A Certificate Authority (CA) plays a crucial role in digital security by issuing and managing digital certificates that verify the authenticity of websites, software, and users. These certificates enable encrypted communication and trust between parties in online transactions and data exchanges. Discover how understanding Certificate Authorities can enhance your cybersecurity and protect your digital interactions in the rest of this article.
Table of Comparison
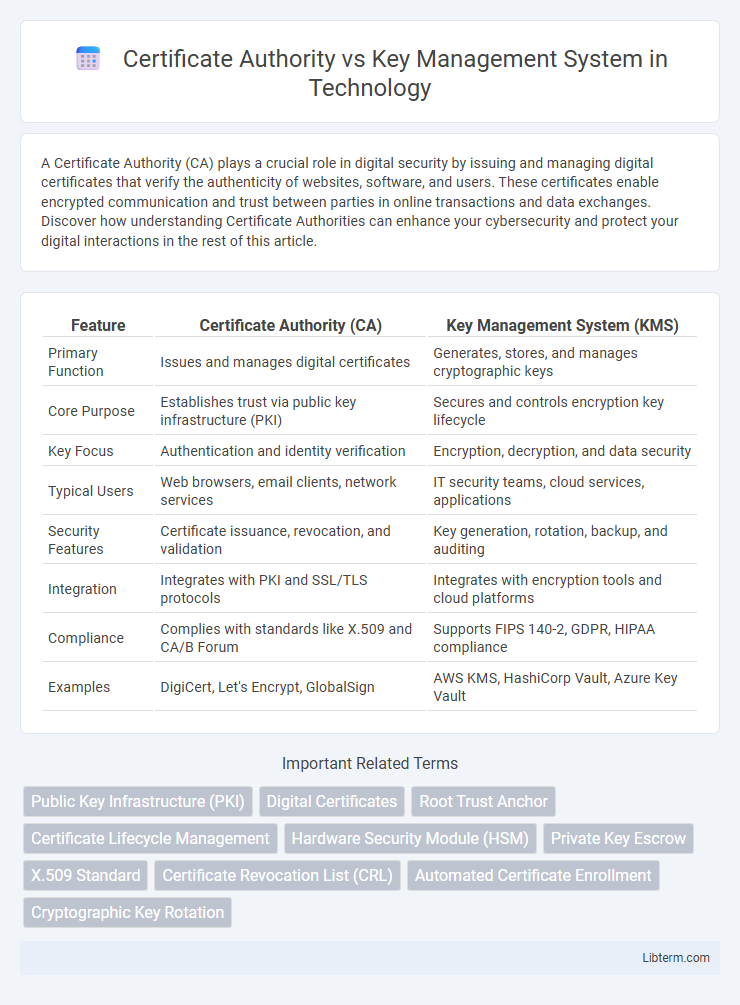
| Feature | Certificate Authority (CA) | Key Management System (KMS) |
|---|---|---|
| Primary Function | Issues and manages digital certificates | Generates, stores, and manages cryptographic keys |
| Core Purpose | Establishes trust via public key infrastructure (PKI) | Secures and controls encryption key lifecycle |
| Key Focus | Authentication and identity verification | Encryption, decryption, and data security |
| Typical Users | Web browsers, email clients, network services | IT security teams, cloud services, applications |
| Security Features | Certificate issuance, revocation, and validation | Key generation, rotation, backup, and auditing |
| Integration | Integrates with PKI and SSL/TLS protocols | Integrates with encryption tools and cloud platforms |
| Compliance | Complies with standards like X.509 and CA/B Forum | Supports FIPS 140-2, GDPR, HIPAA compliance |
| Examples | DigiCert, Let's Encrypt, GlobalSign | AWS KMS, HashiCorp Vault, Azure Key Vault |
Understanding Certificate Authorities (CA)
A Certificate Authority (CA) is a trusted entity responsible for issuing digital certificates that authenticate the identity of organizations and individuals in secure communications. It validates certificate requests, signs certificates using its private key, and maintains certificate revocation lists (CRLs) to ensure certificate integrity. Unlike a Key Management System (KMS) that primarily handles key storage and lifecycle management, a CA establishes trust frameworks essential for Public Key Infrastructure (PKI) by providing digital identity verification through certification.
What is a Key Management System (KMS)?
A Key Management System (KMS) is a centralized platform designed to generate, store, distribute, and manage cryptographic keys throughout their lifecycle, ensuring secure access and usage. Unlike a Certificate Authority (CA), which primarily issues digital certificates to verify identities, a KMS focuses on the control of encryption keys used for data protection, authentication, and cryptographic operations. Implementing a KMS enhances security compliance by enforcing policies, key rotation, and audit trails, critical for safeguarding sensitive information in cloud environments and enterprise networks.
Core Functions of Certificate Authorities
Certificate Authorities (CAs) primarily issue, validate, and revoke digital certificates that authenticate the identity of entities in cryptographic communications, ensuring secure data exchange and trust in public key infrastructure (PKI). Key Management Systems (KMS) focus on the generation, storage, distribution, and lifecycle management of cryptographic keys within an organization. The core function of Certificate Authorities includes verifying certificate requests, binding public keys to identities, and maintaining certificate revocation lists (CRLs) or online certificate status protocols (OCSP) to uphold security and trustworthiness.
Key Management System: Key Features
Key Management Systems (KMS) provide secure generation, storage, and lifecycle management of cryptographic keys to protect sensitive data. They enable automated rotation, centralized access control, and auditing to ensure compliance with security policies and reduce the risk of key compromise. Integration with cloud services and hardware security modules (HSM) enhances encryption efficiency and resilience in complex IT environments.
CA vs. KMS: Main Differences
Certificate Authority (CA) primarily issues and manages digital certificates to establish trust in public key infrastructures (PKI), while Key Management System (KMS) focuses on the secure generation, storage, distribution, and lifecycle management of cryptographic keys. CA validates identities and binds public keys to entities through certificates, enabling authentication and encrypted communications, whereas KMS ensures keys are securely handled to maintain data confidentiality and integrity. The main difference lies in CA's role in trust establishment via certificates versus KMS's comprehensive control over cryptographic key operations across various encryption services.
Use Cases: When to Use CA
Certificate Authorities (CAs) are essential for establishing trust through issuing digital certificates that authenticate identities in web browsers, email, and secure communications. They are ideal when verifying third-party identities and enabling public key infrastructure (PKI) environments for SSL/TLS encryption or code signing. Key Management Systems (KMS) focus on generating, storing, and managing cryptographic keys internally, making CAs preferable for scenarios requiring external trust validation and certificate lifecycle management.
Use Cases: When to Use KMS
A Key Management System (KMS) is essential for organizations that require centralized control over cryptographic keys used in data encryption, ensuring secure generation, storage, rotation, and lifecycle management across multiple applications and cloud services. Unlike a Certificate Authority (CA), which issues and manages digital certificates to authenticate identities and establish secure communications, a KMS is crucial in environments demanding stringent encryption key governance for data protection and compliance, such as securing databases, cloud storage, and application secrets. Enterprises handling sensitive data in regulated industries often deploy KMS to maintain high security standards and operational efficiency beyond what a CA provides.
Security Considerations: CA vs. KMS
Certificate Authorities (CAs) provide trusted identity verification through digital certificates, ensuring secure communication by binding public keys to verified entities. Key Management Systems (KMS) focus on the secure generation, storage, and lifecycle management of cryptographic keys, emphasizing protection against unauthorized access and key compromise. Security considerations highlight that while CAs establish trust frameworks and validation mechanisms, KMS enforces stringent access controls and audit trails to safeguard cryptographic material throughout its operational lifespan.
Integration and Interoperability
Certificate Authorities (CAs) and Key Management Systems (KMS) play complementary roles in cryptographic security, with integration focusing on seamless certificate issuance and lifecycle management within the key management framework. Interoperability between CAs and KMS is achieved through standardized protocols such as PKCS #11, CMP, and RESTful APIs, enabling automated certificate provisioning, renewal, and revocation while maintaining centralized control of cryptographic keys. Effective integration ensures compliance with security policies and simplifies operational workflows by unifying certificate management and key storage across diverse IT environments.
Choosing Between Certificate Authority and Key Management System
Choosing between a Certificate Authority (CA) and a Key Management System (KMS) depends on organizational security needs and infrastructure complexity. Certificate Authorities primarily issue, manage, and revoke digital certificates for identity verification within public key infrastructures. Key Management Systems focus on secure generation, storage, and lifecycle management of cryptographic keys, making them essential for internal encryption and data protection strategies.
Certificate Authority Infographic
 libterm.com
libterm.com