Penetration testing identifies vulnerabilities in your network by simulating real-world cyberattacks to uncover security weaknesses before hackers can exploit them. This proactive approach helps organizations strengthen defenses and ensure compliance with industry standards. Discover how penetration testing can protect your digital assets by reading the full article.
Table of Comparison
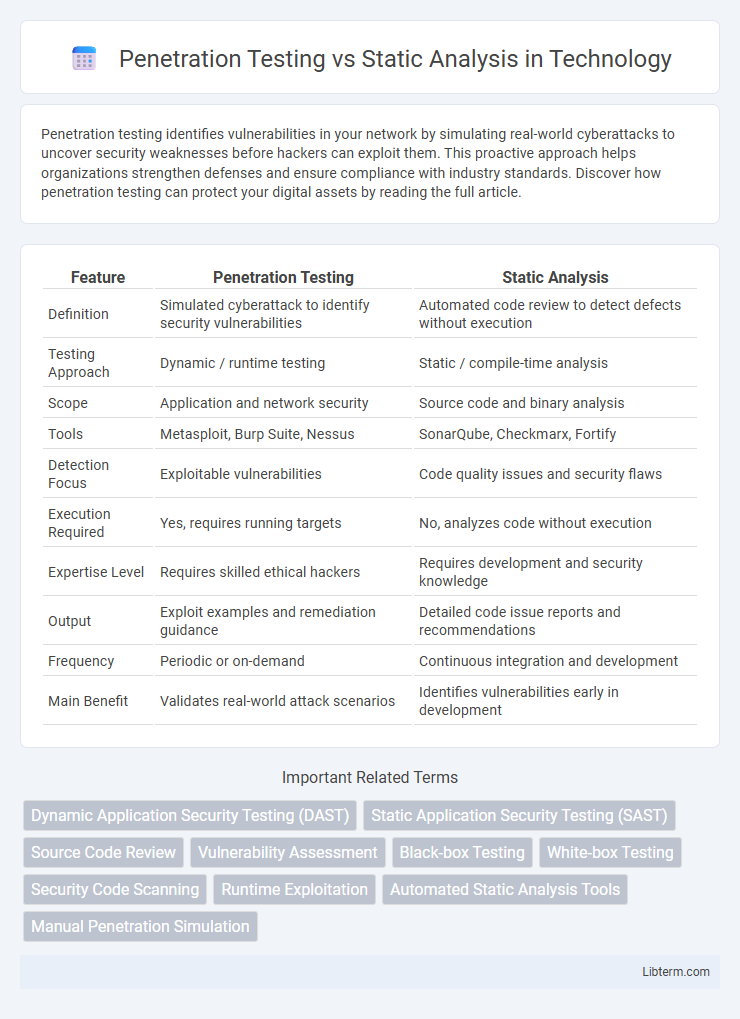
| Feature | Penetration Testing | Static Analysis |
|---|---|---|
| Definition | Simulated cyberattack to identify security vulnerabilities | Automated code review to detect defects without execution |
| Testing Approach | Dynamic / runtime testing | Static / compile-time analysis |
| Scope | Application and network security | Source code and binary analysis |
| Tools | Metasploit, Burp Suite, Nessus | SonarQube, Checkmarx, Fortify |
| Detection Focus | Exploitable vulnerabilities | Code quality issues and security flaws |
| Execution Required | Yes, requires running targets | No, analyzes code without execution |
| Expertise Level | Requires skilled ethical hackers | Requires development and security knowledge |
| Output | Exploit examples and remediation guidance | Detailed code issue reports and recommendations |
| Frequency | Periodic or on-demand | Continuous integration and development |
| Main Benefit | Validates real-world attack scenarios | Identifies vulnerabilities early in development |
Understanding Penetration Testing
Penetration testing involves simulating cyberattacks on a system to identify vulnerabilities that could be exploited in real-world scenarios, providing hands-on assessment beyond code examination. It evaluates the security posture by exploiting weaknesses in network configurations, user permissions, and software implementations. This dynamic approach uncovers risks static analysis might miss, such as logic flaws and runtime issues.
What is Static Analysis?
Static analysis is a cybersecurity technique that examines source code, bytecode, or binaries without executing the program to identify vulnerabilities, coding errors, and security flaws early in the development lifecycle. It uses automated tools to detect issues such as buffer overflows, injection flaws, and insecure coding patterns by analyzing the code structure, syntax, and data flow. Static analysis improves software security by enabling developers to fix potential risks before runtime, contrasting with penetration testing which evaluates security through simulated attacks on running systems.
Key Differences Between Penetration Testing and Static Analysis
Penetration testing simulates cyberattacks to identify exploitable vulnerabilities by actively probing live systems, whereas static analysis examines source code or binaries for potential security flaws without execution. Penetration testing provides real-world attack insights by exploiting vulnerabilities, while static analysis offers early detection of coding errors and security weaknesses during development. These methods differ in timing, scope, and execution, with penetration testing being dynamic and environment-dependent, and static analysis being code-centric and automated.
Advantages of Penetration Testing
Penetration testing offers the advantage of simulating real-world cyberattacks to identify vulnerabilities that automated static analysis might miss, including complex business logic flaws and runtime environment issues. It provides a comprehensive assessment of security by exploiting weaknesses in applications, networks, and systems, revealing potential attack paths and the practical impact of security gaps. Penetration testing also enhances an organization's incident response readiness by testing detection and defense mechanisms under controlled, real-time attack conditions.
Benefits of Static Analysis in Software Security
Static analysis enhances software security by identifying vulnerabilities early in the development lifecycle, reducing the cost and effort of fixes compared to penetration testing done post-deployment. It provides comprehensive code coverage with automated tools, uncovering hidden flaws such as buffer overflows, injection flaws, and insecure API usage before the software runs. This proactive approach ensures continuous security compliance and minimizes the risk of exploits in production environments.
When to Use Penetration Testing
Penetration testing is most effective when assessing the actual security posture of an application or network in real-world attack scenarios, identifying vulnerabilities that static analysis might miss. It is ideal for uncovering complex security flaws such as misconfigurations, authentication weaknesses, and business logic errors that require active exploitation. Use penetration testing during the later stages of the software development lifecycle or before major deployments to validate security defenses and demonstrate compliance with industry standards like OWASP Top Ten and PCI DSS.
Ideal Scenarios for Static Analysis
Static analysis excels in early-stage software development by identifying vulnerabilities, coding errors, and security flaws without executing the code, enhancing code quality and ensuring compliance with coding standards. It is ideal for continuous integration environments where automated tools can scan source code rapidly, enabling developers to fix issues before deployment. This technique suits organizations prioritizing secure coding practices and aiming to detect vulnerabilities at scale across large codebases.
Common Tools for Penetration Testing and Static Analysis
Common tools for penetration testing include Metasploit, Burp Suite, and Nmap, which enable security professionals to identify vulnerabilities through active exploitation and network scanning techniques. Static analysis relies on tools like SonarQube, Veracode, and Checkmarx to examine source code for security flaws, coding errors, and compliance issues without executing the program. Both approaches complement each other by combining dynamic vulnerability discovery with in-depth code quality assessment to strengthen overall application security.
Challenges and Limitations
Penetration testing faces challenges such as limited scope, reliance on tester expertise, and inability to identify all vulnerabilities within complex systems. Static analysis often struggles with false positives, scalability issues, and difficulty in interpreting code semantics accurately across diverse programming languages. Both methods have limitations in providing complete security assurance without complementary use in comprehensive security assessments.
Integrating Penetration Testing and Static Analysis for Robust Security
Integrating penetration testing with static analysis enhances the security posture by combining dynamic threat simulation and comprehensive code inspection, enabling identification of both runtime vulnerabilities and underlying code flaws. Penetration testing simulates real-world attacks to uncover exploitable security weaknesses, while static analysis automatically scans source code to detect coding errors, insecure patterns, and compliance violations before deployment. Leveraging both approaches creates a robust security framework, optimizing vulnerability detection across the software development lifecycle and improving remediation strategies for enterprise applications.
Penetration Testing Infographic
 libterm.com
libterm.com