AES (Advanced Encryption Standard) is a widely used symmetric encryption algorithm that ensures secure data transmission by converting plaintext into unreadable ciphertext using a secret key. It is essential for protecting sensitive information in various applications, including banking, communications, and data storage. Discover how AES works and why it is crucial for your digital security in the rest of this article.
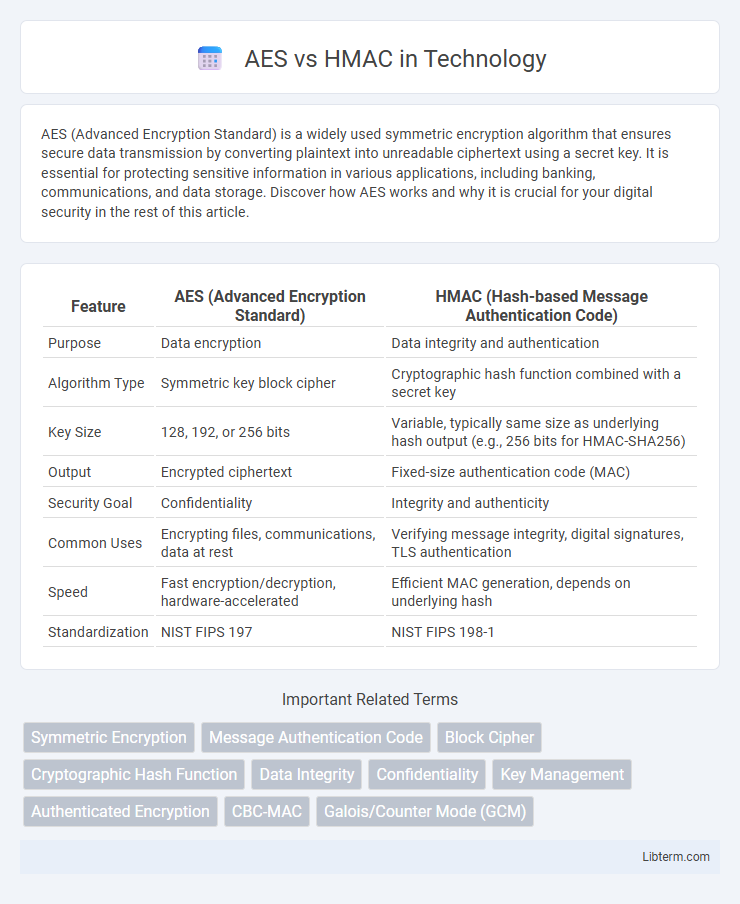
Table of Comparison
| Feature | AES (Advanced Encryption Standard) | HMAC (Hash-based Message Authentication Code) |
|---|---|---|
| Purpose | Data encryption | Data integrity and authentication |
| Algorithm Type | Symmetric key block cipher | Cryptographic hash function combined with a secret key |
| Key Size | 128, 192, or 256 bits | Variable, typically same size as underlying hash output (e.g., 256 bits for HMAC-SHA256) |
| Output | Encrypted ciphertext | Fixed-size authentication code (MAC) |
| Security Goal | Confidentiality | Integrity and authenticity |
| Common Uses | Encrypting files, communications, data at rest | Verifying message integrity, digital signatures, TLS authentication |
| Speed | Fast encryption/decryption, hardware-accelerated | Efficient MAC generation, depends on underlying hash |
| Standardization | NIST FIPS 197 | NIST FIPS 198-1 |
Introduction to AES and HMAC
AES (Advanced Encryption Standard) is a symmetric key encryption algorithm widely used for securing data through block cipher techniques, offering high efficiency and strong security in encrypting fixed-size data blocks. HMAC (Hash-based Message Authentication Code) combines a cryptographic hash function like SHA-256 with a secret key to provide message integrity and authentication, ensuring that data has not been altered. AES focuses on confidentiality by encrypting data, whereas HMAC ensures data authenticity and integrity without encrypting the content.
Core Differences Between AES and HMAC
AES (Advanced Encryption Standard) is a symmetric encryption algorithm primarily used for encrypting data to ensure confidentiality, converting plaintext into ciphertext using a secret key. HMAC (Hash-based Message Authentication Code) employs cryptographic hash functions combined with a secret key to provide data integrity and authentication, verifying that a message has not been altered. The core difference lies in AES securing data through encryption, while HMAC secures data authenticity and integrity without encrypting the content.
How AES Works: Encryption Basics
AES (Advanced Encryption Standard) operates by transforming plaintext into ciphertext through a series of well-defined steps including substitution, permutation, and mixing of data blocks, using a symmetric key. It divides the input data into fixed-size blocks (128 bits) and processes them through multiple rounds of encryption involving byte substitution, row shifting, column mixing, and key addition based on the key size (128, 192, or 256 bits). Unlike HMAC, which provides data integrity and authentication through cryptographic hashing combined with a secret key, AES focuses purely on data confidentiality by encrypting the content.
How HMAC Functions: Authentication Explained
HMAC (Hash-based Message Authentication Code) functions by combining a cryptographic hash function with a secret key to provide data integrity and authentication. It processes the message and secret key through two rounds of hashing, producing a fixed-size output that verifies both the authenticity and the integrity of the message. Unlike AES, which is primarily an encryption algorithm, HMAC ensures that the message has not been altered and originates from a legitimate sender, making it essential for secure communication protocols.
Use Cases: When to Use AES vs HMAC
AES is best suited for encrypting sensitive data to ensure confidentiality in applications like secure file storage, VPN communications, and encrypted messaging. HMAC provides data integrity and authentication, making it ideal for verifying message authenticity in APIs, digital signatures, and secure token validation. Use AES when confidentiality is required, and HMAC when integrity and authentication are the primary concerns.
Security Strengths of AES
AES (Advanced Encryption Standard) provides robust security through symmetric key encryption, offering key sizes of 128, 192, and 256 bits that resist brute-force attacks and ensure data confidentiality. Its design includes multiple rounds of substitution, permutation, and mixing operations, which strengthen resistance against cryptanalysis techniques such as differential and linear cryptanalysis. AES's widespread adoption in government and commercial applications underscores its reliability and high security strength in protecting sensitive data.
Security Benefits of HMAC
HMAC provides strong message integrity and authentication by combining a cryptographic hash function with a secret key, making it resistant to forgery and replay attacks. Unlike AES, which primarily ensures data confidentiality through encryption, HMAC verifies both the authenticity and integrity of the message, preventing tampering and impersonation. Its security relies on the strength of the underlying hash function, such as SHA-256, offering robust protection in verifying data origin and consistency.
Performance Comparison: AES vs HMAC
AES encryption operates with hardware acceleration in modern CPUs, offering fast and efficient data encryption and decryption. HMAC, relying on hash functions like SHA-256, generally processes data faster in software due to lower computational complexity. Performance differences depend on use case; AES excels in bulk data encryption while HMAC is more efficient for integrity verification and message authentication.
Common Vulnerabilities and Mitigations
AES encryption risks include key leakage and improper implementation of mode of operation, which can lead to vulnerabilities such as padding oracle attacks and ciphertext manipulation. HMAC is vulnerable to weak hash functions and timing attacks that can expose secret keys, but using strong hash functions like SHA-256 and implementing constant-time comparison mitigates these risks. Ensuring secure key management, adopting proper cryptographic libraries, and regularly updating algorithms are essential practices to prevent common vulnerabilities in both AES and HMAC.
Choosing the Right Algorithm for Your Needs
AES provides strong symmetric encryption to protect data confidentiality, while HMAC ensures data integrity and authentication using cryptographic hash functions. Choose AES for encrypting sensitive data where privacy is crucial, and HMAC for verifying message authenticity and detecting tampering. Evaluate your security requirements to determine if encryption, integrity, or both are necessary for your application.
AES Infographic
 libterm.com
libterm.com