Kerberos is a network authentication protocol designed to provide strong security for verifying user identities through secret-key cryptography. It operates by issuing time-stamped tickets to users, enabling seamless access to multiple services without repeatedly entering passwords. Explore the full article to understand how Kerberos can enhance your organization's security infrastructure.
Table of Comparison
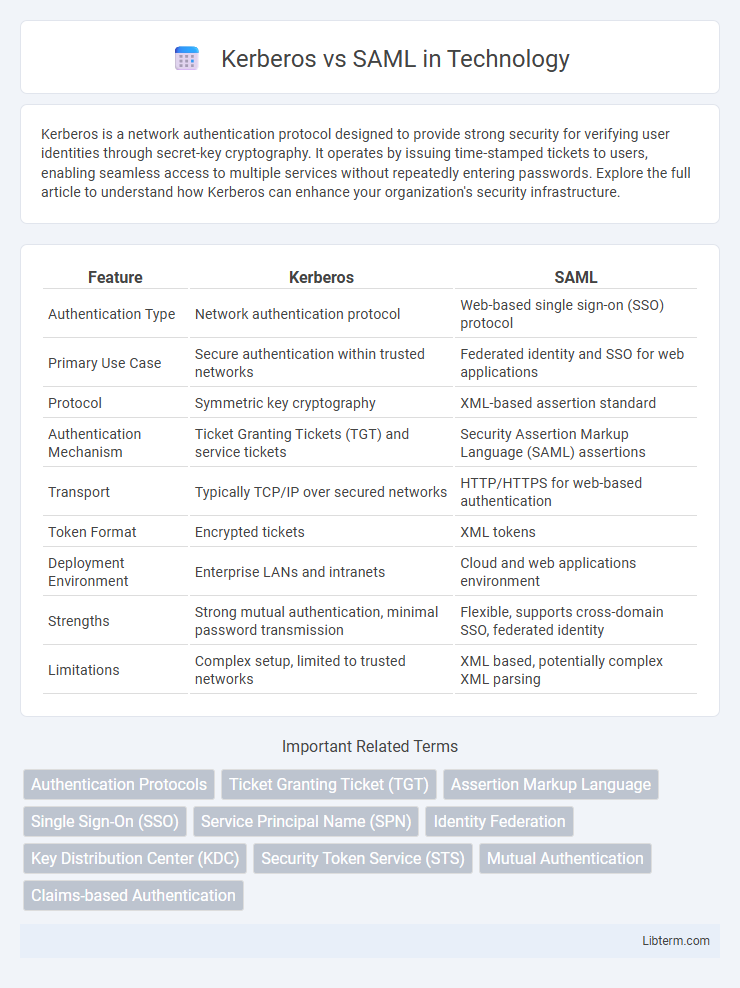
| Feature | Kerberos | SAML |
|---|---|---|
| Authentication Type | Network authentication protocol | Web-based single sign-on (SSO) protocol |
| Primary Use Case | Secure authentication within trusted networks | Federated identity and SSO for web applications |
| Protocol | Symmetric key cryptography | XML-based assertion standard |
| Authentication Mechanism | Ticket Granting Tickets (TGT) and service tickets | Security Assertion Markup Language (SAML) assertions |
| Transport | Typically TCP/IP over secured networks | HTTP/HTTPS for web-based authentication |
| Token Format | Encrypted tickets | XML tokens |
| Deployment Environment | Enterprise LANs and intranets | Cloud and web applications environment |
| Strengths | Strong mutual authentication, minimal password transmission | Flexible, supports cross-domain SSO, federated identity |
| Limitations | Complex setup, limited to trusted networks | XML based, potentially complex XML parsing |
Introduction to Kerberos and SAML
Kerberos is a network authentication protocol designed to provide secure user authentication through secret-key cryptography and a trusted third party known as the Key Distribution Center (KDC). Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, primarily used for single sign-on (SSO) in web applications. Both Kerberos and SAML facilitate identity verification, but Kerberos operates mainly within internal networks while SAML enables federated identity across different domains.
Core Concepts and Architecture
Kerberos operates on a ticket-based authentication protocol that uses secret-key cryptography and a trusted third-party Key Distribution Center (KDC) to validate user identities within a secure network, primarily designed for single sign-on in internal environments. SAML (Security Assertion Markup Language) relies on XML-based assertions and an identity provider-service provider model to enable federated single sign-on across different security domains using browser-based interactions. The Kerberos architecture consists of client, KDC (containing the Authentication Server and Ticket Granting Server), and service servers, while SAML involves identity providers, service providers, and a reliance on XML messages for authentication and authorization data exchange.
Authentication Workflow: Kerberos Explained
Kerberos authentication workflow involves a trusted third party called the Key Distribution Center (KDC), which issues Ticket Granting Tickets (TGT) to clients after verifying their credentials. Clients use the TGT to request service tickets for access to specific resources, enabling secure, mutual authentication without transmitting passwords. This ticket-based system contrasts with SAML's reliance on XML-based assertions and browser redirects for federated identity verification.
Authentication Workflow: SAML Explained
SAML (Security Assertion Markup Language) uses an XML-based authentication workflow where the identity provider (IdP) issues a digitally signed assertion to the service provider (SP) after user authentication. The SP relies on the SAML assertion to grant access without repeatedly prompting for credentials, enabling single sign-on (SSO) across multiple domains. This federated authentication process contrasts with Kerberos, which uses ticket-based credentials within a single, trusted network domain.
Key Features and Differences
Kerberos is a network authentication protocol that uses secret-key cryptography and tickets to enable secure user verification within a single domain, emphasizing mutual authentication and single sign-on (SSO) capabilities primarily in Windows environments. SAML (Security Assertion Markup Language) is an XML-based open standard designed for exchanging authentication and authorization data between identity providers and service providers, enabling cross-domain SSO, especially for web applications and federated identity management. Key differences include Kerberos' focus on internal network security using symmetric key cryptography versus SAML's use of digital signatures with XML-based assertions for federated authentication across multiple domains and platforms.
Security Mechanisms and Protocols
Kerberos uses a ticket-based authentication protocol relying on secret-key cryptography to securely verify user identities within a trusted network, preventing replay attacks through timestamped tickets issued by the Key Distribution Center (KDC). SAML employs XML-based assertions and relies on public key infrastructure (PKI) for secure exchange of authentication and authorization data between identity providers and service providers, leveraging digital signatures and encryption to ensure message integrity and confidentiality. While Kerberos excels in internal network authentication with symmetric keys, SAML is optimized for federated single sign-on (SSO) across different domains using standardized XML protocols and security tokens.
Use Cases: When to Use Kerberos
Kerberos is ideal for environments requiring strong, mutual authentication in internal networks, especially within Windows-based Active Directory domains. It excels in scenarios where secure, single sign-on (SSO) access to services such as file shares, printers, and intranet applications is needed without repeatedly prompting users for credentials. Organizations prioritizing confidentiality and integrity in local network authentication often choose Kerberos for its ticket-based protocol and resistance to replay attacks.
Use Cases: When to Use SAML
SAML is ideal for single sign-on (SSO) in web-based applications, particularly in enterprise environments requiring secure federated identity management across multiple domains. It excels in scenarios where users access cloud services or partner portals, enabling seamless authentication without repeatedly entering credentials. SAML's trust model supports cross-organization authentication, making it effective for integrating third-party SaaS platforms and business-to-business (B2B) collaborations.
Performance, Scalability, and Compatibility
Kerberos offers high performance through symmetric-key cryptography, making it efficient for frequent authentication in large, homogeneous environments, while SAML relies on XML-based tokens that can introduce latency and complexity, affecting speed. Scalability in Kerberos is limited by its dependency on a centralized Key Distribution Center (KDC), whereas SAML supports scalable single sign-on (SSO) across multiple domains and diverse platforms without a single point of failure. Compatibility-wise, Kerberos is primarily designed for internal network authentication in Windows and UNIX systems, whereas SAML is broadly compatible with web-based applications and cloud services, enabling seamless integration across different identity providers and service providers.
Conclusion: Choosing Between Kerberos and SAML
Kerberos excels in secure, single sign-on authentication within internal networks, leveraging ticket-based protocols for efficient, encrypted access control. SAML is ideal for federated identity management across diverse web applications and organizational boundaries, enabling seamless user authentication via XML-based assertions. Selecting between Kerberos and SAML depends on the environment's architecture, security requirements, and whether the use case favors intranet ticketing or cross-domain web authentication.
Kerberos Infographic
 libterm.com
libterm.com