Client Credentials Flow is an OAuth 2.0 authorization method that enables applications to authenticate and gain access to protected resources without user involvement. This flow is ideal for server-to-server communication where your application needs to securely connect to APIs using its own credentials. Explore the rest of the article to understand how to implement Client Credentials Flow effectively for your projects.
Table of Comparison
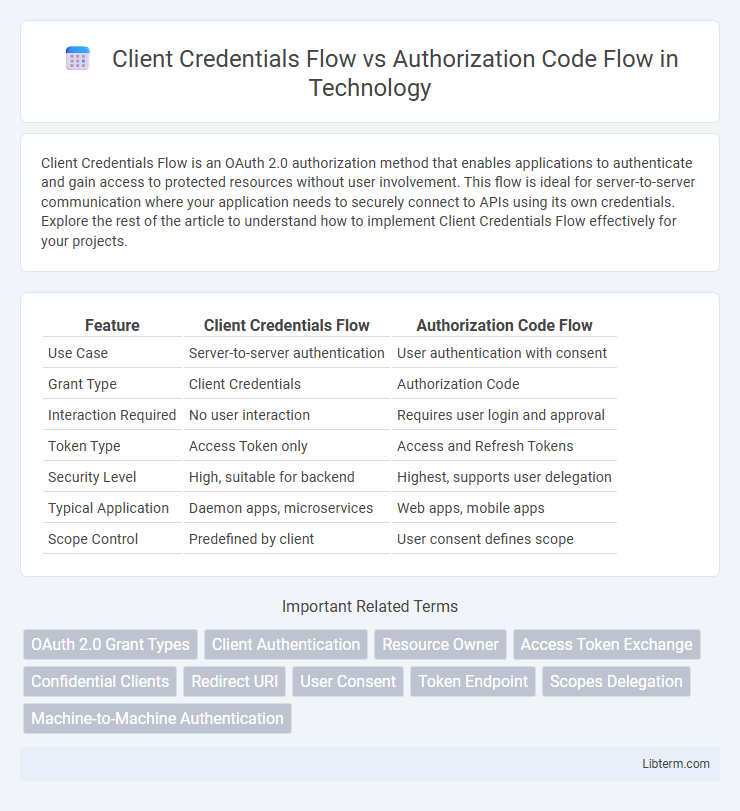
| Feature | Client Credentials Flow | Authorization Code Flow |
|---|---|---|
| Use Case | Server-to-server authentication | User authentication with consent |
| Grant Type | Client Credentials | Authorization Code |
| Interaction Required | No user interaction | Requires user login and approval |
| Token Type | Access Token only | Access and Refresh Tokens |
| Security Level | High, suitable for backend | Highest, supports user delegation |
| Typical Application | Daemon apps, microservices | Web apps, mobile apps |
| Scope Control | Predefined by client | User consent defines scope |
Introduction to OAuth 2.0 Grant Types
OAuth 2.0 grant types define methods for clients to obtain access tokens for resource access; the Client Credentials Flow is designed for machine-to-machine authentication without user context, providing direct token exchange using client ID and secret. Authorization Code Flow involves an interactive user login, exchanging an authorization code for tokens, ensuring secure delegated access with user consent and refresh token support. Understanding these flows is crucial for implementing secure API authorization tailored to different application scenarios.
Overview of Client Credentials Flow
Client Credentials Flow enables server-to-server authentication by allowing applications to obtain access tokens without user involvement, making it ideal for backend services and machine-to-machine interactions. It involves the client securely presenting its credentials to the authorization server, which then issues an access token for accessing protected resources. This flow excludes user consent and redirect URIs, optimizing security and efficiency for non-interactive scenarios.
Overview of Authorization Code Flow
Authorization Code Flow is a secure OAuth 2.0 authorization method designed for client applications that can maintain confidentiality, typically web and mobile apps. It involves an intermediate authorization code exchanged for an access token, ensuring the client never directly handles user credentials, enhancing security. This flow supports user consent, refresh tokens, and scopes, enabling fine-grained access control and long-lived sessions.
Key Differences Between Both Flows
Client Credentials Flow is designed for server-to-server authentication where no user interaction is required, typically used by applications to access their own resources. Authorization Code Flow involves user authorization through a browser and exchange of an authorization code for tokens, providing enhanced security suitable for web and mobile applications accessing user data. Key differences include the presence of user consent, token exchange mechanisms, and suitability for different use cases: Client Credentials Flow lacks user involvement and grants access based on client identity, while Authorization Code Flow requires user authentication and consent.
Use Cases for Client Credentials Flow
Client Credentials Flow is primarily designed for server-to-server interactions where no user context is needed, such as automated backend services, microservices communication, or machine-to-machine authentication. It enables applications to obtain access tokens directly using their own credentials, making it ideal for secure API access without user involvement. Unlike Authorization Code Flow, which requires user authentication and consent, Client Credentials Flow is optimal for non-interactive scenarios demanding high security and efficiency.
Use Cases for Authorization Code Flow
Authorization Code Flow is ideal for applications requiring secure user authentication, such as web and mobile apps that need access to user data with explicit consent. This flow ensures authorization by redirecting users to the identity provider's login page, enabling multi-factor authentication and minimizing exposure of tokens. It suits scenarios where refresh tokens and long-lived sessions are necessary for managing user-specific permissions securely.
Security Implications and Best Practices
Client Credentials Flow is designed for machine-to-machine communication, eliminating end-user involvement and relying solely on client authentication via client ID and secret, which reduces risks related to token interception but requires secure storage of credentials to prevent unauthorized access. Authorization Code Flow involves user authentication through a browser redirect, exchanging an authorization code for an access token, enhancing security by limiting token exposure to the client and enabling the use of refresh tokens and PKCE (Proof Key for Code Exchange) to mitigate interception and replay attacks. Best practices include implementing secure storage and rotation of client secrets for Client Credentials Flow, enforcing HTTPS, employing PKCE in Authorization Code Flow, and adhering to the principle of least privilege when defining scopes and access permissions.
Choosing the Right OAuth 2.0 Flow
Client Credentials Flow is ideal for server-to-server communication where no user context is needed, enhancing security by avoiding user interaction. Authorization Code Flow suits applications requiring user authentication and consent, supporting secure token exchange via authorization codes. Selecting the right OAuth 2.0 flow depends on the application's need for user involvement and security requirements.
Implementation Challenges and Considerations
Client Credentials Flow requires managing secure storage and regular rotation of client secrets to prevent unauthorized access, posing challenges in secure backend implementation. Authorization Code Flow involves complex handling of redirect URIs, authorization codes, and refresh tokens, demanding rigorous user consent management and protection against CSRF attacks. Both flows necessitate careful consideration of token expiry, scope restrictions, and error handling to maintain robust security and seamless user experience.
Conclusion: Selecting the Optimal Flow
Client Credentials Flow suits server-to-server authentication where no user interaction is required, optimizing security and simplicity for machine-to-machine communication. Authorization Code Flow is ideal for applications needing user authentication and delegated access, ensuring secure token exchange with user consent. Choosing the optimal flow depends on whether the interaction involves user context or purely backend service authentication.
Client Credentials Flow Infographic
 libterm.com
libterm.com