Hashing is a technique used in computer science to convert data into a fixed-size string of characters, typically for faster data retrieval or secure information storage. It plays a critical role in various applications including password protection, data integrity verification, and efficient database indexing. Discover how hashing can enhance your digital security and streamline data management by exploring the rest of this article.
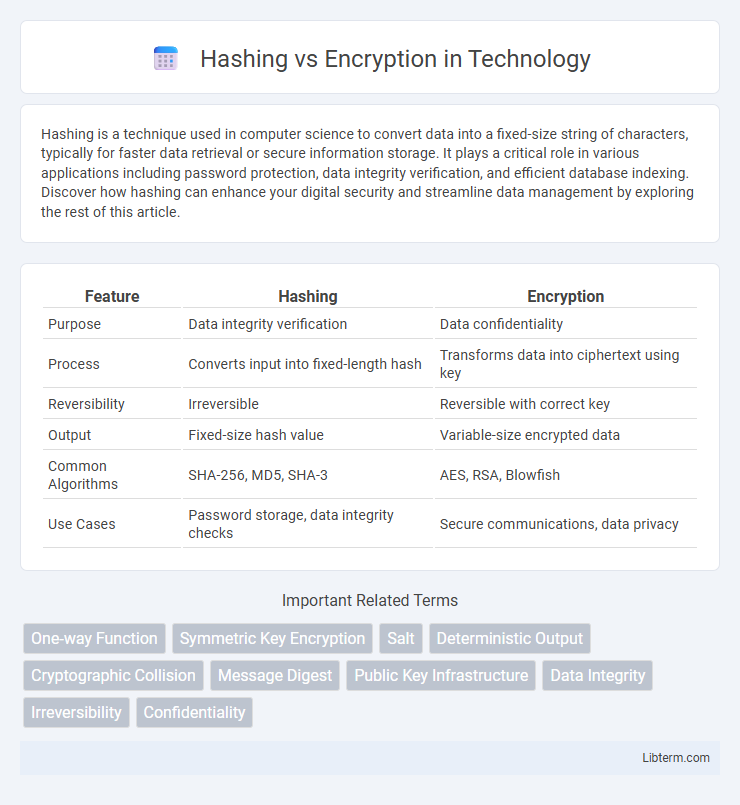
Table of Comparison
| Feature | Hashing | Encryption |
|---|---|---|
| Purpose | Data integrity verification | Data confidentiality |
| Process | Converts input into fixed-length hash | Transforms data into ciphertext using key |
| Reversibility | Irreversible | Reversible with correct key |
| Output | Fixed-size hash value | Variable-size encrypted data |
| Common Algorithms | SHA-256, MD5, SHA-3 | AES, RSA, Blowfish |
| Use Cases | Password storage, data integrity checks | Secure communications, data privacy |
Introduction to Hashing and Encryption
Hashing transforms input data into a fixed-size string of characters, typically a hash code, which is unique for different inputs and used for data integrity verification. Encryption converts plaintext into ciphertext using algorithms and keys to ensure data confidentiality and secure communication. Both methods serve distinct security purposes: hashing for verifying authenticity and encryption for protecting data privacy.
Key Differences Between Hashing and Encryption
Hashing transforms data into a fixed-size string of characters, which is irreversible and primarily used for data integrity verification, such as password storage. Encryption converts data into ciphertext using a key, enabling authorized parties to decrypt and restore the original information, ensuring confidentiality. The key difference lies in reversibility--encryption is reversible with the appropriate key, while hashing is a one-way process without reversal capability.
Core Principles of Hashing
Hashing transforms input data into a fixed-size string of characters, known as a hash value, using algorithms like SHA-256, ensuring data integrity by detecting alterations. Unlike encryption, hashing is a one-way process with no feasible method to reverse the output to its original form, making it ideal for password storage and data verification. Core principles emphasize determinism, fast computation, pre-image resistance, and collision resistance to maintain security and reliability.
Core Principles of Encryption
Encryption transforms readable data into an unreadable format using algorithms and keys to protect confidentiality and ensure secure communication. Core principles of encryption include data confidentiality, integrity, authentication, and non-repudiation, achieved through symmetric or asymmetric cryptographic methods. Unlike hashing, which produces a fixed-size digest primarily for data verification, encryption allows reversible data retrieval with the appropriate key, maintaining secure access control.
Use Cases for Hashing
Hashing is primarily used for data integrity verification, password storage, and digital signatures, ensuring that information remains unaltered and secure. It transforms input data into a fixed-size string of characters, which acts as a unique identifier for the original content without the possibility of reversing back to the original data. This makes hashing essential in applications like verifying file downloads, securing user credentials, and maintaining blockchain data immutability.
Use Cases for Encryption
Encryption secures sensitive data by transforming it into unreadable ciphertext, enabling confidential communication in applications like online banking, secure email, and e-commerce transactions. It protects data at rest and in transit, ensuring only authorized parties can access information such as credit card details, personal identity data, and proprietary business secrets. Encryption also plays a critical role in securing cloud storage, virtual private networks (VPNs), and regulatory compliance frameworks like GDPR and HIPAA.
Security Strengths of Hashing vs Encryption
Hashing provides data integrity by generating fixed-size, unique hash values that detect any alteration in the input, making it ideal for verifying data authenticity without revealing the original content. Encryption secures data confidentiality by transforming plaintext into ciphertext using algorithms and keys, allowing only authorized parties to decrypt and access the information. While hashing ensures tamper resistance through one-way functions, encryption offers controlled data access through reversible processes, each serving distinct but complementary security strengths.
Limitations and Vulnerabilities
Hashing is vulnerable to collision attacks where two different inputs produce the same hash, and it lacks reversibility, making it unsuitable for data retrieval. Encryption allows data recovery via decryption but is susceptible to brute force, key exposure, and cryptanalysis attacks. Both methods depend heavily on strong algorithms and secure key management to minimize security risks and limitations.
Real-World Examples and Applications
Hashing secures passwords by transforming input data into fixed-length hash values, ensuring user credentials remain protected in systems like bcrypt for authentication. Encryption converts data into ciphertext using algorithms such as AES or RSA, enabling secure communication in applications like HTTPS for online banking and email confidentiality. Digital signatures rely on hashing combined with encryption to verify document integrity and authenticity in legal and financial transactions.
Choosing the Right Technique for Your Needs
When choosing between hashing and encryption, consider that hashing is ideal for verifying data integrity and storing passwords securely since it produces a fixed-size digest that cannot be reversed. Encryption is better suited for protecting sensitive information that needs to be accessed and decrypted later, using algorithms such as AES or RSA. Selecting the right technique depends on whether the goal is data confidentiality, where encryption excels, or data verification and integrity, where hashing algorithms like SHA-256 are preferable.
Hashing Infographic
 libterm.com
libterm.com