Biometrics refers to the measurement and analysis of unique physical or behavioral characteristics, such as fingerprints, facial recognition, or voice patterns, to verify an individual's identity. This technology enhances security by providing reliable and convenient authentication methods, increasingly integrated into smartphones, access control, and financial services. Explore the rest of the article to understand how biometrics can safeguard your personal data and transform identity verification.
Table of Comparison
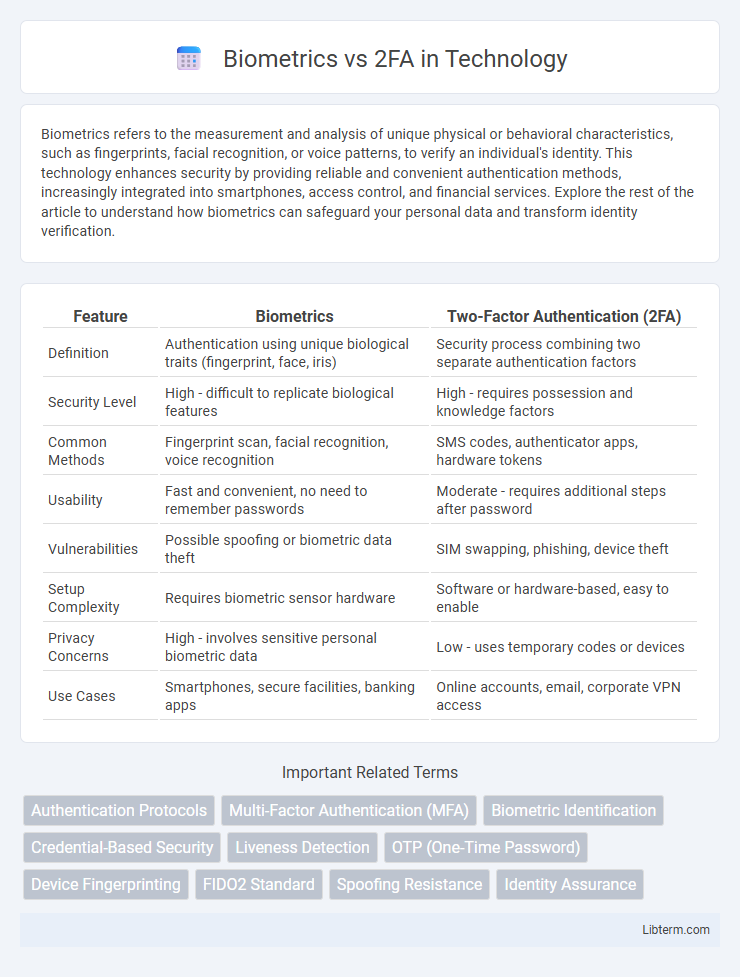
| Feature | Biometrics | Two-Factor Authentication (2FA) |
|---|---|---|
| Definition | Authentication using unique biological traits (fingerprint, face, iris) | Security process combining two separate authentication factors |
| Security Level | High - difficult to replicate biological features | High - requires possession and knowledge factors |
| Common Methods | Fingerprint scan, facial recognition, voice recognition | SMS codes, authenticator apps, hardware tokens |
| Usability | Fast and convenient, no need to remember passwords | Moderate - requires additional steps after password |
| Vulnerabilities | Possible spoofing or biometric data theft | SIM swapping, phishing, device theft |
| Setup Complexity | Requires biometric sensor hardware | Software or hardware-based, easy to enable |
| Privacy Concerns | High - involves sensitive personal biometric data | Low - uses temporary codes or devices |
| Use Cases | Smartphones, secure facilities, banking apps | Online accounts, email, corporate VPN access |
Introduction to Authentication Methods
Authentication methods are essential for verifying user identities and protecting sensitive data, with biometrics and two-factor authentication (2FA) being prominent techniques. Biometrics use unique physiological traits such as fingerprints, facial recognition, or iris scans to grant access, offering a highly secure and convenient user experience. Two-factor authentication combines something the user knows, like a password, with something they have or receive, such as a text message code or authentication app, to enhance security by adding an extra verification layer.
What is Biometrics?
Biometrics refers to the measurement and analysis of unique physical or behavioral characteristics, such as fingerprints, facial recognition, iris scans, or voice patterns, used to verify an individual's identity. Unlike traditional 2FA methods that rely on something you know (password) and something you have (token or smartphone), biometric authentication uses intrinsic traits that are difficult to replicate or steal. This technology enhances security by providing a seamless and highly personalized form of access control in various applications, including mobile devices, banking, and government systems.
Understanding Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) enhances security by requiring users to provide two distinct forms of identification: something they know (password) and something they have or are (biometrics or tokens). Biometrics, such as fingerprint or facial recognition, serve as the second factor by verifying unique physical traits, making unauthorized access more difficult. Implementing 2FA with biometric verification significantly reduces the risk of account breaches compared to single-factor authentication methods.
How Biometrics Works in Security
Biometrics in security relies on unique physiological or behavioral traits such as fingerprints, facial recognition, and voice patterns to verify identity. Biometric systems capture and analyze these traits using sensors and algorithms, then compare the data against stored templates for authentication. This method offers enhanced security by reducing reliance on passwords and minimizing risks of phishing or credential theft common in traditional two-factor authentication (2FA) approaches.
Common Types of 2FA
Common types of 2FA include SMS codes, authenticator apps, hardware tokens, and biometric verification. Biometrics, such as fingerprint scans and facial recognition, serve as a secure 2FA method that leverages unique physical traits. Combining biometrics with traditional 2FA enhances security by requiring both something you are and something you have or know.
Security Advantages of Biometrics
Biometrics provides enhanced security advantages over traditional 2FA by using unique physiological traits such as fingerprints, facial recognition, or iris scans that are difficult to replicate or steal. Unlike 2FA methods relying on passwords or SMS codes vulnerable to phishing and SIM swapping attacks, biometric authentication offers a higher level of identity verification and fraud prevention. Integration of biometrics also reduces risks associated with credential sharing or loss, ensuring stronger protection for sensitive data and secure access control.
Strengths and Weaknesses of 2FA
Two-factor authentication (2FA) enhances security by requiring users to provide two distinct forms of identification, typically combining something they know (password) with something they have (a mobile device) or something they are (biometric data). Its primary strength lies in reducing the risk of unauthorized access due to compromised passwords, yet 2FA's weaknesses include vulnerability to phishing attacks, SIM swapping, and reliance on the user's device availability and security. Despite these limitations, 2FA remains a widely adopted security method that significantly improves protection compared to single-factor authentication.
Biometrics vs 2FA: Comparison Table
Biometrics and Two-Factor Authentication (2FA) provide distinct security approaches; biometrics use unique physical traits like fingerprints or facial recognition, while 2FA combines two separate authentication factors such as passwords and one-time codes. A comparison table highlights that biometrics offer faster, more user-friendly access but may raise privacy and spoofing concerns; 2FA delivers stronger protection by requiring multiple credentials but can be less convenient and reliant on device availability. Organizations often select authentication methods based on risk tolerance, user experience priorities, and compliance requirements, balancing security effectiveness with operational impact.
Use Cases: When to Choose Biometrics or 2FA
Biometrics excel in scenarios requiring fast, convenient, and user-friendly authentication such as unlocking smartphones, accessing secure facilities, or time-sensitive transactions where identity verification must be seamless. Two-factor authentication (2FA) is more suitable for high-security environments like online banking, corporate VPN access, or cloud services, where combining something the user knows (password) with something they have (device) significantly reduces the risk of unauthorized access. Choosing between biometrics and 2FA depends on balancing security needs with usability, often integrating both for layered protection in critical applications.
Future Trends in Authentication Technologies
Biometrics and 2FA represent evolving frontiers in authentication, with biometrics leveraging unique physiological traits such as fingerprints and facial recognition to enhance security. Future trends indicate a shift towards multi-modal biometric systems that combine voice, iris, and behavioral patterns, offering more seamless and robust identity verification. Integration of AI-driven continuous authentication within 2FA frameworks is expected to further reduce fraud, enabling adaptive security measures that respond dynamically to user behavior and threat levels.
Biometrics Infographic
 libterm.com
libterm.com