Effective key management ensures secure generation, distribution, storage, and destruction of cryptographic keys to protect sensitive information from unauthorized access. It plays a critical role in maintaining data integrity, confidentiality, and compliance with security standards. Explore the rest of this article to understand how your organization can implement robust key management strategies.
Table of Comparison
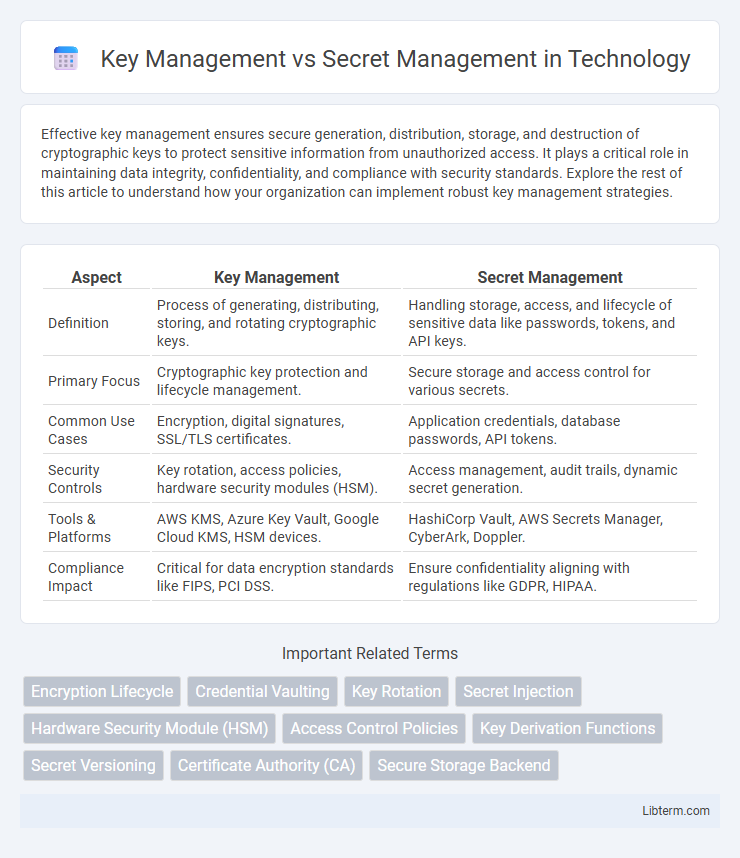
| Aspect | Key Management | Secret Management |
|---|---|---|
| Definition | Process of generating, distributing, storing, and rotating cryptographic keys. | Handling storage, access, and lifecycle of sensitive data like passwords, tokens, and API keys. |
| Primary Focus | Cryptographic key protection and lifecycle management. | Secure storage and access control for various secrets. |
| Common Use Cases | Encryption, digital signatures, SSL/TLS certificates. | Application credentials, database passwords, API tokens. |
| Security Controls | Key rotation, access policies, hardware security modules (HSM). | Access management, audit trails, dynamic secret generation. |
| Tools & Platforms | AWS KMS, Azure Key Vault, Google Cloud KMS, HSM devices. | HashiCorp Vault, AWS Secrets Manager, CyberArk, Doppler. |
| Compliance Impact | Critical for data encryption standards like FIPS, PCI DSS. | Ensure confidentiality aligning with regulations like GDPR, HIPAA. |
Introduction to Key Management and Secret Management
Key management involves the generation, distribution, storage, and lifecycle management of cryptographic keys used to secure data and communications in various systems. Secret management focuses on securely storing, accessing, and rotating sensitive information like passwords, API keys, and tokens to prevent unauthorized access. Both disciplines are essential for maintaining data confidentiality and integrity within cybersecurity frameworks.
Key Concepts in Key Management
Key Management revolves around the lifecycle of cryptographic keys, including their generation, distribution, storage, rotation, and destruction to ensure secure encryption and decryption processes. Critical concepts in Key Management include key hierarchy, symmetric and asymmetric keys, key escrow, and hardware security modules (HSMs) that protect keys from unauthorized access. Effective Key Management enforces strict access controls and auditing mechanisms to maintain data confidentiality and integrity throughout the key's usage.
Essentials of Secret Management
Secret management focuses on securely storing, distributing, and controlling access to sensitive data like API keys, passwords, and tokens within an application or infrastructure. It ensures secrets are encrypted at rest and in transit, audited for access, and rotated regularly to minimize security risks. Key management primarily deals with cryptographic keys used for data encryption, while secret management encompasses a broader range of confidential information crucial for authentication and authorization processes.
Differences Between Keys and Secrets
Keys are cryptographic artifacts primarily used for encryption, decryption, and digital signatures, ensuring data confidentiality and integrity. Secrets encompass broader sensitive information such as passwords, API tokens, and certificates that require secure storage and controlled access. Key management specifically deals with lifecycle processes like generation, rotation, and revocation of cryptographic keys, whereas secret management covers secure storage, distribution, and access policies for all types of sensitive credentials.
Typical Use Cases for Key Management
Key Management is essential in protecting cryptographic keys used for data encryption, digital signatures, and authentication across various industries. Typical use cases include securing enterprise-wide encryption keys for databases, managing keys for cloud service providers to ensure data confidentiality, and handling keys in hardware security modules (HSMs) to maintain tamper-resistant environments. This contrasts with Secret Management, which generally focuses on managing passwords, API tokens, and other sensitive credentials in software applications.
Typical Use Cases for Secret Management
Secret management typically involves storing, accessing, and distributing sensitive information such as API keys, passwords, tokens, and certificates in a secure manner. Common use cases include managing database credentials for applications, securing service-to-service authentication, and protecting configuration secrets in cloud environments. Efficient secret management reduces the risk of exposure and simplifies secret rotation and auditing processes essential for maintaining compliance and operational security.
Security Challenges in Key and Secret Management
Key management faces security challenges such as unauthorized access to cryptographic keys, inadequate key lifecycle control, and vulnerabilities in key storage that can lead to data breaches. Secret management struggles with protecting sensitive information like API keys and passwords from exposure, ensuring secure transmission, and preventing leakage through misconfigurations or insider threats. Both require robust encryption, strict access controls, and continuous monitoring to mitigate risks and maintain confidentiality and integrity.
Best Practices for Key and Secret Handling
Effective key management involves generating, distributing, storing, rotating, and revoking cryptographic keys securely to prevent unauthorized access and ensure data integrity. Secret management emphasizes the safe handling of sensitive information like API keys, passwords, and tokens using encrypted storage, access controls, and audit logging to minimize exposure risks. Best practices include employing hardware security modules (HSMs) for key protection, implementing least privilege access policies, automating secret rotation, and regularly auditing usage to maintain robust security posture.
Key Management and Secret Management Tools
Key management involves the generation, distribution, storage, and lifecycle management of cryptographic keys, ensuring secure encryption and decryption processes across various systems. Secret management tools specialize in securely storing, accessing, and auditing sensitive information such as passwords, API keys, and certificates to protect credentials from unauthorized access. Popular key management solutions include AWS KMS and Google Cloud KMS, while secret management tools like HashiCorp Vault and CyberArk provide comprehensive platforms for centralized secret storage and access control.
Choosing the Right Solution for Your Organization
Selecting the right solution between key management and secret management depends on your organization's specific security needs and operational scale. Key management systems focus on generating, storing, and controlling cryptographic keys, essential for encryption and digital signatures, whereas secret management systems handle sensitive data such as passwords, API keys, and tokens to ensure secure access and rotation. Evaluating factors like integration capabilities, compliance requirements, and automation support helps determine whether a comprehensive key management platform, a dedicated secret manager, or a hybrid approach best aligns with your organization's risk profile and infrastructure complexity.
Key Management Infographic
 libterm.com
libterm.com