Packet filtering controls network traffic by examining packets' headers and determining whether to allow or block them based on predefined rules, enhancing security at the network layer. It effectively prevents unauthorized access while permitting legitimate communication, making it a cornerstone of firewall technology. Explore the rest of the article to understand how packet filtering can strengthen your network defenses.
Table of Comparison
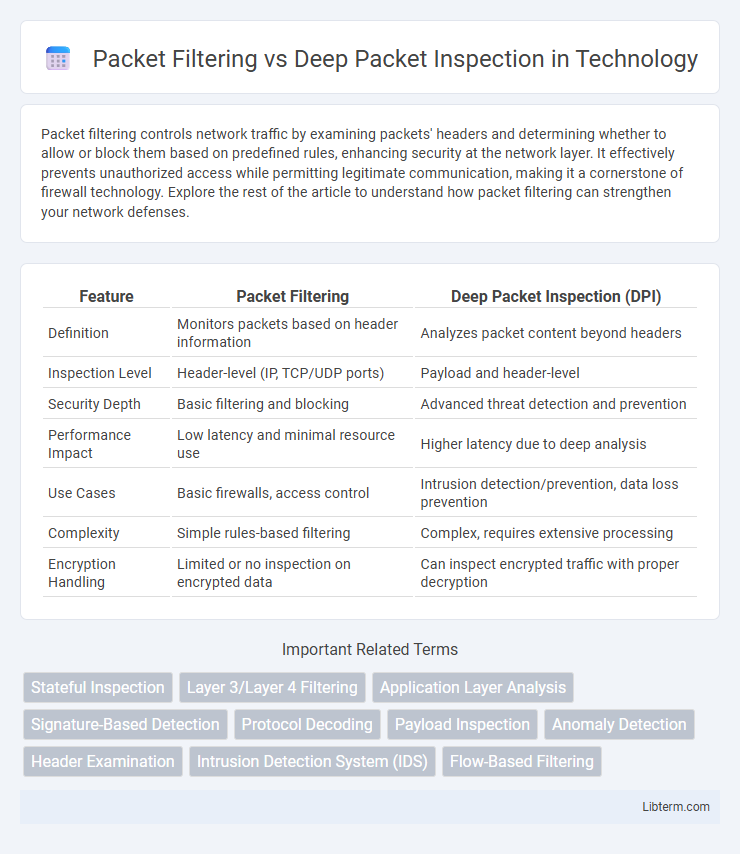
| Feature | Packet Filtering | Deep Packet Inspection (DPI) |
|---|---|---|
| Definition | Monitors packets based on header information | Analyzes packet content beyond headers |
| Inspection Level | Header-level (IP, TCP/UDP ports) | Payload and header-level |
| Security Depth | Basic filtering and blocking | Advanced threat detection and prevention |
| Performance Impact | Low latency and minimal resource use | Higher latency due to deep analysis |
| Use Cases | Basic firewalls, access control | Intrusion detection/prevention, data loss prevention |
| Complexity | Simple rules-based filtering | Complex, requires extensive processing |
| Encryption Handling | Limited or no inspection on encrypted data | Can inspect encrypted traffic with proper decryption |
Introduction to Packet Filtering and Deep Packet Inspection
Packet filtering is a network security mechanism that controls data flow based on predefined rules applied to packet headers, such as IP addresses, ports, and protocols, enabling efficient but basic traffic filtering. Deep Packet Inspection (DPI) analyzes the entire content of data packets beyond header information, detecting complex threats, enforcing policies, and providing granular control over network traffic. DPI offers advanced security capabilities by examining payload data, unlike packet filtering, which solely relies on header information for decision-making.
How Packet Filtering Works
Packet filtering works by examining packet headers to determine whether to allow or block data based on predefined rules such as IP addresses, ports, or protocols. This basic network security method operates at the OSI model's network layer, making rapid decisions without inspecting the packet payload. Packet filtering is efficient for managing traffic and preventing unauthorized access but lacks the granular inspection capabilities found in Deep Packet Inspection (DPI).
How Deep Packet Inspection Operates
Deep Packet Inspection (DPI) operates by analyzing the data portion and header of packets as they pass through a network inspection point, enabling it to detect, categorize, or block specific content, protocols, or threats. Unlike basic Packet Filtering that only checks packet headers, DPI drills down into the payload for granular inspection, which supports advanced security measures like intrusion detection, data leak prevention, and application control. This process involves inspecting packets against predefined rules or signatures to identify malicious code, unauthorized data transfers, or non-compliant usage.
Key Differences Between Packet Filtering and Deep Packet Inspection
Packet filtering examines only packet headers to allow or block traffic based on IP addresses, ports, and protocols, providing basic network security with minimal performance impact. Deep Packet Inspection (DPI) analyzes both headers and payloads, enabling more thorough inspection for malware, intrusions, and content filtering but requires higher processing resources. The key differences lie in DPI's ability to detect application-layer threats and enforce granular policies versus packet filtering's role in faster, less resource-intensive packet-level screening.
Security Capabilities Comparison
Packet filtering provides basic security by examining packet headers for source and destination IP addresses and ports, enabling simple access control and blocking of unauthorized traffic. Deep Packet Inspection (DPI) offers advanced security capabilities by analyzing the actual content of packets, detecting malware, intrusions, and enforcing application-level policies in real time. While packet filtering is efficient for ruling out unwanted traffic quickly, DPI ensures comprehensive protection against sophisticated threats through detailed content analysis.
Performance and Resource Impact
Packet filtering offers faster performance with minimal resource impact by inspecting only packet headers, making it suitable for high-speed networks requiring basic security controls. Deep packet inspection (DPI) consumes more CPU and memory resources due to its comprehensive examination of packet payloads, enabling advanced threat detection and granular traffic analysis. Organizations prioritizing low latency favor packet filtering, while those needing detailed security invest in DPI despite its higher resource demands.
Use Cases for Packet Filtering
Packet filtering is primarily used in network firewalls to control access by monitoring incoming and outgoing packets based on IP addresses, ports, and protocols. It is efficient for basic security measures such as blocking unauthorized access and preventing simple attacks like IP spoofing or unauthorized port access. Packet filtering is ideal for high-speed environments requiring minimal latency and where only fundamental traffic control is necessary.
Use Cases for Deep Packet Inspection
Deep Packet Inspection (DPI) is essential for advanced network security tasks such as identifying and blocking malware, detecting intrusion attempts, and enforcing granular content filtering policies across enterprise environments. It enables Internet Service Providers (ISPs) and data centers to monitor traffic for compliance, optimize bandwidth by prioritizing critical applications, and prevent data exfiltration by inspecting packet payloads beyond basic header information. DPI is particularly valuable in environments requiring regulatory compliance, threat intelligence, and real-time threat mitigation, where traditional packet filtering cannot provide sufficient application-level visibility.
Advantages and Limitations of Each Approach
Packet filtering offers advantages in speed and simplicity by examining packet headers to enforce basic security policies, making it efficient for high-throughput networks but limited by its inability to analyze packet payloads or detect complex threats. Deep Packet Inspection (DPI) provides detailed analysis of both headers and payloads, enabling detection of sophisticated attacks and enforcement of granular security rules, though it introduces higher latency and requires more processing power, which can impact network performance. While packet filtering excels in fast, straightforward filtering, DPI is superior for comprehensive threat detection but demands significant resources and may raise privacy concerns.
Choosing the Right Solution for Your Network
Packet filtering offers basic network security by examining header information such as IP addresses and port numbers, making it suitable for simple, high-speed filtering needs. Deep Packet Inspection (DPI) analyzes the entire data payload for enhanced threat detection, application control, and data leak prevention, ideal for environments requiring granular security measures. Selecting the right solution depends on your network's complexity, performance requirements, and security policies, where DPI is preferred for comprehensive inspection and packet filtering fits well in low-latency, resource-constrained scenarios.
Packet Filtering Infographic
 libterm.com
libterm.com