Post-quantum key exchange methods protect your communications from future quantum computer attacks by using algorithms resistant to quantum-based decryption. These cryptographic schemes ensure secure data transmission even when quantum computers become capable of breaking traditional encryption. Explore the article to understand how post-quantum key exchange secures your digital interactions in the quantum era.
Table of Comparison
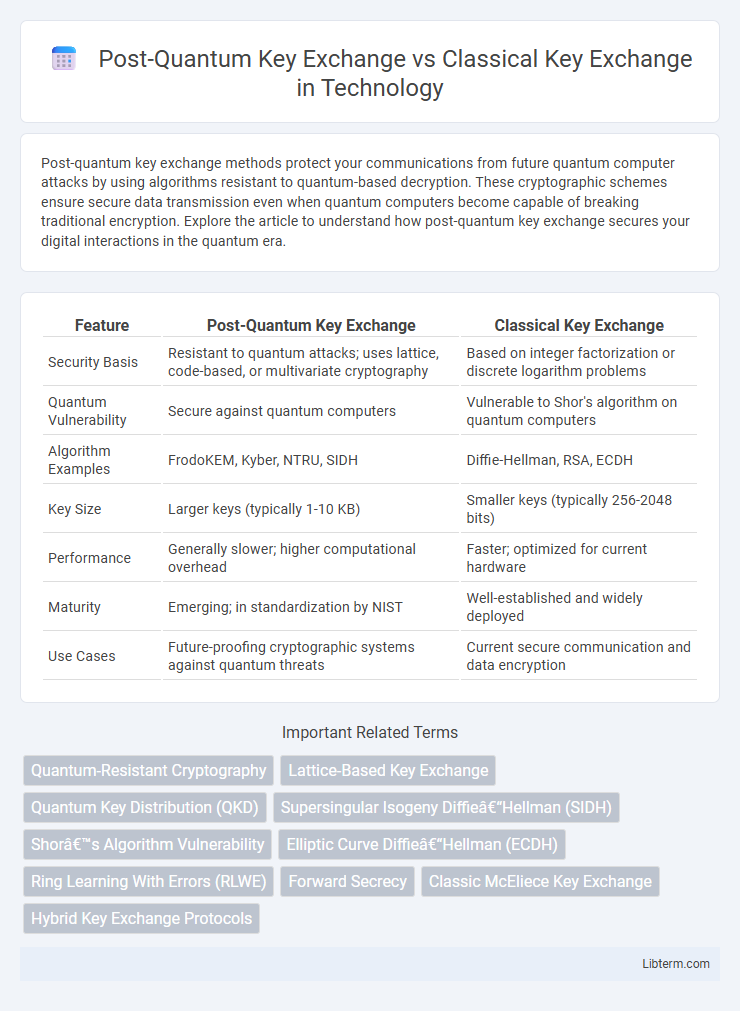
| Feature | Post-Quantum Key Exchange | Classical Key Exchange |
|---|---|---|
| Security Basis | Resistant to quantum attacks; uses lattice, code-based, or multivariate cryptography | Based on integer factorization or discrete logarithm problems |
| Quantum Vulnerability | Secure against quantum computers | Vulnerable to Shor's algorithm on quantum computers |
| Algorithm Examples | FrodoKEM, Kyber, NTRU, SIDH | Diffie-Hellman, RSA, ECDH |
| Key Size | Larger keys (typically 1-10 KB) | Smaller keys (typically 256-2048 bits) |
| Performance | Generally slower; higher computational overhead | Faster; optimized for current hardware |
| Maturity | Emerging; in standardization by NIST | Well-established and widely deployed |
| Use Cases | Future-proofing cryptographic systems against quantum threats | Current secure communication and data encryption |
Introduction to Key Exchange Mechanisms
Key exchange mechanisms establish a secure communication channel by enabling parties to share encryption keys confidentially. Classical key exchange protocols, such as Diffie-Hellman and RSA, rely on computational hardness assumptions vulnerable to quantum computing attacks. Post-quantum key exchange protocols use quantum-resistant algorithms like lattice-based and code-based cryptography to ensure security against quantum adversaries.
Overview of Classical Key Exchange Protocols
Classical key exchange protocols such as Diffie-Hellman and RSA rely on mathematical problems like integer factorization and discrete logarithms, which are currently computationally feasible to secure communication. These protocols use asymmetric cryptography to enable two parties to securely generate a shared secret over an insecure channel. The vulnerability of classical key exchanges to quantum attacks, specifically from Shor's algorithm, emphasizes the need for transitioning to post-quantum cryptographic methods.
What is Post-Quantum Key Exchange?
Post-Quantum Key Exchange refers to cryptographic protocols designed to secure data transmission against threats posed by quantum computers, which can break classical encryption algorithms like RSA and ECC. It uses mathematical problems believed to be resistant to quantum attacks, such as lattice-based, hash-based, or multivariate polynomial problems, to establish shared secret keys between parties. This emerging technology aims to future-proof secure communication by ensuring confidentiality even in the presence of powerful quantum adversaries.
Cryptographic Vulnerabilities in a Quantum Era
Post-quantum key exchange protocols address cryptographic vulnerabilities inherent in classical algorithms, such as RSA and ECC, which are susceptible to quantum attacks like Shor's algorithm. Quantum-resistant algorithms like lattice-based, code-based, and multivariate polynomial schemes offer robust security against quantum adversaries by relying on mathematical problems that remain hard for quantum computers. Transitioning to post-quantum key exchange is critical for safeguarding data confidentiality and integrity in the imminent quantum computing landscape.
Algorithmic Foundations: Classical vs Post-Quantum
Classical key exchange algorithms, such as Diffie-Hellman and RSA, rely on the computational difficulty of problems like integer factorization and discrete logarithms, which are efficiently solvable by quantum computers using Shor's algorithm. Post-quantum key exchange protocols leverage mathematical structures resistant to quantum attacks, including lattice-based, code-based, and multivariate polynomial problems, ensuring security against both classical and quantum adversaries. These post-quantum algorithms prioritize hardness assumptions unrelated to factoring or discrete logs, forming the foundation for next-generation cryptographic standards in a quantum computing era.
Performance and Efficiency Comparison
Post-quantum key exchange protocols, leveraging lattice-based or code-based cryptography, exhibit increased computational complexity compared to classical Diffie-Hellman or RSA methods, leading to higher processing times and larger key sizes. Despite this overhead, post-quantum schemes ensure security against quantum attacks, with ongoing optimizations improving their performance to approach classical efficiency levels. Energy consumption and bandwidth requirements remain higher in post-quantum exchanges, but advancements in algorithm engineering and hardware acceleration are narrowing the efficiency gap.
Security Guarantees Against Quantum Attacks
Post-Quantum Key Exchange protocols leverage lattice-based, code-based, or multivariate polynomial cryptosystems designed to withstand attacks from quantum computers, unlike classical key exchange methods such as RSA or Diffie-Hellman which are vulnerable to Shor's algorithm. These post-quantum schemes provide security guarantees by relying on mathematical problems believed to be hard even for quantum adversaries, ensuring confidentiality in a post-quantum era. Transitioning to post-quantum key exchanges is critical for maintaining long-term data security as quantum computing capabilities advance.
Real-World Applications and Industry Adoption
Post-Quantum Key Exchange protocols, such as those based on lattice cryptography and supersingular isogeny, offer resistance to attacks from quantum computers, positioning them as critical for securing future communications in industries like finance, government, and healthcare. Classical Key Exchange methods, including RSA and Diffie-Hellman, remain dominant due to their established infrastructure and efficiency but face obsolescence risks as quantum computing advances. Industry adoption of post-quantum algorithms is accelerating through standards bodies like NIST, with pilot deployments in cloud services and IoT devices demonstrating practical feasibility and driving a gradual transition in real-world cryptographic ecosystems.
Migration Challenges to Post-Quantum Key Exchange
Migrating from Classical Key Exchange protocols such as Diffie-Hellman or RSA to Post-Quantum Key Exchange (PQKE) algorithms involves complex challenges including the integration of quantum-resistant algorithms like lattice-based or code-based cryptography into existing systems without compromising performance or compatibility. Key issues include managing increased computational overhead, ensuring interoperability with legacy infrastructure, and securing transitional states where both classical and quantum-safe algorithms operate concurrently. Organizations must carefully plan phased deployments and rigorous testing to mitigate risks during the migration to PQKE, especially given the evolving standards from bodies like NIST.
Future Outlook for Secure Communications
Post-quantum key exchange protocols leverage quantum-resistant algorithms such as lattice-based, hash-based, and code-based cryptography to secure communications against future quantum computing threats. Classical key exchange methods, including RSA and ECC, rely on mathematical problems vulnerable to quantum attacks like Shor's algorithm, posing significant risks to long-term data confidentiality. As quantum computers advance, integrating post-quantum cryptography into existing infrastructure becomes critical for ensuring resilient, future-proof secure communication frameworks.
Post-Quantum Key Exchange Infographic
 libterm.com
libterm.com