys that allow operations on ciphertexts without exposing the plaintext.
Security Strengths: Symmetric vs Homomorphic Encryption
Symmetric encryption offers strong security through fast, efficient algorithms like AES, making it ideal for securing data at rest and in transit with proven resistance against brute-force attacks when proper key lengths are used. Homomorphic encryption enables computation on encrypted data without decryption, providing enhanced privacy and security for cloud computing and data analysis, though it currently incurs higher computational overhead and complexity. While symmetric encryption excels in practical, high-speed protection, homomorphic encryption strengthens data confidentiality by preserving encryption during processing, ideal for secure outsourced computations.
Performance Comparison: Speed and Resource Efficiency
Symmetric encryption algorithms such as AES offer superior speed and resource efficiency, encrypting and decrypting data in milliseconds with minimal CPU and memory usage, making them ideal for real-time applications and large data volumes. Homomorphic encryption, while enabling computation on encrypted data, incurs significant computational overhead due to complex mathematical operations, resulting in encryption and processing times that are orders of magnitude slower and requiring substantially more memory and processing power. Therefore, symmetric encryption excels in performance for scenarios demanding fast throughput and low resource consumption, whereas homomorphic encryption prioritizes secure data processing at the cost of reduced speed and increased resource demands.
Real-World Applications: Use Cases for Each Encryption Type
Symmetric encryption is widely used in real-world applications such as securing data at rest, protecting files in cloud storage, and enabling fast, encrypted communication channels like VPNs due to its efficiency and speed. Homomorphic encryption finds critical use in privacy-preserving computations, allowing secure data processing in sensitive fields like healthcare for encrypted medical records analysis and finance for performing encrypted financial transactions without exposing raw data. Organizations prioritize symmetric encryption for routine data protection while leveraging homomorphic encryption in advanced scenarios requiring secure computation on encrypted datasets.
Limitations and Challenges of Symmetric and Homomorphic Encryption
Symmetric encryption faces challenges such as key distribution and management difficulties, vulnerability to key compromise, and limitations in enabling computations on encrypted data. Homomorphic encryption overcomes some of these by allowing computations on ciphertexts but suffers from significant performance overhead, increased computational complexity, and limited practical scalability due to noise accumulation in ciphertext. Both encryption methods present trade-offs between efficiency, security, and functionality, impacting their suitability for different applications.
Choosing the Right Encryption Method: Factors to Consider
Choosing the right encryption method depends on factors such as data sensitivity, processing requirements, and computational resources. Symmetric encryption offers faster performance and efficiency for securing large volumes of data, making it ideal for scenarios where data is stored or transmitted securely without real-time processing. Homomorphic encryption enables computation on encrypted data without decryption, providing strong privacy for applications like secure data analytics and cloud computing, though it requires significantly higher computational power and complexity.
Future Trends in Encryption Technologies
Symmetric encryption remains a cornerstone for data protection due to its efficiency and speed, but emerging trends highlight increased integration of homomorphic encryption for secure computation on encrypted data without decryption. Future encryption technologies prioritize enhancing homomorphic schemes to enable more complex computations with reduced latency, addressing challenges in cloud computing, privacy-preserving machine learning, and secure data sharing. Advances in algorithm optimization and hardware acceleration are driving the scalability and practical adoption of homomorphic encryption alongside traditional symmetric encryption frameworks.
Symmetric Encryption Infographic
 libterm.com
libterm.com