WS-Federation enables secure identity federation and single sign-on (SSO) across web applications, simplifying user authentication and access management. This protocol facilitates interoperability between different security realms by exchanging security tokens, improving seamless access for users across enterprises. Explore the full article to understand how WS-Federation can enhance your organization's identity strategy.
Table of Comparison
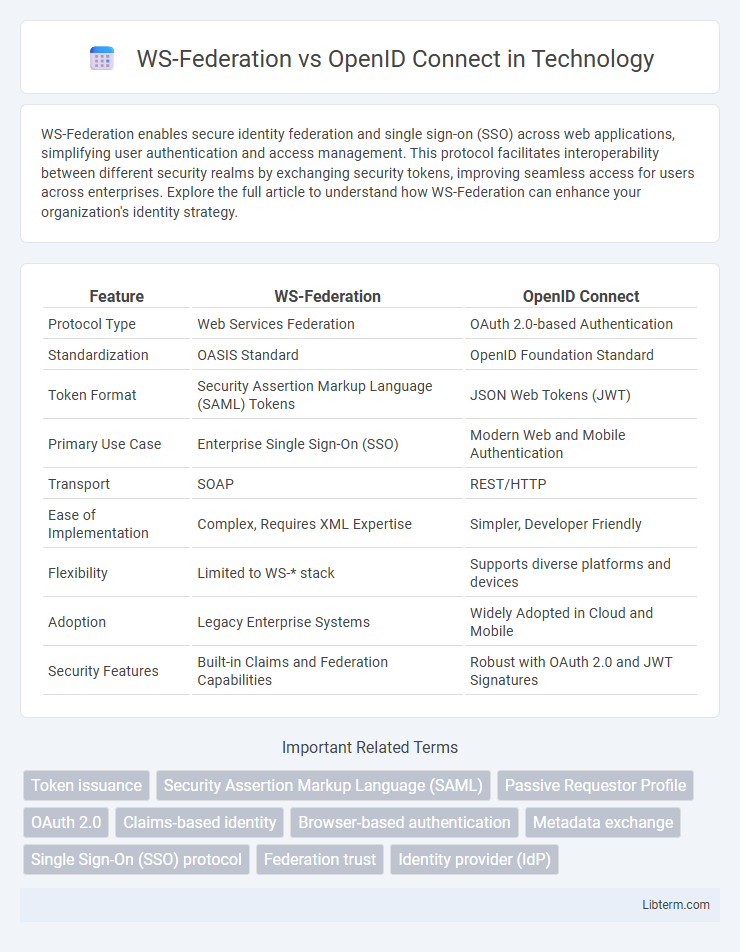
| Feature | WS-Federation | OpenID Connect |
|---|---|---|
| Protocol Type | Web Services Federation | OAuth 2.0-based Authentication |
| Standardization | OASIS Standard | OpenID Foundation Standard |
| Token Format | Security Assertion Markup Language (SAML) Tokens | JSON Web Tokens (JWT) |
| Primary Use Case | Enterprise Single Sign-On (SSO) | Modern Web and Mobile Authentication |
| Transport | SOAP | REST/HTTP |
| Ease of Implementation | Complex, Requires XML Expertise | Simpler, Developer Friendly |
| Flexibility | Limited to WS-* stack | Supports diverse platforms and devices |
| Adoption | Legacy Enterprise Systems | Widely Adopted in Cloud and Mobile |
| Security Features | Built-in Claims and Federation Capabilities | Robust with OAuth 2.0 and JWT Signatures |
Introduction to Identity Federation Protocols
WS-Federation and OpenID Connect are identity federation protocols that facilitate secure user authentication and single sign-on (SSO) across different domains. WS-Federation is built on the WS-* (Web Services) standards and primarily used within enterprise and Microsoft-based environments, leveraging Security Token Service (STS) for token issuance. OpenID Connect, an OAuth 2.0-based protocol, provides a modern, RESTful approach designed for web, mobile, and cloud applications, using JSON Web Tokens (JWT) for identity claims and enabling seamless integration with various identity providers.
What is WS-Federation?
WS-Federation is a web services specification designed to enable identity, authentication, and authorization across different security realms using a federated identity model. It facilitates the exchange of security tokens between identity providers and service providers, primarily in Microsoft environments, supporting single sign-on (SSO) and seamless access to multiple applications. WS-Federation leverages SOAP-based protocols and XML token formats such as SAML to manage user identity and trust relationships in enterprise and federated networks.
What is OpenID Connect?
OpenID Connect is an identity layer built on the OAuth 2.0 protocol that enables clients to verify the identity of users based on authentication performed by an authorization server. It provides standardized RESTful APIs for authentication and allows seamless integration of single sign-on (SSO) and federated identity across web and mobile applications. OpenID Connect supports JSON Web Tokens (JWT) for secure identity token transmission and is widely adopted for modern cloud-based identity management solutions.
Core Principles and Architecture Comparison
WS-Federation relies on security tokens and trust relationships between identity providers and service providers using SOAP-based communication, emphasizing federation through WS-* standards. OpenID Connect utilizes JSON Web Tokens (JWT) and OAuth 2.0 framework for authorization and authentication, promoting lightweight, RESTful, and modern web-friendly protocols. The architecture of WS-Federation centers on passive requestor profiles designed primarily for browser-based single sign-on, whereas OpenID Connect supports a broader range of clients, including mobile and native applications, through its flexible token issuance and user info endpoints.
Authentication Flows: WS-Federation vs OpenID Connect
WS-Federation employs passive request-response mechanisms primarily designed for browser-based Single Sign-On (SSO) using Security Assertion Markup Language (SAML) tokens, facilitating authentication via trust relationships between Identity Providers and relying parties. OpenID Connect, built on the OAuth 2.0 framework, utilizes JSON Web Tokens (JWT) and supports multiple authentication flows including Authorization Code, Implicit, and Hybrid flows, offering greater flexibility for native, web, and mobile applications. The OpenID Connect flows provide more modern, scalable, and RESTful methods for authentication and token exchange compared to WS-Federation's SOAP-based interaction model.
Security Mechanisms and Protocol Features
WS-Federation employs passive requestor profiles primarily for web browser single sign-on, relying on security tokens like SAML for authentication and supports WS-Security standards to ensure message integrity and confidentiality. OpenID Connect, built on OAuth 2.0, uses JSON Web Tokens (JWT) for secure identity assertion, leveraging RESTful APIs and supports features like token introspection, refresh tokens, and scopes for granular access control. The protocol design of OpenID Connect enables stronger resistance to replay and token substitution attacks through standardized token validation and signature verification mechanisms.
Interoperability and Ecosystem Support
WS-Federation offers solid interoperability within Microsoft-centric environments, leveraging existing Active Directory and Windows Integrated Authentication technologies. OpenID Connect provides broader ecosystem support across diverse platforms and modern web and mobile applications, built on the OAuth 2.0 framework for flexible, standardized authorization. OpenID Connect's widespread adoption by major identity providers enhances cross-platform integration, making it the preferred choice for multi-vendor and cloud-native identity solutions.
Use Cases and Industry Adoption
WS-Federation is primarily adopted in enterprise environments with legacy Microsoft technologies, facilitating single sign-on (SSO) across Active Directory Federation Services (ADFS) and on-premises applications. OpenID Connect enjoys widespread industry adoption, especially among modern web and mobile applications, thanks to its support for OAuth 2.0 and flexible JSON-based tokens. Use cases for WS-Federation often involve internal corporate applications and federated identity management in Microsoft-centric ecosystems, whereas OpenID Connect is favored for consumer-facing platforms requiring seamless social logins and secure API authorization.
Pros and Cons of WS-Federation and OpenID Connect
WS-Federation offers strong compatibility with legacy Microsoft environments and integrates seamlessly with Active Directory Federation Services (ADFS), making it ideal for enterprises invested in Windows infrastructure; however, it is less flexible and slower to adopt modern web standards compared to OpenID Connect. OpenID Connect provides a lightweight, RESTful protocol built on OAuth 2.0, delivering superior support for mobile and cloud applications, improved scalability, and broader industry adoption, but may require additional configuration for deep integration with on-premises Microsoft services. Choosing between WS-Federation and OpenID Connect depends on the existing IT ecosystem, with WS-Federation favoring Windows-centric setups and OpenID Connect excelling in diverse, modern application environments.
Choosing the Right Protocol for Your Needs
WS-Federation provides robust support for legacy Microsoft environments, ideal for enterprises heavily invested in Active Directory and on-premises solutions. OpenID Connect offers modern, scalable authentication using OAuth 2.0, making it suitable for web, mobile, and cloud-native applications requiring seamless SSO and API security. Selecting between WS-Federation and OpenID Connect depends on your infrastructure compatibility, security requirements, and future scalability needs.
WS-Federation Infographic
 libterm.com
libterm.com