Post-Quantum Cryptography focuses on developing encryption algorithms resistant to quantum computer attacks, ensuring data security in a future where classical cryptographic methods may be compromised. These innovative techniques rely on mathematical problems believed to be hard for quantum machines to solve, safeguarding sensitive information against evolving threats. Explore the rest of this article to understand how post-quantum cryptography can protect your digital privacy.
Table of Comparison
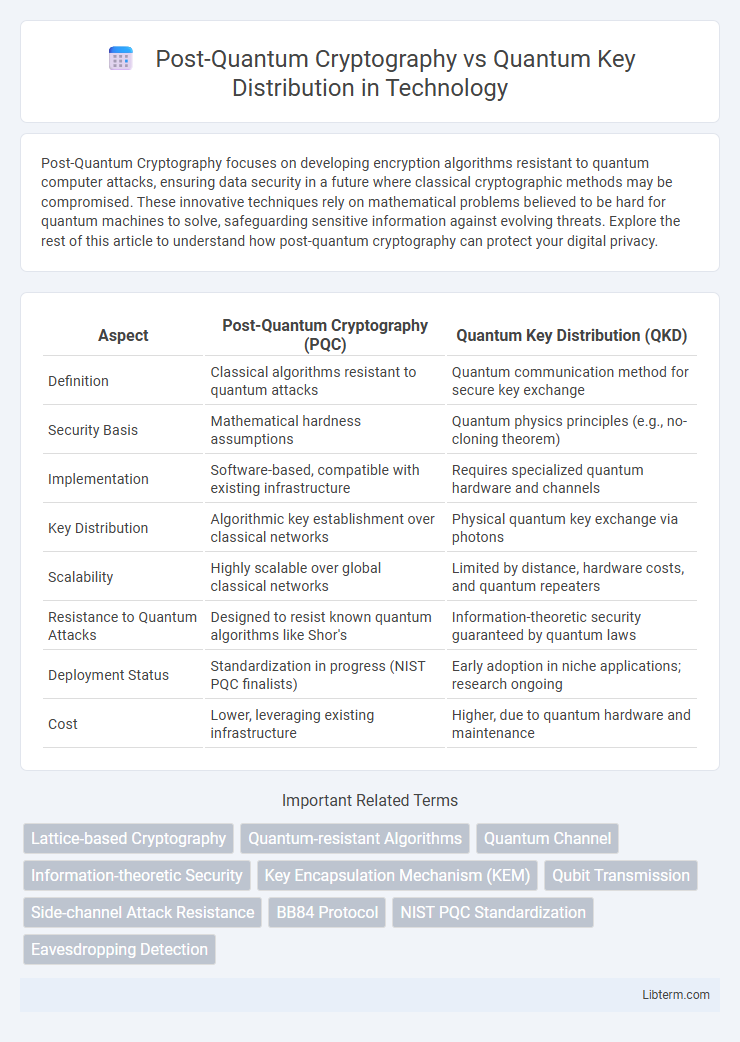
| Aspect | Post-Quantum Cryptography (PQC) | Quantum Key Distribution (QKD) |
|---|---|---|
| Definition | Classical algorithms resistant to quantum attacks | Quantum communication method for secure key exchange |
| Security Basis | Mathematical hardness assumptions | Quantum physics principles (e.g., no-cloning theorem) |
| Implementation | Software-based, compatible with existing infrastructure | Requires specialized quantum hardware and channels |
| Key Distribution | Algorithmic key establishment over classical networks | Physical quantum key exchange via photons |
| Scalability | Highly scalable over global classical networks | Limited by distance, hardware costs, and quantum repeaters |
| Resistance to Quantum Attacks | Designed to resist known quantum algorithms like Shor's | Information-theoretic security guaranteed by quantum laws |
| Deployment Status | Standardization in progress (NIST PQC finalists) | Early adoption in niche applications; research ongoing |
| Cost | Lower, leveraging existing infrastructure | Higher, due to quantum hardware and maintenance |
Introduction to Post-Quantum Cryptography and Quantum Key Distribution
Post-Quantum Cryptography (PQC) involves cryptographic algorithms designed to be secure against attacks from quantum computers, relying on mathematical problems such as lattice-based, hash-based, and code-based cryptography. Quantum Key Distribution (QKD) uses principles of quantum mechanics to enable secure communication by generating shared encryption keys, ensuring detection of any eavesdropping through quantum states' measurement properties. PQC offers software-based solutions compatible with existing infrastructure, while QKD requires specialized hardware and physical quantum channels for key exchange.
Understanding Quantum Computing Threats
Post-Quantum Cryptography (PQC) develops algorithms capable of withstanding attacks from quantum computers by relying on hard mathematical problems, ensuring the security of classical communication channels. Quantum Key Distribution (QKD) leverages principles of quantum mechanics to provide provably secure key exchange, but requires specialized quantum hardware and infrastructure. Understanding quantum computing threats highlights the urgency of implementing PQC for broad compatibility, while QKD offers a complementary approach focused on ultimate security through physical quantum properties.
Fundamentals of Post-Quantum Cryptography
Post-Quantum Cryptography (PQC) relies on classical algorithms designed to withstand attacks from quantum computers, utilizing hard mathematical problems such as lattice-based cryptography, code-based cryptography, and multivariate polynomial equations. PQC algorithms enable secure communication without the need for quantum channels, making them compatible with existing digital infrastructure and scalable for widespread deployment. These cryptographic methods focus on computational assumptions rather than physical quantum phenomena, providing practical security solutions against future quantum adversaries.
Principles of Quantum Key Distribution
Quantum Key Distribution (QKD) relies on the principles of quantum mechanics, such as superposition and entanglement, to securely distribute cryptographic keys by detecting any eavesdropping through quantum state disturbances. QKD uses protocols like BB84, where the key is encoded in the polarization states of photons, ensuring that any interception alters the quantum states and alerts communicating parties. Post-Quantum Cryptography (PQC), in contrast, employs classical cryptographic algorithms designed to withstand attacks by quantum computers but does not involve quantum states or physical distribution methods.
Security Assumptions and Robustness
Post-Quantum Cryptography (PQC) relies on mathematical problems believed to be hard for quantum computers, such as lattice-based or code-based cryptography, ensuring security under the assumption that these problems remain intractable. Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to provide theoretically unbreakable security, assuming ideal quantum channels and devices free from implementation flaws. PQC offers robustness against real-world communication infrastructure with classical algorithms, while QKD requires specialized hardware and faces challenges from physical imperfections and noise in quantum channels.
Practical Implementation Challenges
Post-Quantum Cryptography (PQC) involves developing algorithms resistant to quantum attacks that can be implemented using existing digital infrastructure, yet faces challenges in standardization, performance, and integration with current systems. Quantum Key Distribution (QKD) relies on quantum mechanical principles to securely distribute encryption keys but requires specialized hardware, quantum channels, and faces distance limitations due to photon loss and noise. Practical implementation hurdles for QKD include high costs, scalability issues, and the necessity for trusted nodes in long-distance networks, whereas PQC demands rigorous security proofs and optimization for real-world computational constraints.
Performance and Scalability Comparison
Post-Quantum Cryptography (PQC) offers higher performance and better scalability by using classical communication channels and algorithms designed to resist quantum attacks, enabling seamless integration with existing infrastructure. Quantum Key Distribution (QKD) relies on quantum mechanics principles for secure key exchange but requires specialized hardware, high-quality quantum channels, and faces distance limitations that hinder widespread scalability. PQC schemes demonstrate lower latency and computational overhead compared to QKD systems, making PQC more practical for large-scale deployment in classical networks.
Real-World Applications and Use Cases
Post-Quantum Cryptography (PQC) provides scalable algorithms designed to secure data against future quantum attacks, enabling integration into existing digital infrastructure such as cloud computing, financial transactions, and government communications. Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to establish secure, tamper-proof communication channels, primarily applied in high-security networks like defense, critical infrastructure, and metropolitan area networks. While PQC offers broad compatibility with current systems, QKD delivers information-theoretic security, making them complementary technologies for enhancing cybersecurity in practical environments.
Future Prospects in Quantum-Safe Security
Post-Quantum Cryptography (PQC) aims to develop encryption algorithms resistant to quantum computing attacks, ensuring the security of digital data in a quantum future. Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to enable secure communication through the exchange of cryptographic keys with provable security guarantees. The future prospects for quantum-safe security involve integrating PQC for widespread software and hardware compatibility, while QKD offers specialized high-security applications, together forming a comprehensive defense against quantum cyber threats.
Conclusion: Choosing Between PQC and QKD
Post-Quantum Cryptography (PQC) offers scalable software-based encryption methods designed to resist quantum attacks on classical networks, ensuring compatibility with existing infrastructure. Quantum Key Distribution (QKD) provides information-theoretic security using quantum mechanics but requires specialized hardware and high costs, limiting widespread adoption. The choice between PQC and QKD depends on balancing practical deployment constraints against desired security levels, with PQC favored for broad applicability and QKD suited for environments demanding ultimate cryptographic security.
Post-Quantum Cryptography Infographic
 libterm.com
libterm.com