A thorough compliance review ensures that your business adheres to all relevant laws, regulations, and internal policies, minimizing risks and avoiding costly penalties. This process identifies potential gaps and implements corrective actions to strengthen your organization's compliance framework. Explore the rest of the article to discover effective strategies for conducting a comprehensive compliance review.
Table of Comparison
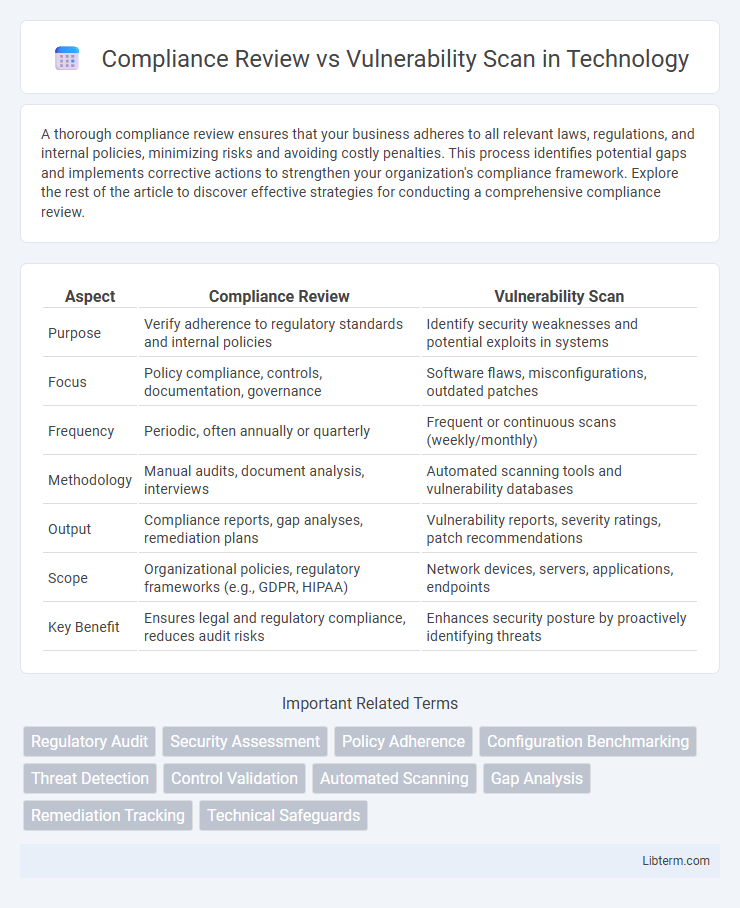
| Aspect | Compliance Review | Vulnerability Scan |
|---|---|---|
| Purpose | Verify adherence to regulatory standards and internal policies | Identify security weaknesses and potential exploits in systems |
| Focus | Policy compliance, controls, documentation, governance | Software flaws, misconfigurations, outdated patches |
| Frequency | Periodic, often annually or quarterly | Frequent or continuous scans (weekly/monthly) |
| Methodology | Manual audits, document analysis, interviews | Automated scanning tools and vulnerability databases |
| Output | Compliance reports, gap analyses, remediation plans | Vulnerability reports, severity ratings, patch recommendations |
| Scope | Organizational policies, regulatory frameworks (e.g., GDPR, HIPAA) | Network devices, servers, applications, endpoints |
| Key Benefit | Ensures legal and regulatory compliance, reduces audit risks | Enhances security posture by proactively identifying threats |
Introduction to Compliance Review and Vulnerability Scan
Compliance review evaluates an organization's adherence to regulatory standards, internal policies, and industry best practices by systematically assessing controls and processes. Vulnerability scans identify security weaknesses in systems, networks, or applications by automatically detecting outdated software, misconfigurations, and exploitable vulnerabilities. Both methods are essential for maintaining cybersecurity posture, with compliance reviews focusing on policy alignment and vulnerability scans targeting technical security risks.
Defining Compliance Review
Compliance review is a systematic evaluation process that ensures an organization's policies, procedures, and controls align with regulatory requirements and industry standards such as GDPR, HIPAA, or PCI-DSS. This review assesses adherence to legal obligations and internal guidelines by auditing documentation, processes, and system configurations to identify gaps and enforce accountability. Compliance reviews differ from vulnerability scans by focusing on policy enforcement and regulatory adherence rather than identifying technical security weaknesses in IT infrastructure.
Understanding Vulnerability Scan
A vulnerability scan identifies, quantifies, and prioritizes vulnerabilities in a system by automatically probing devices for known security weaknesses, misconfigurations, or missing patches. It provides a detailed report on potential security issues without assessing compliance against regulatory standards, unlike a compliance review. Regular vulnerability scans are essential for proactive threat detection and remediation in cybersecurity management.
Key Differences Between Compliance Review and Vulnerability Scan
Compliance reviews focus on verifying adherence to specific regulatory standards and internal policies, assessing whether security controls meet required frameworks such as HIPAA or PCI-DSS. Vulnerability scans identify and analyze system weaknesses, misconfigurations, and software flaws that could be exploited by attackers, often using automated tools to detect real-time security issues. While compliance reviews evaluate policy implementation and procedural effectiveness, vulnerability scans concentrate on uncovering technical security gaps and potential attack vectors within the IT environment.
Objectives of Compliance Review
Compliance Review aims to ensure that an organization adheres to regulatory standards, internal policies, and industry best practices by systematically evaluating security controls and processes. It identifies gaps in compliance frameworks to mitigate risks associated with legal penalties, financial loss, and reputational damage. This review focuses on maintaining alignment with mandates such as GDPR, HIPAA, or PCI DSS to enforce accountability and secure sensitive data effectively.
Objectives of Vulnerability Scan
Vulnerability scans aim to identify security weaknesses, misconfigurations, and outdated software in IT systems and networks to prevent potential exploitation by cyber attackers. These scans provide a detailed inventory of vulnerabilities, prioritize risks based on severity, and offer actionable remediation guidelines to enhance system security. Unlike compliance reviews, which verify adherence to regulatory standards and organizational policies, vulnerability scans focus primarily on technical security flaws and exposure points.
Tools Used in Compliance Review vs Vulnerability Scan
Compliance review utilizes tools such as Qualys Policy Compliance, IBM OpenPages, and RSA Archer to assess adherence to regulatory standards and internal policies, focusing on configurations and controls. Vulnerability scanning relies on tools like Nessus, Rapid7 Nexpose, and OpenVAS to identify security weaknesses and potential exploits within network assets and applications. These distinct toolsets emphasize compliance verification versus identifying security flaws, respectively.
Benefits of Regular Compliance Reviews
Regular compliance reviews ensure adherence to industry standards and regulatory requirements, reducing the risk of legal penalties and enhancing organizational reputation. These reviews identify gaps in security policies and processes, enabling proactive remediation before vulnerabilities are exploited. Consistent compliance assessments foster a culture of accountability and continuous improvement, strengthening overall cybersecurity posture.
Advantages of Conducting Vulnerability Scans
Vulnerability scans offer the advantage of identifying security weaknesses proactively by systematically detecting known vulnerabilities across networks, systems, and applications. They provide real-time assessments that help organizations prioritize remediation efforts based on severity levels, enhancing overall security posture. Automated and repeatable, vulnerability scans reduce the risk of exploitation by enabling continuous monitoring and early detection of potential threats.
Choosing the Right Approach for Your Organization
Choosing the right security assessment between Compliance Review and Vulnerability Scan depends on your organization's specific goals and regulatory requirements. Compliance Reviews ensure adherence to industry standards like PCI-DSS or HIPAA, focusing on policy enforcement and procedural controls, while Vulnerability Scans identify technical weaknesses and potential entry points in your network infrastructure. Integrating both approaches delivers a comprehensive security posture, aligning regulatory compliance with proactive threat detection to protect critical assets effectively.
Compliance Review Infographic
 libterm.com
libterm.com