Network segmentation enhances cybersecurity by dividing a larger network into smaller, isolated segments to limit unauthorized access and contain potential threats. This technique improves performance and simplifies network management by reducing traffic congestion and isolating sensitive data. Discover how network segmentation can protect Your digital infrastructure and boost efficiency by reading the rest of the article.
Table of Comparison
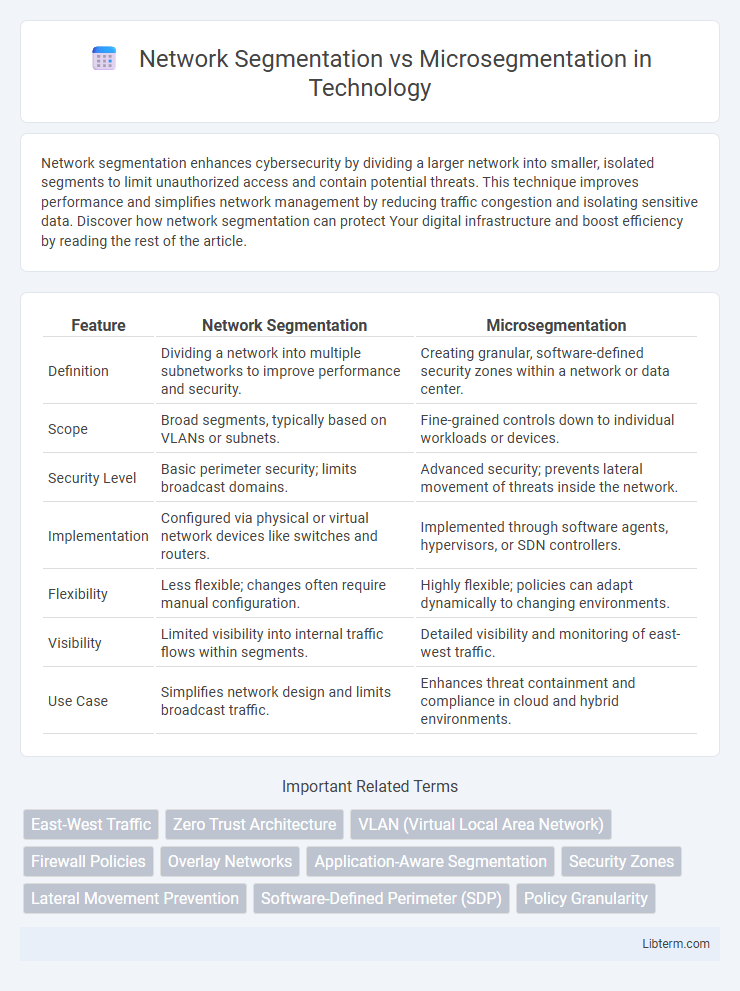
| Feature | Network Segmentation | Microsegmentation |
|---|---|---|
| Definition | Dividing a network into multiple subnetworks to improve performance and security. | Creating granular, software-defined security zones within a network or data center. |
| Scope | Broad segments, typically based on VLANs or subnets. | Fine-grained controls down to individual workloads or devices. |
| Security Level | Basic perimeter security; limits broadcast domains. | Advanced security; prevents lateral movement of threats inside the network. |
| Implementation | Configured via physical or virtual network devices like switches and routers. | Implemented through software agents, hypervisors, or SDN controllers. |
| Flexibility | Less flexible; changes often require manual configuration. | Highly flexible; policies can adapt dynamically to changing environments. |
| Visibility | Limited visibility into internal traffic flows within segments. | Detailed visibility and monitoring of east-west traffic. |
| Use Case | Simplifies network design and limits broadcast traffic. | Enhances threat containment and compliance in cloud and hybrid environments. |
Introduction to Network Segmentation and Microsegmentation
Network segmentation divides a computer network into multiple subnetworks to improve performance and security by isolating traffic within distinct zones. Microsegmentation enhances this approach by applying granular security controls at the workload or application level within those segments, reducing the attack surface and preventing lateral movement of threats. This fine-grained isolation is essential for protecting sensitive data in modern, dynamic environments such as cloud infrastructures and data centers.
Core Concepts: Understanding Segmentation in Cybersecurity
Network segmentation divides a network into multiple segments or subnets to improve security by containing breaches and controlling traffic flow, while microsegmentation applies this principle at a more granular level, isolating workloads or applications within the same network segment. Core concepts include reducing the attack surface, enforcing least privilege access, and minimizing lateral movement of threats by limiting communication pathways. Both strategies rely on segmentation policies, firewall rules, and identity-based access controls to enhance network security posture.
Key Differences Between Network Segmentation and Microsegmentation
Network segmentation divides a network into larger, distinct segments primarily based on physical or logical boundaries, improving performance and security by isolating traffic at the subnet or VLAN level. Microsegmentation provides granular, software-defined security policies at the workload or application level, enabling isolation down to individual virtual machines or containers regardless of location. The key difference lies in granularity: network segmentation controls traffic between broad network zones, while microsegmentation enforces dynamic security controls within those zones for sophisticated threat prevention.
Benefits of Traditional Network Segmentation
Traditional network segmentation enhances security by dividing a large network into smaller, manageable subnetworks, limiting the spread of cyber threats and reducing attack surfaces. It improves performance and reduces congestion by isolating traffic within designated segments, ensuring efficient data flow. Additionally, it simplifies compliance with regulatory standards by controlling access and monitoring network activity within specific segments.
Advantages of Microsegmentation for Modern Networks
Microsegmentation enhances network security by isolating workloads within data centers and cloud environments, limiting lateral movement of threats and minimizing attack surfaces. It enables granular policy enforcement at the individual workload level, offering precise control over traffic flows compared to traditional network segmentation. This fine-grained approach supports compliance requirements and improves visibility into network traffic, crucial for protecting modern, dynamic network architectures.
Common Use Cases: When to Use Each Approach
Network segmentation is commonly used to separate large networks into smaller, manageable zones, enhancing security by isolating critical assets like databases and servers in enterprise environments. Microsegmentation applies finer-grained controls within these zones, ideal for data centers and cloud environments where application-level protection and east-west traffic control are necessary. Use network segmentation for broad perimeter defense and microsegmentation for minimizing lateral movement and enforcing strict security policies inside trusted areas.
Security Implications and Risk Management
Network segmentation divides a network into distinct zones to limit the spread of threats and contain potential breaches, effectively reducing attack surfaces by isolating critical assets. Microsegmentation offers granular control at the workload or application level, enabling precise enforcement of security policies and minimizing lateral movement of threats inside the network. Both strategies enhance risk management, but microsegmentation provides superior protection against advanced persistent threats by enforcing strict, context-aware security controls within segmented environments.
Challenges in Implementation and Maintenance
Network segmentation faces challenges such as complex architecture design, limited granularity, and insufficient enforcement of security policies, leading to potential lateral movement by attackers. Microsegmentation requires high resource allocation for deploying granular security controls and continuous monitoring, making implementation labor-intensive and demanding skilled personnel. Both approaches struggle with maintaining accurate policy updates and visibility in dynamic environments, increasing the risk of misconfigurations and security gaps.
Choosing the Right Segmentation Strategy for Your Organization
Network segmentation divides a network into broad zones to improve security and performance by limiting traffic flow between segments, ideal for organizations with simpler infrastructure or regulatory requirements. Microsegmentation provides granular controls down to the workload or application level, enhancing security in complex environments with dynamic cloud and hybrid networks. Selecting between them depends on factors like organizational size, security posture, compliance demands, and operational complexity to ensure effective threat containment and resource allocation.
Future Trends in Network Security Segmentation
Network segmentation and microsegmentation are evolving with increased adoption of AI-driven automation and zero-trust architectures to enhance threat detection and containment. Future trends emphasize granular policy enforcement at the workload level, leveraging machine learning for dynamic access control and anomaly detection in real-time. Integration with cloud-native environments and hybrid infrastructures is accelerating, enabling scalable, adaptive segmentation strategies for comprehensive network security.
Network Segmentation Infographic
 libterm.com
libterm.com