Mutating Webhooks enable dynamic modification of Kubernetes API requests, allowing you to customize resource configurations during creation or update. This powerful feature ensures your cluster maintains consistent policies and optimizes deployments. Explore the article to understand how Mutating Webhooks can enhance your Kubernetes workflows.
Table of Comparison
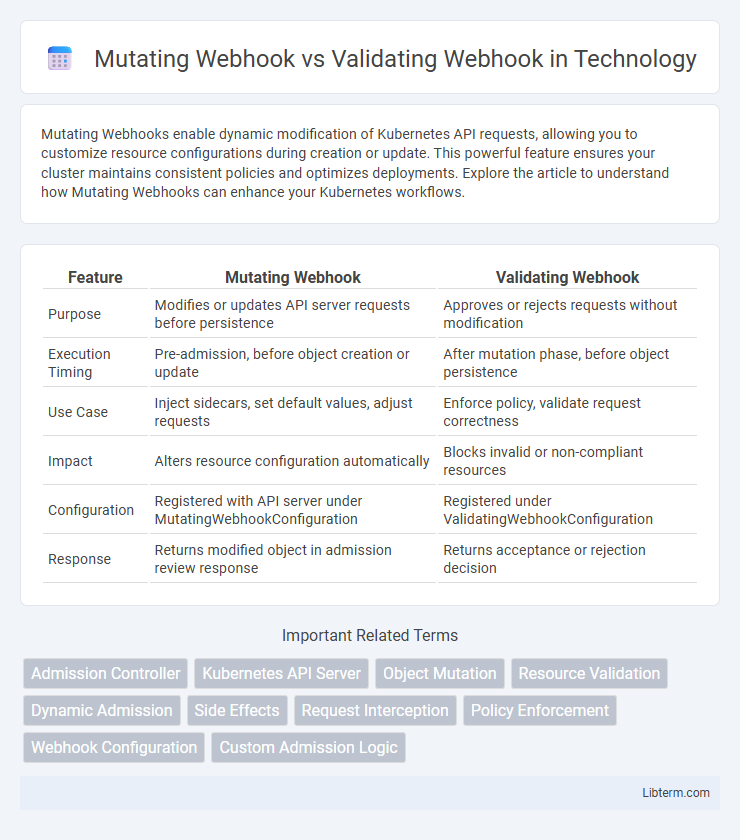
| Feature | Mutating Webhook | Validating Webhook |
|---|---|---|
| Purpose | Modifies or updates API server requests before persistence | Approves or rejects requests without modification |
| Execution Timing | Pre-admission, before object creation or update | After mutation phase, before object persistence |
| Use Case | Inject sidecars, set default values, adjust requests | Enforce policy, validate request correctness |
| Impact | Alters resource configuration automatically | Blocks invalid or non-compliant resources |
| Configuration | Registered with API server under MutatingWebhookConfiguration | Registered under ValidatingWebhookConfiguration |
| Response | Returns modified object in admission review response | Returns acceptance or rejection decision |
Introduction to Kubernetes Admission Webhooks
Kubernetes admission webhooks are crucial for customizing and controlling cluster behavior during resource creation or modification. Mutating webhooks modify object configurations before they are persisted, enabling automated defaults and sidecar injections, while validating webhooks enforce custom policies by rejecting non-compliant requests to ensure cluster security and compliance. Both webhook types integrate seamlessly into the Kubernetes admission chain, providing flexible mechanisms to enforce operational standards dynamically.
What is a Mutating Webhook?
A Mutating Webhook in Kubernetes is a type of admission webhook that intercepts API server requests to modify or mutate the objects before they are persisted. It enables automatic changes such as adding default labels, annotations, or injecting sidecar containers into pods. This webhook plays a crucial role in enhancing resource configurations dynamically during creation or update operations.
What is a Validating Webhook?
A Validating Webhook in Kubernetes intercepts API server requests to ensure that resource configurations meet predefined policies before they are persisted. It evaluates incoming resource changes without modifying them, enforcing validation logic to maintain cluster integrity. Unlike Mutating Webhooks, which alter objects, Validating Webhooks solely accept or reject requests based on compliance with rules.
Key Differences: Mutating vs Validating Webhook
Mutating Webhooks modify or change Kubernetes API requests before they are persisted, enabling dynamic alterations such as injecting sidecars or adding labels. Validating Webhooks only observe and validate the incoming requests without altering them, ensuring the resource complies with policies and preventing invalid configurations. The key difference lies in their function: Mutating Webhooks transform the object, while Validating Webhooks enforce correctness and compliance without modification.
How Mutating Webhooks Work
Mutating webhooks intercept Kubernetes API server requests before they are persisted, allowing modifications to object configurations such as adding default labels or annotations. They operate by receiving admission review requests, applying patches or changes to the resource, and returning altered resource definitions to the API server. This process ensures dynamic customization of Kubernetes objects during creation or update phases, enhancing cluster management flexibility.
How Validating Webhooks Operate
Validating webhooks function by intercepting Kubernetes API server requests to verify the contents of objects before they're persisted, ensuring that all modifications meet predefined validation criteria. They analyze admission review requests and respond with allowed or denied statuses based on custom validation logic, without altering the object data. This process helps enforce policies consistently and prevents invalid resource configurations from being accepted into the cluster.
Common Use Cases for Mutating Webhooks
Mutating webhooks are primarily used to modify or augment Kubernetes API requests, such as injecting sidecar containers, adding labels, or setting default values during pod creation. Common use cases include automatically inserting monitoring agents, configuring networking settings, and enforcing security policies by adjusting resource specifications before they are persisted. Validating webhooks, in contrast, only approve or reject API requests without altering them, ensuring compliance with policies and resource validation rules.
Popular Scenarios for Validating Webhooks
Validating Webhooks are popular in scenarios requiring strict admission control, such as enforcing security policies, validating configuration schemas, and preventing deployment of non-compliant resources. They operate by intercepting API requests to Kubernetes clusters, ensuring that objects meet predefined criteria before being persisted. This makes Validating Webhooks essential for compliance auditing, policy enforcement, and maintaining cluster stability by rejecting invalid or unauthorized changes.
Best Practices for Implementing Webhooks
Mutating webhooks modify incoming Kubernetes API requests to enforce policies or inject defaults, while validating webhooks block requests that do not meet predefined criteria, ensuring cluster consistency. Best practices for implementing webhooks include minimizing processing time to avoid request delays, securing communication with TLS and authentication, and maintaining version compatibility to prevent failures during API changes. Monitoring webhook performance and error rates is crucial to detect and resolve issues promptly, thus maintaining cluster stability and reliability.
Choosing the Right Webhook for Your Use Case
Mutating Webhooks modify Kubernetes API requests before they are persisted, suitable for injecting default configurations or labels, while Validating Webhooks enforce policies by validating requests without altering them, ideal for compliance and security checks. Choose Mutating Webhooks when automatic modifications to resource specifications enhance deployment consistency, and select Validating Webhooks to prevent invalid or unauthorized resource changes. Evaluating your need for transformation versus validation helps determine the appropriate webhook type to maintain cluster integrity and operational standards.
Mutating Webhook Infographic
 libterm.com
libterm.com