Public Key Infrastructure (PKI) is a robust framework that secures electronic communications through cryptographic key pairs, ensuring data integrity, confidentiality, and authentication. It involves digital certificates, certificate authorities, and registration authorities to manage and validate public keys effectively. Discover how PKI can enhance your cybersecurity strategy by exploring the detailed insights in the rest of this article.
Table of Comparison
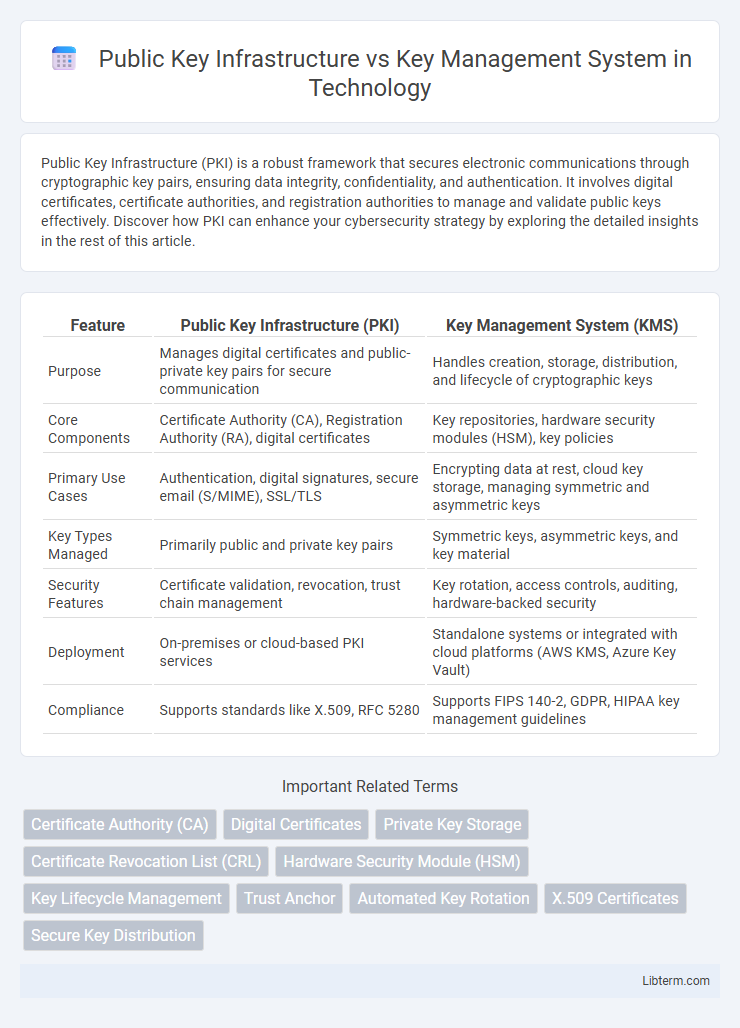
| Feature | Public Key Infrastructure (PKI) | Key Management System (KMS) |
|---|---|---|
| Purpose | Manages digital certificates and public-private key pairs for secure communication | Handles creation, storage, distribution, and lifecycle of cryptographic keys |
| Core Components | Certificate Authority (CA), Registration Authority (RA), digital certificates | Key repositories, hardware security modules (HSM), key policies |
| Primary Use Cases | Authentication, digital signatures, secure email (S/MIME), SSL/TLS | Encrypting data at rest, cloud key storage, managing symmetric and asymmetric keys |
| Key Types Managed | Primarily public and private key pairs | Symmetric keys, asymmetric keys, and key material |
| Security Features | Certificate validation, revocation, trust chain management | Key rotation, access controls, auditing, hardware-backed security |
| Deployment | On-premises or cloud-based PKI services | Standalone systems or integrated with cloud platforms (AWS KMS, Azure Key Vault) |
| Compliance | Supports standards like X.509, RFC 5280 | Supports FIPS 140-2, GDPR, HIPAA key management guidelines |
Introduction to Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI) establishes a framework for managing digital certificates and public-key encryption, ensuring secure electronic communication and authentication. It involves components like Certificate Authorities (CAs), Registration Authorities (RAs), and a repository for storing certificates, enabling trust through validation and issuance. PKI differs from a Key Management System (KMS), which primarily focuses on lifecycle management of cryptographic keys without necessarily providing the comprehensive validation and trust services PKI offers.
Understanding Key Management Systems (KMS)
Key Management Systems (KMS) provide centralized control over cryptographic keys, enabling secure generation, storage, distribution, and lifecycle management. Unlike Public Key Infrastructure (PKI), which primarily focuses on digital certificates and asymmetric key pair validation, KMS supports a broader range of key types and integrates with cloud services for scalable encryption management. KMS platforms ensure compliance with security standards by automating key rotation, access control, and auditing, essential for protecting sensitive data in dynamic IT environments.
Core Components of PKI
Public Key Infrastructure (PKI) core components include Certificate Authorities (CAs), Registration Authorities (RAs), digital certificates, public and private key pairs, and a central repository for certificate storage and revocation lists. These elements work together to enable secure digital identity verification, encryption, and digital signatures across networks. In contrast, a Key Management System (KMS) primarily focuses on the creation, storage, distribution, and lifecycle management of cryptographic keys without inherently providing the trust framework or certificate issuance functions of a PKI.
Key Management System Architecture
Key Management System (KMS) architecture centers on secure generation, storage, distribution, and lifecycle management of cryptographic keys, ensuring robust access controls and auditability. Unlike Public Key Infrastructure (PKI), which manages digital certificates and asymmetric keys for authentication and encryption, KMS supports both symmetric and asymmetric keys within a centralized or hierarchical structure. Core components of KMS architecture include secure key stores, hardware security modules (HSMs), key usage policies, and integration with enterprise applications to maintain cryptographic integrity and compliance.
Security Functions: PKI vs KMS
Public Key Infrastructure (PKI) provides robust security functions such as digital certificate issuance, authentication, encryption, and non-repudiation, enabling secure communications and identity verification through asymmetric cryptography. Key Management Systems (KMS) specialize in centralized lifecycle management of cryptographic keys, including key generation, storage, rotation, and revocation, primarily supporting symmetric key operations to maintain data confidentiality. While PKI ensures trust establishment using public-private key pairs and certificate authorities, KMS enhances operational security by automating key safeguards and access controls within enterprise environments.
Use Cases and Applications
Public Key Infrastructure (PKI) is primarily used for secure communication, identity verification, and digital signatures, enabling encryption and authentication across networks and applications. Key Management Systems (KMS) focus on the lifecycle management of cryptographic keys, including generation, storage, rotation, and access control, making them essential for cloud services, data encryption, and regulatory compliance. Organizations deploy PKI for securing email, VPNs, and SSL/TLS certificates, while KMS is integral for managing keys in cloud platforms like AWS KMS, Azure Key Vault, and Google Cloud KMS to protect sensitive data and automate key policies.
Scalability and Flexibility Considerations
Public Key Infrastructure (PKI) offers robust scalability through hierarchical trust models and certificate authorities, enabling secure management of large-scale digital identities. Key Management Systems (KMS) provide flexibility by supporting diverse cryptographic keys and integration with various applications, facilitating adaptable security policies. While PKI excels in standardized identity validation for extensive networks, KMS focuses on dynamic key lifecycle management tailored to specific organizational needs.
Compliance and Regulatory Aspects
Public Key Infrastructure (PKI) provides a framework for managing digital certificates and public-key encryption, ensuring compliance with standards such as NIST, GDPR, and HIPAA by enabling strong identity verification and secure data transmission. Key Management Systems (KMS) focus on the lifecycle management of cryptographic keys, offering centralized control that supports regulatory requirements like FIPS 140-2 and PCI DSS for secure key storage, rotation, and access controls. Organizations must align PKI and KMS practices with industry-specific regulations to mitigate risks related to data breaches and maintain audit readiness.
Integration with Existing IT Ecosystems
Public Key Infrastructure (PKI) integrates with existing IT ecosystems by enabling secure digital certificate issuance and validation, facilitating encrypted communications and authentication across diverse network environments. Key Management Systems (KMS) focus on centralized control, storage, and lifecycle management of cryptographic keys, ensuring seamless integration with applications, cloud services, and hardware security modules (HSMs). Both PKI and KMS support interoperability with enterprise directories, identity access management (IAM) systems, and compliance frameworks to maintain robust security infrastructures.
Choosing Between PKI and KMS: Key Factors
Choosing between Public Key Infrastructure (PKI) and Key Management System (KMS) depends on organizational needs for secure key generation, storage, and distribution. PKI excels in environments requiring robust digital certificate issuance and authentication across diverse systems, while KMS offers centralized encryption key lifecycle management optimized for cloud and data protection. Evaluating factors such as scalability, compliance requirements, integration complexity, and the specific cryptographic use cases is essential for selecting the appropriate solution.
Public Key Infrastructure Infographic
 libterm.com
libterm.com