IPS technology delivers vibrant colors and wide viewing angles, enhancing your visual experience on monitors and smartphones. Its consistent image quality makes it ideal for graphic design, gaming, and professional applications where color accuracy matters. Explore the full article to discover how IPS panels can transform your display experience.
Table of Comparison
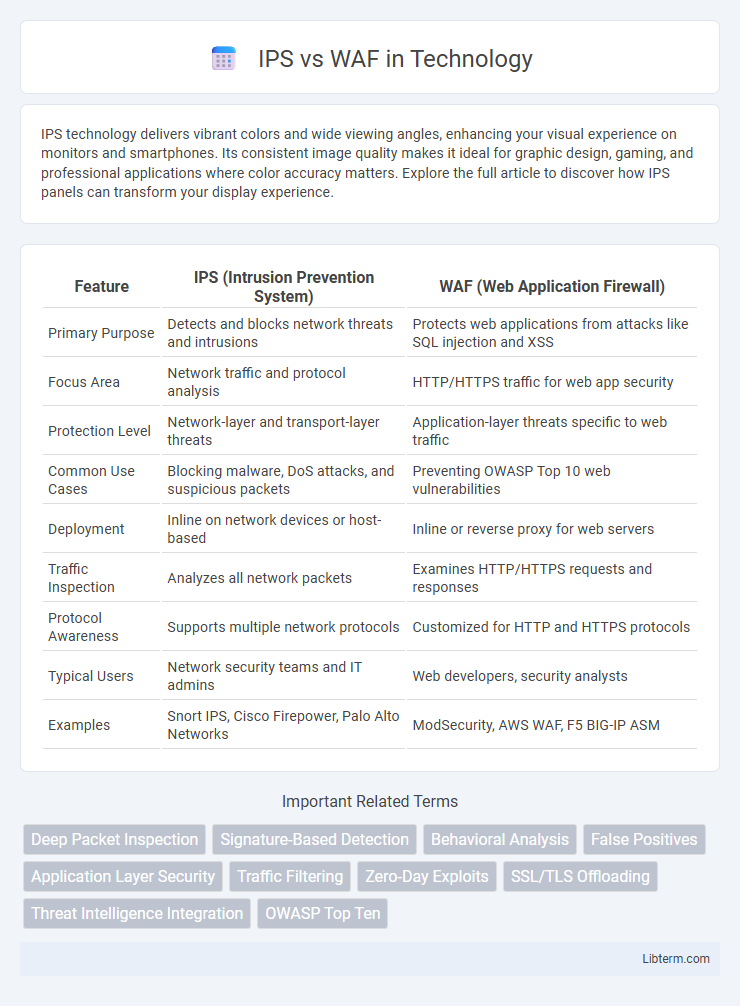
| Feature | IPS (Intrusion Prevention System) | WAF (Web Application Firewall) |
|---|---|---|
| Primary Purpose | Detects and blocks network threats and intrusions | Protects web applications from attacks like SQL injection and XSS |
| Focus Area | Network traffic and protocol analysis | HTTP/HTTPS traffic for web app security |
| Protection Level | Network-layer and transport-layer threats | Application-layer threats specific to web traffic |
| Common Use Cases | Blocking malware, DoS attacks, and suspicious packets | Preventing OWASP Top 10 web vulnerabilities |
| Deployment | Inline on network devices or host-based | Inline or reverse proxy for web servers |
| Traffic Inspection | Analyzes all network packets | Examines HTTP/HTTPS requests and responses |
| Protocol Awareness | Supports multiple network protocols | Customized for HTTP and HTTPS protocols |
| Typical Users | Network security teams and IT admins | Web developers, security analysts |
| Examples | Snort IPS, Cisco Firepower, Palo Alto Networks | ModSecurity, AWS WAF, F5 BIG-IP ASM |
Introduction to IPS and WAF
Intrusion Prevention Systems (IPS) monitor network traffic to identify and block potential threats in real-time, enhancing cybersecurity by preventing attacks before they reach critical systems. Web Application Firewalls (WAF) specifically protect web applications by filtering and monitoring HTTP traffic to prevent exploits such as SQL injection and cross-site scripting (XSS). Both IPS and WAF are integral to a layered security approach, with IPS providing broad network defense while WAF targets application-level vulnerabilities.
Core Functions of IPS
Intrusion Prevention Systems (IPS) primarily focus on detecting and blocking malicious network traffic in real-time by analyzing packet data, signatures, and behavioral patterns to prevent threats such as exploits, malware, and denial-of-service attacks. Unlike Web Application Firewalls (WAF) which protect web applications by filtering HTTP/HTTPS traffic and preventing attacks like SQL injection or cross-site scripting, IPS operates at the network level to safeguard a broader range of protocols and services. Key functionalities of IPS include continuous network monitoring, automated threat response, and vulnerability exploitation prevention, making it essential for comprehensive network security.
Core Functions of WAF
Web Application Firewalls (WAF) specifically protect web applications by filtering and monitoring HTTP traffic to prevent attacks like SQL injection, Cross-Site Scripting (XSS), and other OWASP Top 10 threats. Unlike Intrusion Prevention Systems (IPS) that analyze network traffic for a broad range of threats, WAFs inspect application-layer protocols, enforcing rules tailored to web traffic patterns and vulnerabilities. Core functions of a WAF include filtering malicious requests, blocking unauthorized data leakage, and providing detailed application-layer logging and alerts to enhance security posture.
Key Differences Between IPS and WAF
Intrusion Prevention Systems (IPS) primarily detect and block network-based attacks by analyzing traffic patterns and signatures at the network layer, while Web Application Firewalls (WAF) safeguard web applications by filtering, monitoring, and blocking HTTP/HTTPS traffic to prevent attacks like SQL injection and cross-site scripting (XSS). IPS operates broadly across the network infrastructure, offering protection against threats such as malware and DoS attacks, whereas WAF focuses specifically on application-layer threats targeting web interfaces. The implementation of IPS often involves inline network traffic inspection, whereas WAF deployment typically involves reverse proxy configurations tailored for application-specific security policies.
Deployment Scenarios for IPS
Intrusion Prevention Systems (IPS) are typically deployed inline within network infrastructure to monitor and block malicious traffic in real time, often positioned at network perimeters, data centers, or critical junction points to enhance threat detection and prevention. IPS deployment scenarios include integration with routers, switches, or dedicated appliances to provide immediate response against exploits, malware, and intrusion attempts while minimizing network latency. Unlike Web Application Firewalls (WAF) focused on HTTP/HTTPS traffic and application-layer security, IPS offers broader network-layer protection across diverse protocols and services.
Deployment Scenarios for WAF
Web Application Firewalls (WAF) are primarily deployed to protect web applications from threats such as SQL injection, cross-site scripting (XSS), and layer 7 DDoS attacks by filtering and monitoring HTTP/HTTPS traffic. Common deployment scenarios for WAFs include reverse proxy mode, where the WAF sits between users and the web server to inspect incoming traffic, and transparent bridge mode, which allows seamless integration without changing IP addresses. Cloud-based WAF services offer scalable protection with minimal on-premises hardware, ideal for modern hybrid and multi-cloud environments.
Strengths and Limitations of IPS
Intrusion Prevention Systems (IPS) excel at real-time threat detection and automated blocking of network-based attacks, leveraging deep packet inspection and signature-based detection to prevent known and emerging threats. IPS strength lies in its capacity for proactive response within network traffic, reducing attack surface and minimizing the impact of intrusions without human intervention. Limitations include potential false positives that may disrupt legitimate traffic, inability to analyze encrypted traffic without additional decryption capabilities, and limited protection against application-layer attacks that require more granular inspection found in Web Application Firewalls (WAFs).
Strengths and Limitations of WAF
Web Application Firewalls (WAFs) excel in protecting web applications by filtering and monitoring HTTP traffic to block common threats like SQL injection and cross-site scripting, enhancing security against application-layer attacks. WAFs provide customizable rule sets and can be deployed quickly without modifying existing infrastructure, making them highly adaptable for evolving web environments. However, WAFs may struggle with false positives, limited protection beyond the application layer, and often require continuous tuning to stay effective against new and complex attack vectors.
Choosing Between IPS and WAF
Choosing between an Intrusion Prevention System (IPS) and a Web Application Firewall (WAF) depends on the specific security needs and network architecture of an organization. IPS is designed to monitor network traffic for malicious activity and enforce security rules at the network level, making it ideal for detecting and preventing a wide range of cyber threats. WAF specializes in protecting web applications by filtering and monitoring HTTP/HTTPS traffic, effectively mitigating vulnerabilities such as SQL injection, cross-site scripting, and other application-layer attacks.
Integrating IPS and WAF for Comprehensive Security
Integrating Intrusion Prevention Systems (IPS) and Web Application Firewalls (WAF) delivers a comprehensive security framework by combining network-level threat detection with application-specific protection. IPS effectively monitors and blocks malicious traffic across the network, while WAF safeguards against web-based attacks such as SQL injection and cross-site scripting. This integration ensures layered defense, reducing attack surface and enabling more accurate threat identification through shared intelligence and coordinated response mechanisms.
IPS Infographic
 libterm.com
libterm.com