A firewall acts as a critical security barrier between your internal network and external threats, monitoring and controlling incoming and outgoing traffic based on predetermined security rules. It helps prevent unauthorized access, cyber attacks, and data breaches by filtering potentially harmful traffic. Discover how implementing the right firewall can protect your digital assets by reading the rest of this article.
Table of Comparison
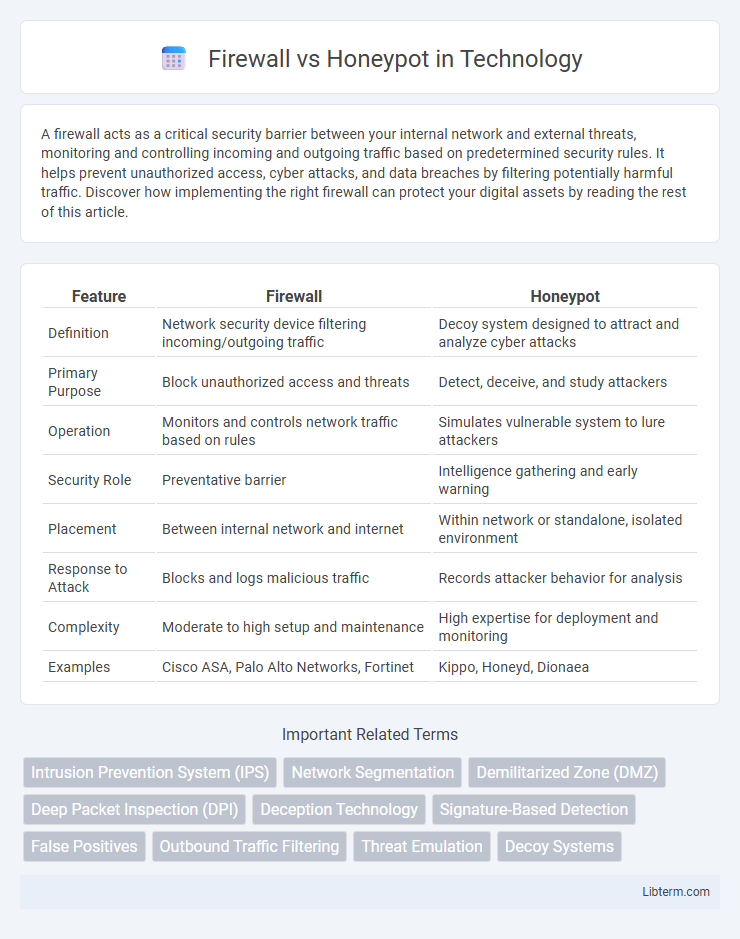
| Feature | Firewall | Honeypot |
|---|---|---|
| Definition | Network security device filtering incoming/outgoing traffic | Decoy system designed to attract and analyze cyber attacks |
| Primary Purpose | Block unauthorized access and threats | Detect, deceive, and study attackers |
| Operation | Monitors and controls network traffic based on rules | Simulates vulnerable system to lure attackers |
| Security Role | Preventative barrier | Intelligence gathering and early warning |
| Placement | Between internal network and internet | Within network or standalone, isolated environment |
| Response to Attack | Blocks and logs malicious traffic | Records attacker behavior for analysis |
| Complexity | Moderate to high setup and maintenance | High expertise for deployment and monitoring |
| Examples | Cisco ASA, Palo Alto Networks, Fortinet | Kippo, Honeyd, Dionaea |
Understanding Firewalls: Core Functions
Firewalls serve as critical security barriers that monitor and control incoming and outgoing network traffic based on predetermined security rules, effectively preventing unauthorized access. They operate through packet filtering, stateful inspection, and proxy services to enforce network policies and block malicious activity. Key firewall types include network firewalls, host-based firewalls, and next-generation firewalls (NGFWs), each designed to protect against diverse cyber threats by inspecting traffic at different layers.
What is a Honeypot? An Overview
A honeypot is a cybersecurity mechanism designed to attract and trap potential attackers by mimicking legitimate systems or data, thereby gathering valuable intelligence on attack methods and sources. Unlike a firewall, which serves as a barrier that blocks unauthorized access to a network, a honeypot operates as a decoy that lures attackers to study their behavior in a controlled environment. This proactive tool aids security teams in enhancing threat detection, analysis, and response strategies by providing real-time data on emerging cyber threats.
Key Differences Between Firewalls and Honeypots
Firewalls act as security barriers that filter incoming and outgoing network traffic based on predetermined rules to prevent unauthorized access, while honeypots serve as decoy systems designed to attract and analyze cyber attackers by mimicking vulnerable targets. Firewalls primarily provide perimeter defense and enforce access policies, whereas honeypots gather intelligence on attack methods and motives by engaging attackers in controlled environments. The key difference lies in their purpose: firewalls block threats proactively, while honeypots detect and study threats reactively.
How Firewalls Protect Network Perimeters
Firewalls safeguard network perimeters by monitoring and controlling incoming and outgoing traffic based on predetermined security rules, effectively blocking unauthorized access. They filter data packets and enforce access policies to prevent cyber threats such as malware, hackers, and data breaches from infiltrating internal networks. Unlike honeypots, which serve as decoys to detect attackers, firewalls provide a proactive defense mechanism that maintains the integrity and security of the entire network boundary.
The Role of Honeypots in Cybersecurity
Honeypots serve as deceptive traps designed to attract and analyze cyber attackers, providing crucial insights into emerging threats and attack techniques that traditional firewalls may miss. Unlike firewalls that block unauthorized access, honeypots detect, isolate, and study malicious activity by simulating vulnerable systems within a controlled environment. This proactive cybersecurity measure enhances threat intelligence, enabling organizations to improve defense strategies and strengthen overall network security.
Deployment Strategies: Firewall vs Honeypot
Firewalls are deployed at network perimeters to filter incoming and outgoing traffic based on predefined security rules, providing a first line of defense against unauthorized access and cyber threats. Honeypots are strategically placed in isolated segments within the network to lure attackers, monitor malicious activities, and gather intelligence without exposing critical assets. Combining firewalls for traffic control with honeypots for threat detection enhances overall network security by balancing prevention and proactive threat analysis.
Strengths and Weaknesses of Firewalls
Firewalls provide strong perimeter security by filtering incoming and outgoing network traffic based on established security rules, effectively blocking unauthorized access and mitigating external threats. Their limitations include difficulty in detecting internal threats or sophisticated attacks like zero-day exploits, as they primarily control network boundaries rather than monitor user behavior or system anomalies. Firewalls also struggle with encrypted traffic inspection and require constant updating to address evolving threats, making them less effective against insider attacks compared to honeypots that attract and analyze malicious activity.
Advantages and Limitations of Honeypots
Honeypots provide valuable advantages such as deception and early threat detection by attracting attackers and analyzing their techniques without risking critical systems. Their limitations include limited scalability, as they can only monitor a small segment of the network, and the risk of being identified and bypassed by sophisticated attackers. Despite these constraints, honeypots enhance cybersecurity by gathering actionable intelligence to improve defense mechanisms.
Choosing the Right Solution: Use Cases
Firewalls are essential for protecting network perimeters by filtering incoming and outgoing traffic based on security rules, making them ideal for organizations requiring robust access control and threat blocking. Honeypots serve as deception tools by mimicking vulnerable systems to detect, analyze, and divert cyber attackers, best suited for research environments and advanced threat intelligence gathering. Choosing between a firewall and a honeypot depends on whether the primary need is preventative defense or proactive threat detection and analysis.
Integrating Firewalls and Honeypots for Enhanced Security
Integrating firewalls and honeypots creates a layered security architecture, where firewalls control incoming and outgoing network traffic based on predetermined security rules, while honeypots actively lure attackers to detect and analyze malicious activities. This combination enhances threat intelligence, enabling rapid identification of sophisticated cyber threats and reducing false positives by differentiating legitimate traffic from attack vectors. Deployment of this integrated approach strengthens overall network defense by providing real-time alerts and comprehensive forensic data to cybersecurity professionals.
Firewall Infographic
 libterm.com
libterm.com