Cross-Site Scripting (XSS) is a security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. This exploit can lead to unauthorized access, data theft, and compromised user sessions, posing significant risks to your online security. Explore the rest of this article to understand how XSS works and the best strategies to protect your digital assets.
Table of Comparison
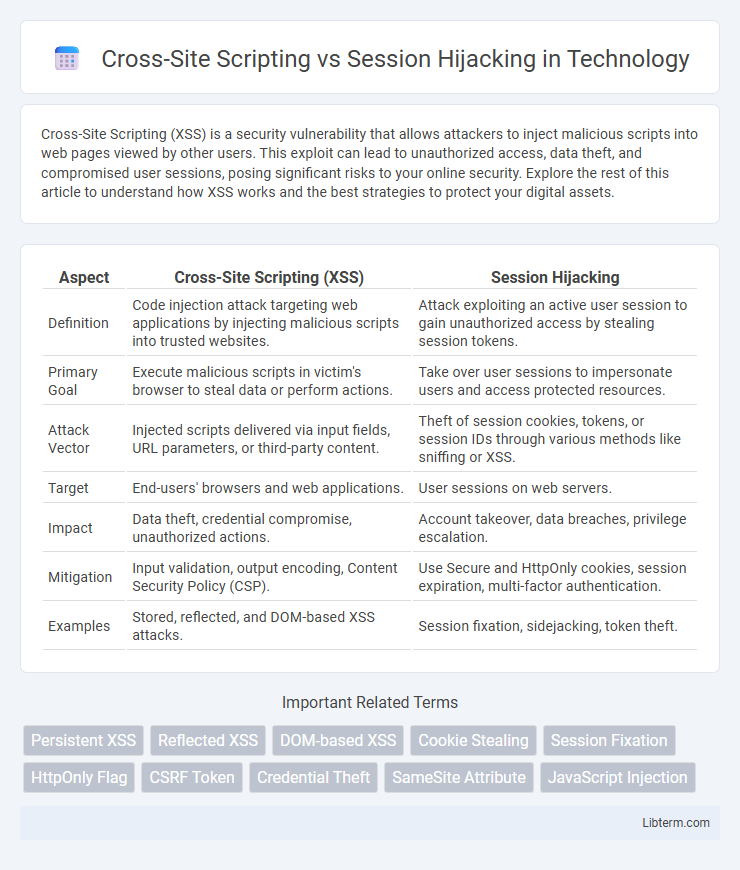
| Aspect | Cross-Site Scripting (XSS) | Session Hijacking |
|---|---|---|
| Definition | Code injection attack targeting web applications by injecting malicious scripts into trusted websites. | Attack exploiting an active user session to gain unauthorized access by stealing session tokens. |
| Primary Goal | Execute malicious scripts in victim's browser to steal data or perform actions. | Take over user sessions to impersonate users and access protected resources. |
| Attack Vector | Injected scripts delivered via input fields, URL parameters, or third-party content. | Theft of session cookies, tokens, or session IDs through various methods like sniffing or XSS. |
| Target | End-users' browsers and web applications. | User sessions on web servers. |
| Impact | Data theft, credential compromise, unauthorized actions. | Account takeover, data breaches, privilege escalation. |
| Mitigation | Input validation, output encoding, Content Security Policy (CSP). | Use Secure and HttpOnly cookies, session expiration, multi-factor authentication. |
| Examples | Stored, reflected, and DOM-based XSS attacks. | Session fixation, sidejacking, token theft. |
Understanding Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a cybersecurity vulnerability that enables attackers to inject malicious scripts into otherwise trusted websites, compromising user interactions by capturing sensitive data such as cookies or session tokens. Unlike session hijacking, which directly targets user sessions to gain unauthorized access, XSS exploits web application vulnerabilities to execute malicious code in the victim's browser. Understanding the mechanics of XSS is crucial for implementing effective input validation and output encoding strategies to protect web applications from data theft and unauthorized actions.
Defining Session Hijacking
Session hijacking involves attackers exploiting valid user session tokens to gain unauthorized access to a web application, bypassing authentication mechanisms. Unlike Cross-Site Scripting (XSS), which injects malicious scripts into trusted websites, session hijacking targets the user's active session to impersonate them and steal sensitive information. Effective prevention methods include secure cookie management, using HTTPS, and implementing robust session expiration policies.
How Cross-Site Scripting Attacks Work
Cross-Site Scripting (XSS) attacks occur when malicious scripts are injected into trusted websites, allowing attackers to execute unauthorized code in the victim's browser. This code can steal sensitive information such as cookies, session tokens, or other authentication data, leading to session hijacking. By exploiting vulnerabilities in web applications that fail to properly sanitize user inputs, attackers manipulate client-side scripts to gain unauthorized access and control over user sessions.
Session Hijacking: Methods and Techniques
Session hijacking involves attackers exploiting valid user sessions by stealing or predicting session tokens through methods such as session fixation, sidejacking using sniffed cookies over unsecured networks, or cross-site scripting (XSS) that injects malicious scripts to capture session IDs. Techniques like man-in-the-middle (MITM) attacks intercept session data, while malware or social engineering may also be used to obtain authentication tokens. Effective defenses include implementing secure cookies with HttpOnly and Secure flags, using encrypted communication via HTTPS, and deploying robust session management practices to detect and invalidate compromised sessions.
Comparing Attack Vectors: XSS vs Session Hijacking
Cross-Site Scripting (XSS) exploits vulnerabilities in web applications to inject malicious scripts that run in a user's browser, targeting the client-side environment. Session Hijacking captures or steals active session tokens or cookies to impersonate a user and gain unauthorized access to server-side resources. While XSS attacks leverage client-side script execution, session hijacking focuses on intercepting or manipulating session identifiers as the primary attack vector.
Common Vulnerabilities Leading to XSS
Common vulnerabilities leading to Cross-Site Scripting (XSS) include improper input validation, failure to sanitize user inputs, and insecure output encoding, allowing attackers to inject malicious scripts into web pages viewed by other users. Session hijacking often exploits these XSS vulnerabilities by stealing session cookies or tokens, enabling unauthorized access to a user's active session. Understanding and mitigating these weaknesses through secure coding practices and robust security controls is vital to prevent both XSS and related session hijacking attacks.
How Attackers Hijack Sessions
Attackers hijack sessions in Cross-Site Scripting (XSS) by injecting malicious scripts into trusted websites, which then execute in the victim's browser to steal session cookies or tokens. In session hijacking, adversaries intercept or predict valid session IDs through techniques such as network sniffing, man-in-the-middle attacks, or session fixation. Both methods exploit session credentials but differ as XSS leverages browser vulnerabilities while session hijacking directly targets session identifiers in transit or storage.
Prevention Strategies for Cross-Site Scripting
Cross-Site Scripting (XSS) prevention strategies emphasize input validation, output encoding, and Content Security Policy (CSP) implementation to avoid malicious script injection and execution. Employing secure coding practices, such as avoiding inline JavaScript and using frameworks with built-in XSS protections, reduces vulnerabilities. In contrast to session hijacking, which relies on securing session tokens through HTTPS and implementing secure cookie flags, XSS prevention focuses on neutralizing attacker-controlled script content before it can exploit user sessions.
Mitigation Methods Against Session Hijacking
Mitigation methods against session hijacking primarily involve implementing secure communication protocols like HTTPS to encrypt data and prevent interception of session tokens. Employing secure, HttpOnly, and SameSite cookie attributes restricts unauthorized access and cross-site scripting attacks that can lead to session theft. Regular session expiration, user authentication revalidation, and multi-factor authentication significantly reduce the risk of unauthorized session access.
Choosing the Right Security Measures: XSS vs Session Hijacking
Selecting the right security measures for Cross-Site Scripting (XSS) involves implementing content security policies (CSP), input validation, and output encoding to prevent malicious script injection. In contrast, defending against Session Hijacking requires secure cookie attributes, such as HttpOnly and Secure flags, along with multi-factor authentication and session timeout controls. Understanding the distinct attack vectors and appropriate mitigations ensures robust protection against both XSS and session hijacking threats.
Cross-Site Scripting Infographic
 libterm.com
libterm.com