Asymmetric encryption uses a pair of keys--a public key for encrypting data and a private key for decrypting it--ensuring secure communication even over unsecured channels. This method enhances data confidentiality, authentication, and integrity in various applications, from email security to digital signatures. Discover how asymmetric encryption works and why it is essential for protecting your information in the digital age by reading the full article.
Table of Comparison
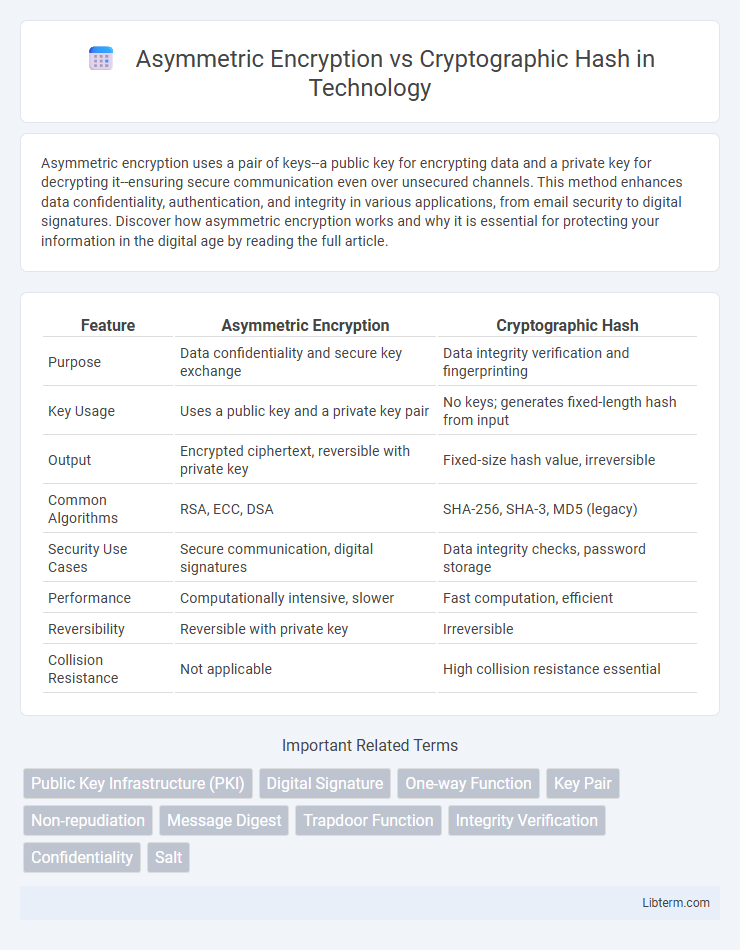
| Feature | Asymmetric Encryption | Cryptographic Hash |
|---|---|---|
| Purpose | Data confidentiality and secure key exchange | Data integrity verification and fingerprinting |
| Key Usage | Uses a public key and a private key pair | No keys; generates fixed-length hash from input |
| Output | Encrypted ciphertext, reversible with private key | Fixed-size hash value, irreversible |
| Common Algorithms | RSA, ECC, DSA | SHA-256, SHA-3, MD5 (legacy) |
| Security Use Cases | Secure communication, digital signatures | Data integrity checks, password storage |
| Performance | Computationally intensive, slower | Fast computation, efficient |
| Reversibility | Reversible with private key | Irreversible |
| Collision Resistance | Not applicable | High collision resistance essential |
Introduction to Asymmetric Encryption and Cryptographic Hash
Asymmetric encryption uses a pair of keys--public and private--to securely encrypt and decrypt data, enabling secure communication without sharing secret keys. Cryptographic hash functions generate fixed-size, unique hash values from variable-length input data, ensuring data integrity and authentication. Both mechanisms form pillars of modern cybersecurity, with asymmetric encryption enabling secure data exchange and cryptographic hashes verifying data integrity.
Core Principles: How Asymmetric Encryption Works
Asymmetric encryption relies on a pair of mathematically related keys: a public key for encryption and a private key for decryption, ensuring data confidentiality and secure communication. The core principle involves encrypting plaintext with the recipient's public key, making the ciphertext indecipherable without the corresponding private key. This cryptographic method supports digital signatures and key exchange protocols, distinguishing it from cryptographic hash functions that create fixed-size message digests for data integrity verification.
Core Principles: How Cryptographic Hash Functions Work
Cryptographic hash functions generate fixed-size output called a hash value by processing input data through a one-way mathematical algorithm, ensuring data integrity and authenticity. These functions are deterministic, collision-resistant, and produce unique outputs even with minor input changes, making it impossible to reverse-engineer the original data. Unlike asymmetric encryption, which uses key pairs for secure communication, cryptographic hashes primarily verify data consistency without revealing the original content.
Key Differences Between Asymmetric Encryption and Hash Functions
Asymmetric encryption uses a pair of keys--a public key for encryption and a private key for decryption--to securely transmit data, whereas cryptographic hash functions generate a fixed-size hash value from input data to ensure integrity without requiring keys. Asymmetric encryption enables confidentiality and authentication through key pairs, while hash functions provide data integrity and verification by producing unique, irreversible hash outputs. The key difference lies in the purpose: encryption transforms data to maintain secrecy, while hashing creates a fingerprint to verify data has not been altered.
Use Cases for Asymmetric Encryption
Asymmetric encryption is primarily used in secure communication protocols such as SSL/TLS for establishing encrypted connections and in digital signatures to verify authenticity and integrity of messages. It enables secure key exchange over untrusted networks, allowing users to encrypt data with a public key that only the intended recipient can decrypt using their private key. This method is essential for applications like email encryption, secure file transfer, and blockchain transaction validation.
Use Cases for Cryptographic Hash Functions
Cryptographic hash functions play a critical role in ensuring data integrity, verifying digital signatures, and securely storing passwords by generating fixed-size hash values from arbitrary input data. They are widely used in blockchain technology to link blocks securely and in message authentication codes (MACs) to confirm data authenticity without revealing the original content. Unlike asymmetric encryption, which enables secure key exchange and confidential communication, cryptographic hashes focus on producing unique data fingerprints for validation and tamper detection.
Security Strengths and Limitations
Asymmetric encryption uses a pair of public and private keys to secure data, offering strong confidentiality and authentication, but its computational intensity limits efficiency in large data encryption. Cryptographic hash functions provide data integrity and verify authenticity by generating fixed-size hash values from input data, though they do not offer confidentiality or reversible encryption. Both methods have distinct security strengths: asymmetric encryption safeguards data transmission securely, while hashes ensure data has not been altered, but neither can fully substitute the other in comprehensive cryptographic systems.
Performance and Efficiency Comparison
Asymmetric encryption requires significantly more computational power and time compared to cryptographic hashing, making it less efficient for processing large volumes of data. Cryptographic hash functions are optimized for speed and performance, producing fixed-size outputs quickly, which is ideal for data integrity verification and digital signatures. The performance overhead of asymmetric encryption stems from complex mathematical operations like modular exponentiation, while hashing involves simpler, faster transformations.
Common Algorithms and Real-World Applications
Asymmetric encryption utilizes paired public and private keys to secure data, with common algorithms including RSA, ECC, and DSA, enabling secure key exchange and digital signatures in email encryption, VPNs, and secure web browsing (SSL/TLS). Cryptographic hash functions like SHA-256, MD5, and SHA-3 generate fixed-size outputs from variable input data, ensuring data integrity and authenticity in password storage, blockchain, and digital fingerprinting. Both technologies underpin modern cybersecurity frameworks by providing confidentiality through encryption and integrity via hashing, supporting robust authentication and secure communications.
Choosing the Right Technique for Your Needs
Asymmetric encryption provides secure communication by using a pair of public and private keys, ideal for data confidentiality and digital signatures in scenarios like email encryption and secure transactions. Cryptographic hash functions generate fixed-size, unique digests from input data, ensuring data integrity and authentication without revealing original content, commonly used in password storage and file verification. Selecting between asymmetric encryption and cryptographic hash depends on whether data confidentiality or integrity is the priority, with asymmetric encryption suited for secure data exchange and hashes for verifying data authenticity.
Asymmetric Encryption Infographic
 libterm.com
libterm.com