Smart cards provide a secure method for data storage and authentication by embedding integrated circuits within plastic cards, commonly used in banking, identification, and access control. These cards enhance security through encryption and protect sensitive information from unauthorized access. Explore the rest of this article to understand how smart cards can safeguard your digital interactions effectively.
Table of Comparison
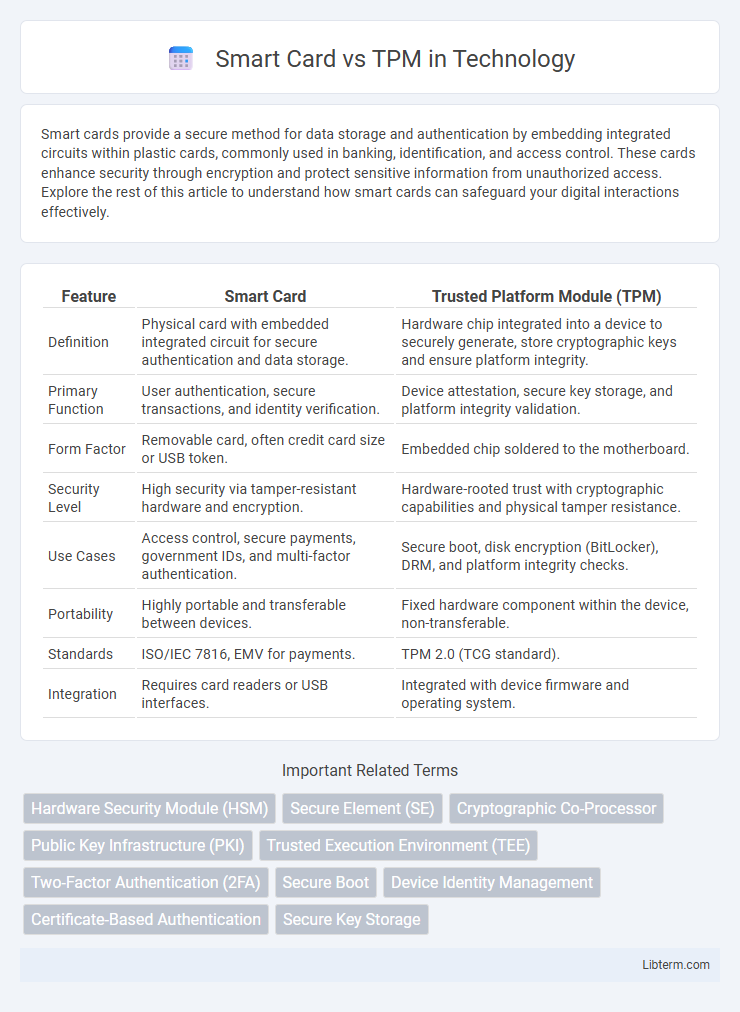
| Feature | Smart Card | Trusted Platform Module (TPM) |
|---|---|---|
| Definition | Physical card with embedded integrated circuit for secure authentication and data storage. | Hardware chip integrated into a device to securely generate, store cryptographic keys and ensure platform integrity. |
| Primary Function | User authentication, secure transactions, and identity verification. | Device attestation, secure key storage, and platform integrity validation. |
| Form Factor | Removable card, often credit card size or USB token. | Embedded chip soldered to the motherboard. |
| Security Level | High security via tamper-resistant hardware and encryption. | Hardware-rooted trust with cryptographic capabilities and physical tamper resistance. |
| Use Cases | Access control, secure payments, government IDs, and multi-factor authentication. | Secure boot, disk encryption (BitLocker), DRM, and platform integrity checks. |
| Portability | Highly portable and transferable between devices. | Fixed hardware component within the device, non-transferable. |
| Standards | ISO/IEC 7816, EMV for payments. | TPM 2.0 (TCG standard). |
| Integration | Requires card readers or USB interfaces. | Integrated with device firmware and operating system. |
Introduction to Smart Cards and TPM
Smart Cards are physical cards embedded with integrated circuits that securely store and process data for authentication, secure transactions, and access control. Trusted Platform Modules (TPM) are specialized microcontrollers designed to provide hardware-based security functions, such as cryptographic key generation, secure storage, and platform integrity verification, integrated directly into computing devices. Both Smart Cards and TPMs enhance digital security by leveraging hardware-level protections to prevent unauthorized access and tampering.
How Smart Cards Work: Key Features
Smart cards operate using embedded microprocessors that securely store cryptographic keys and execute encryption algorithms directly on the card, enabling strong user authentication and secure transactions. Key features include tamper-resistant hardware, secure key storage, and contact or contactless communication interfaces such as ISO/IEC 7816 or NFC standards. These elements ensure data integrity, prevent unauthorized access, and support multifactor authentication in environments like banking, government ID, and corporate security.
TPM Explained: Core Functions and Capabilities
Trusted Platform Module (TPM) is a specialized hardware chip designed for secure cryptographic operations, including key generation, storage, and platform integrity verification. TPM enables secure boot processes, hardware-based encryption, and ensures that sensitive data remains protected from unauthorized access or tampering. Compared to smart cards, TPM offers deeper integration with the device's firmware and operating system, providing robust security features critical for device authentication and data integrity.
Security Architecture: Smart Card vs TPM
Smart Card security architecture relies on a tamper-resistant chip that securely stores cryptographic keys and executes cryptographic operations within the card, isolating sensitive data from the host system and reducing exposure to malware. TPM (Trusted Platform Module) security architecture integrates a dedicated microcontroller within the device motherboard, providing hardware-based root of trust, secure key storage, and platform integrity measurement to protect boot processes and sensitive information. While Smart Cards excel in portability and user authentication, TPM offers deeper hardware integration for system-wide security enforcement and attestation capabilities.
Use Cases: When to Choose Smart Cards
Smart cards excel in secure physical and logical access control environments such as corporate buildings, government facilities, and healthcare institutions requiring multi-factor authentication. They are ideal for identity verification and secure transactions where portability and offline authentication are critical, including payment systems and public transportation. Smart cards are preferred over TPMs when users need a removable, user-controlled credential for secure access across different devices or locations.
Use Cases: When to Choose TPM
Trusted Platform Module (TPM) is ideal for device-level security in scenarios requiring hardware-based encryption, secure boot, and platform integrity verification, commonly used in enterprise environments for protecting sensitive data and credentials. Use TPM when implementing multi-factor authentication in laptops, servers, or IoT devices to safeguard cryptographic keys and enable secure storage for digital certificates. TPM is preferred over smart cards for embedded security solutions where ease of integration and tamper-resistant hardware features are critical.
Performance Comparison: Speed and Reliability
Smart Cards offer moderate speed reliant on external readers, with typical data transfer rates up to 424 kbps, while TPM (Trusted Platform Module) provides faster cryptographic operations integrated directly on the motherboard, enhancing overall system responsiveness. TPM exhibits superior reliability through hardware-based security with tamper-resistant design, minimizing failure rates compared to Smart Cards that depend on physical contact and external connections subject to wear. Performance benchmarks show TPMs excel in real-time encryption and decryption speeds critical for secure boot and key management, whereas Smart Cards serve better in portable, multi-application use cases despite slightly higher latency.
Integration and Compatibility Considerations
Smart Cards offer broad compatibility with various authentication systems through standardized interfaces like PC/SC and ISO/IEC 7816, enabling seamless integration into existing security infrastructures. TPMs are embedded hardware modules designed to integrate tightly with a device's motherboard, providing cryptographic functions and secure key storage but requiring specific firmware and software support for compatibility. Organizations must evaluate their infrastructure's hardware and software environment to determine whether the plug-and-play nature of Smart Cards or the embedded security model of TPMs best aligns with their integration and compatibility requirements.
Cost Analysis: Smart Card vs TPM
Smart Card solutions typically have lower initial costs due to cheaper hardware and mass production capabilities, while TPM modules are integrated into motherboards, increasing overall device expenses but reducing external component costs. Maintenance and deployment costs for Smart Cards can be higher because of the need for card issuance, management, and reader devices, whereas TPMs benefit from seamless hardware integration, lowering operational overhead. Total cost of ownership favors TPMs in large-scale enterprise environments due to enhanced security features and reduced administrative efforts despite a higher upfront investment.
Future Trends in Secure Authentication Technologies
Future trends in secure authentication technologies highlight the increasing integration of Trusted Platform Modules (TPM) within device hardware to provide robust, tamper-resistant cryptographic key storage, outperforming traditional smart cards in flexibility and scalability. Advancements in TPM 2.0 standards enable seamless support for multi-factor and biometric authentication, positioning TPM as a cornerstone for secure identity management in IoT ecosystems and cloud environments. Meanwhile, smart cards continue evolving with contactless and NFC capabilities, but TPM's embedded nature and firmware update mechanisms drive broader adoption in next-generation trusted computing frameworks.
Smart Card Infographic
 libterm.com
libterm.com