The Implicit Grant is an OAuth 2.0 authorization flow designed primarily for single-page applications where access tokens are obtained directly from the authorization endpoint without an intermediate authorization code. This flow enhances performance by reducing the number of requests but typically has shorter-lived tokens due to security considerations. Explore the rest of the article to understand how the Implicit Grant impacts your application's security and usability.
Table of Comparison
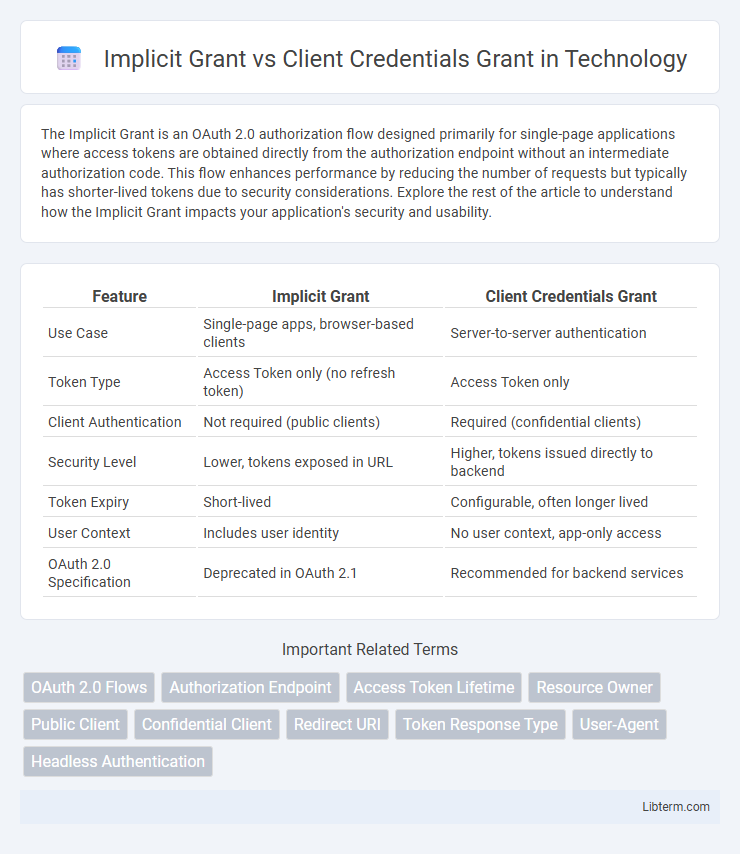
| Feature | Implicit Grant | Client Credentials Grant |
|---|---|---|
| Use Case | Single-page apps, browser-based clients | Server-to-server authentication |
| Token Type | Access Token only (no refresh token) | Access Token only |
| Client Authentication | Not required (public clients) | Required (confidential clients) |
| Security Level | Lower, tokens exposed in URL | Higher, tokens issued directly to backend |
| Token Expiry | Short-lived | Configurable, often longer lived |
| User Context | Includes user identity | No user context, app-only access |
| OAuth 2.0 Specification | Deprecated in OAuth 2.1 | Recommended for backend services |
Understanding OAuth 2.0 Grant Types
OAuth 2.0 grant types define methods for clients to obtain access tokens, with Implicit Grant designed for user-agent-based applications requiring immediate access without a backend server, often used in single-page apps. Client Credentials Grant allows server-to-server authentication by enabling applications to request tokens directly using their own credentials, ideal for machine-to-machine communication without user involvement. Understanding these grants ensures choosing the right flow for secure, efficient authorization in different application architectures.
What Is the Implicit Grant Flow?
The Implicit Grant flow is an OAuth 2.0 authorization method designed for single-page applications and browser-based apps where the client secret cannot be securely stored. It involves the client receiving an access token directly from the authorization endpoint without an intermediate authorization code, enabling quick token acquisition but with reduced security compared to authorization code flow. This flow is optimized for public clients that require immediate token issuance without back-end server communication.
What Is the Client Credentials Grant Flow?
The Client Credentials Grant flow allows applications to authenticate themselves directly with the authorization server, obtaining access tokens without user involvement. It is typically used for machine-to-machine (M2M) interactions, where the client app acts on its own behalf rather than on behalf of a user. This flow involves sending the client ID and client secret to the token endpoint, which returns an access token for accessing protected resources.
Key Differences Between Implicit and Client Credentials Grants
The Implicit Grant is used primarily in single-page applications and involves user authentication, allowing clients to obtain access tokens directly from the authorization endpoint without an intermediate authorization code. In contrast, the Client Credentials Grant is designed for machine-to-machine authentication, where the client application uses its own credentials to request an access token without user involvement. Key differences include the presence of user context in Implicit Grant versus the non-user-specific authentication in Client Credentials Grant, and token issuance methods, with Implicit Grant issuing tokens directly via the front channel and Client Credentials Grant obtaining tokens through secure backend server-to-server communication.
Security Implications of Each Grant Type
The Implicit Grant exposes access tokens directly to the user-agent, increasing the risk of token interception and abuse, making it less secure for web applications. In contrast, the Client Credentials Grant operates with server-to-server communication where credentials remain confidential, significantly reducing exposure to token theft. Consequently, the Client Credentials Grant is preferred for machine-to-machine authentication, while the Implicit Grant is discouraged due to its inherent security vulnerabilities.
When to Use Implicit Grant
Implicit Grant is designed for public clients, such as single-page web applications, where storing client secrets securely is impractical. It enables obtaining access tokens directly from the authorization endpoint without an intermediate authorization code, reducing latency for user authentication. This grant type is suitable when immediate access to protected resources is needed without server-side components capable of securely handling client credentials.
When to Use Client Credentials Grant
Client Credentials Grant is ideal for server-to-server authentication where no user context is required, such as backend API communications or microservices. It provides secure access by using the client's own credentials to obtain an access token directly from the authorization server. This grant type ensures efficient token retrieval for automated processes without the need for user interaction, making it perfect for machine-to-machine authorization scenarios.
Pros and Cons of the Implicit Grant
Implicit Grant offers rapid authorization by enabling token acquisition directly through the browser without requiring a client secret, making it suitable for single-page applications. However, it poses security risks due to exposure of access tokens in URLs and lacks refresh token support, increasing vulnerability to token theft and requiring frequent user re-authentication. The grant's limited token lifespan and reliance on browser redirects present challenges compared to more secure flows like Client Credentials Grant.
Pros and Cons of the Client Credentials Grant
Client Credentials Grant offers a streamlined authentication method for server-to-server interactions, providing enhanced security by not exposing user credentials or tokens to client applications. It enables efficient access to protected resources with minimal overhead and no need for user involvement, making it ideal for backend services or applications acting on their own behalf. However, its limitation lies in the inability to grant delegated user permissions or handle user authentication, restricting its use to scenarios where user context isn't required.
Choosing the Right OAuth 2.0 Grant for Your Application
Choosing the right OAuth 2.0 grant depends on the application type and security requirements. Implicit Grant is suited for browser-based or single-page applications where tokens are exposed directly to the user agent, offering a simplified flow without server-side token exchange. Client Credentials Grant is ideal for server-to-server authorization where the application can securely store client secrets and doesn't involve user authentication, ensuring higher security for backend services.
Implicit Grant Infographic
 libterm.com
libterm.com