Single Sign-On (SSO) streamlines your login process by allowing access to multiple applications with one set of credentials, enhancing both security and user convenience. It reduces password fatigue and minimizes the risk of data breaches associated with password reuse. Discover how SSO can transform your digital experience and improve security by reading the rest of this article.
Table of Comparison
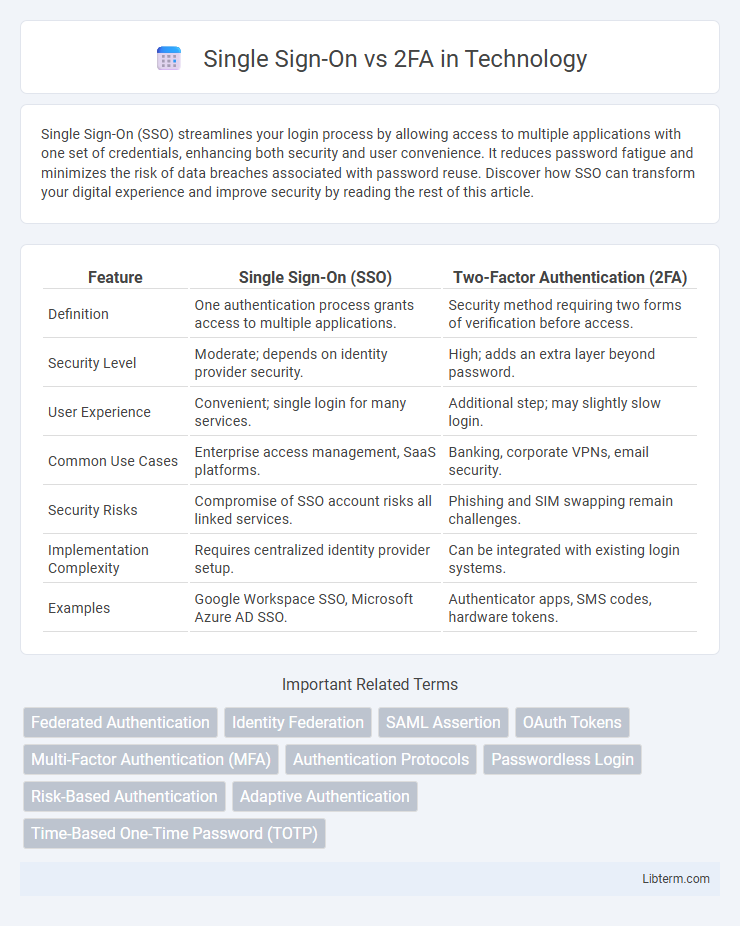
| Feature | Single Sign-On (SSO) | Two-Factor Authentication (2FA) |
|---|---|---|
| Definition | One authentication process grants access to multiple applications. | Security method requiring two forms of verification before access. |
| Security Level | Moderate; depends on identity provider security. | High; adds an extra layer beyond password. |
| User Experience | Convenient; single login for many services. | Additional step; may slightly slow login. |
| Common Use Cases | Enterprise access management, SaaS platforms. | Banking, corporate VPNs, email security. |
| Security Risks | Compromise of SSO account risks all linked services. | Phishing and SIM swapping remain challenges. |
| Implementation Complexity | Requires centralized identity provider setup. | Can be integrated with existing login systems. |
| Examples | Google Workspace SSO, Microsoft Azure AD SSO. | Authenticator apps, SMS codes, hardware tokens. |
Introduction to Single Sign-On (SSO) and Two-Factor Authentication (2FA)
Single Sign-On (SSO) streamlines user access by enabling authentication across multiple applications with a single set of credentials, improving convenience and reducing password fatigue. Two-Factor Authentication (2FA) enhances security by requiring two distinct verification methods, typically combining something the user knows (password) with something the user has (a mobile device or hardware token). Both SSO and 2FA play crucial roles in modern cybersecurity strategies, balancing user ease and protection against unauthorized access.
How Single Sign-On (SSO) Works
Single Sign-On (SSO) streamlines user authentication by allowing access to multiple applications with one set of login credentials, reducing password fatigue while enhancing user convenience. It operates through a centralized identity provider (IdP) that verifies user credentials once and grants tokens or assertions to connected service providers for seamless access. This method contrasts with two-factor authentication (2FA), which adds an extra verification layer, but does not consolidate login processes across platforms.
Understanding Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) enhances security by requiring users to provide two distinct forms of identification, typically something they know (password) and something they have (a mobile device or hardware token). Unlike Single Sign-On (SSO), which allows access to multiple applications with one set of credentials, 2FA adds an extra verification layer to prevent unauthorized access even if passwords are compromised. Implementing 2FA significantly reduces the risk of account breaches through phishing, password theft, or cyberattacks by strengthening user authentication processes.
Key Differences Between SSO and 2FA
Single Sign-On (SSO) allows users to access multiple applications with one set of login credentials, streamlining authentication processes across various platforms. Two-Factor Authentication (2FA) adds an extra layer of security by requiring users to provide two forms of identification, typically combining a password with a secondary factor like a mobile app code or biometric verification. The key difference lies in SSO optimizing convenience and access management, while 2FA primarily enhances security by mitigating unauthorized access risks.
Security Strengths of SSO vs 2FA
Single Sign-On (SSO) streamlines user authentication by enabling access to multiple applications with one set of credentials, reducing password fatigue but potentially increasing risk if the SSO credentials are compromised. Two-Factor Authentication (2FA) enhances security by requiring an additional verification step beyond the password, significantly decreasing unauthorized access even if the primary password is stolen. While SSO improves user convenience and centralized access control, 2FA provides a stronger defense against phishing and credential theft by enabling multi-layered authentication.
User Experience: SSO vs 2FA
Single Sign-On (SSO) enhances user experience by allowing seamless access to multiple applications with one set of credentials, reducing login fatigue and improving productivity. Two-Factor Authentication (2FA) adds an extra security layer by requiring a second verification step, which may introduce slight delays but significantly boosts account protection. Combining SSO with 2FA optimizes security without sacrificing convenience, balancing ease of access and robust user authentication.
Implementation Challenges of SSO and 2FA
Implementing Single Sign-On (SSO) requires integration across diverse applications and platforms, often demanding complex configuration and compatibility checks, which can lead to increased setup time and potential security risks if misconfigured. Two-Factor Authentication (2FA) implementation faces challenges related to user adoption, usability, and managing multiple authentication methods while ensuring secure token delivery and minimizing account lockouts. Both SSO and 2FA must address scalability, user experience, and robust security enforcement to successfully protect enterprise environments.
Best Use Cases for SSO and 2FA
Single Sign-On (SSO) is best suited for enterprise environments requiring seamless access to multiple applications with one set of credentials, enhancing user productivity and reducing password fatigue. Two-Factor Authentication (2FA) is optimal for securing sensitive accounts with an additional verification layer, safeguarding against unauthorized access even if password credentials are compromised. Combining SSO with 2FA provides a balanced approach, ensuring both convenient access management and robust security in high-risk scenarios.
Integration Possibilities: SSO with 2FA
Single Sign-On (SSO) integrates seamlessly with Two-Factor Authentication (2FA) to enhance security without compromising user convenience by requiring a second authentication factor after the initial SSO login. Many identity providers support combining SSO with various 2FA methods such as SMS codes, authenticator apps, or hardware tokens to create a robust access control system. This integration enables centralized management of authentication policies, streamlining compliance with security standards while reducing password-related risks.
Choosing the Right Authentication Method for Your Organization
Single Sign-On (SSO) streamlines user access by enabling one set of credentials for multiple applications, improving user convenience and reducing password fatigue. Two-Factor Authentication (2FA) enhances security by requiring a second form of verification beyond a password, significantly lowering the risk of account breaches. Organizations should evaluate their security requirements and user experience goals, often combining SSO with 2FA to balance seamless access with robust protection.
Single Sign-On Infographic
 libterm.com
libterm.com