Phishing attacks exploit social engineering to trick you into revealing sensitive information such as passwords, credit card numbers, or personal details. These deceptive schemes often appear as urgent messages from trusted sources, aiming to steal your identity or financial assets. Discover how to recognize phishing attempts and protect your data by reading the rest of the article.
Table of Comparison
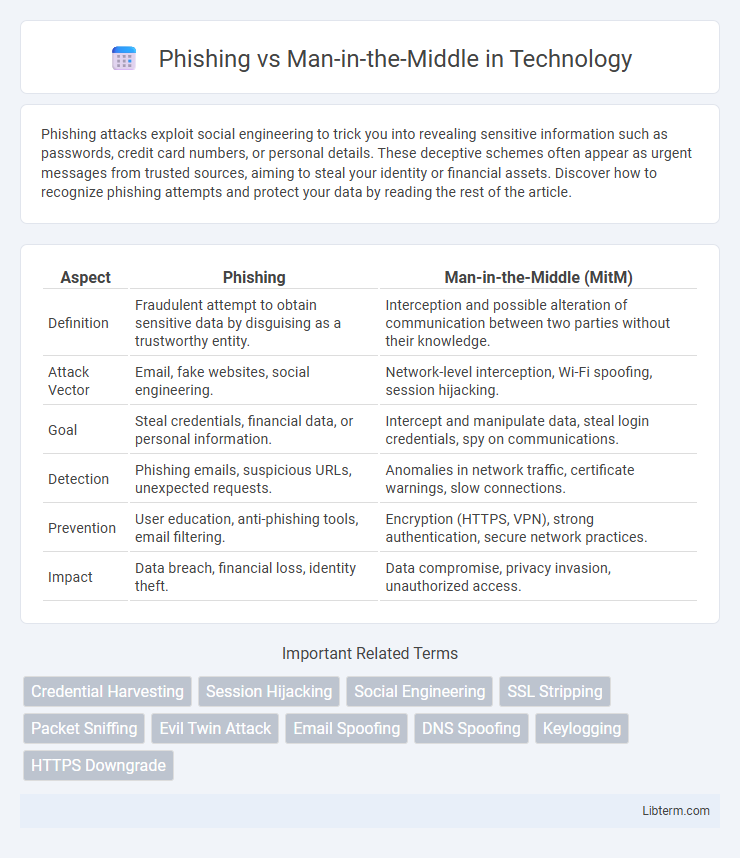
| Aspect | Phishing | Man-in-the-Middle (MitM) |
|---|---|---|
| Definition | Fraudulent attempt to obtain sensitive data by disguising as a trustworthy entity. | Interception and possible alteration of communication between two parties without their knowledge. |
| Attack Vector | Email, fake websites, social engineering. | Network-level interception, Wi-Fi spoofing, session hijacking. |
| Goal | Steal credentials, financial data, or personal information. | Intercept and manipulate data, steal login credentials, spy on communications. |
| Detection | Phishing emails, suspicious URLs, unexpected requests. | Anomalies in network traffic, certificate warnings, slow connections. |
| Prevention | User education, anti-phishing tools, email filtering. | Encryption (HTTPS, VPN), strong authentication, secure network practices. |
| Impact | Data breach, financial loss, identity theft. | Data compromise, privacy invasion, unauthorized access. |
Understanding Phishing: Definition and Techniques
Phishing is a cyberattack technique that involves tricking users into revealing sensitive information such as passwords, credit card numbers, or personal details by impersonating a trustworthy entity via emails, websites, or messages. Common phishing methods include spear phishing, where attackers target specific individuals or organizations, and clone phishing, which uses replicas of legitimate messages to deceive recipients. Understanding these tactics is critical for identifying fraudulent communications and preventing unauthorized access to confidential data.
What is a Man-in-the-Middle Attack?
A Man-in-the-Middle (MitM) attack occurs when an attacker secretly intercepts and alters communication between two parties without their knowledge. Unlike phishing, which tricks users into revealing sensitive information through deceptive messages or websites, MitM attacks exploit network vulnerabilities to eavesdrop or manipulate data in real time. Common MitM techniques include session hijacking, packet sniffing, and SSL stripping, posing significant risks to confidential communication and online security.
Common Methods Used in Phishing Attacks
Phishing attacks commonly use deceptive emails, fake websites, and instant messaging to trick victims into revealing sensitive information such as usernames, passwords, and credit card details. Attackers often employ social engineering tactics like urgent warnings or fake offers to prompt immediate action. These methods contrast with Man-in-the-Middle attacks, where the attacker intercepts and potentially alters communications between two parties without their knowledge.
How Man-in-the-Middle Attacks are Executed
Man-in-the-Middle (MitM) attacks are executed by intercepting communications between two parties without their knowledge, often through methods like packet sniffing, session hijacking, or DNS spoofing. Attackers exploit vulnerabilities in network protocols or unsecured Wi-Fi networks to capture sensitive data such as login credentials or financial information. By masquerading as one party, the attacker can manipulate or steal information in real-time, making detection difficult.
Key Differences Between Phishing and Man-in-the-Middle
Phishing attacks exploit social engineering techniques to deceive users into revealing sensitive information such as passwords and credit card numbers via fake emails or websites. Man-in-the-Middle (MitM) attacks intercept and alter communications between two parties without their knowledge, often targeting data during transmission in public Wi-Fi networks or compromised routers. The key difference lies in phishing manipulating user trust to obtain credentials, while MitM focuses on covertly eavesdropping or tampering with communication channels.
Warning Signs: Identifying Phishing Attempts
Phishing attempts often feature suspicious email addresses, generic greetings, urgent language, and unexpected requests for personal information or login credentials. Man-in-the-Middle attacks may not be immediately visible but can be suspected if users experience unusual website behavior, unexpected SSL certificate warnings, or inconsistencies in URL addresses during sensitive transactions. Recognizing these warning signs is essential for preventing unauthorized access and protecting sensitive data.
Detecting Man-in-the-Middle Attacks: Red Flags
Man-in-the-Middle (MitM) attacks can be detected by monitoring unexpected SSL/TLS certificate warnings, unusual network latency, and discrepancies in IP addresses during communication sessions. Red flags include inconsistent encryption keys, suspicious Wi-Fi hotspots, and unrecognized device connections intercepting the data flow. Regularly analyzing network traffic for irregular packet transfers and using intrusion detection systems enhances the identification of potential MitM threats.
Consequences of Phishing vs Man-in-the-Middle
Phishing attacks primarily result in credential theft, unauthorized access to sensitive accounts, and potential financial loss, often leading to identity fraud and compromised personal information. Man-in-the-Middle (MitM) attacks cause interception and manipulation of communication between two parties, resulting in data breaches, confidential information exposure, and unauthorized transaction modifications. Both attack types carry severe risks to privacy and security, but MitM attacks can undetectably alter or eavesdrop on communications in real-time, increasing the potential for ongoing data compromise.
Preventive Measures for Each Attack Type
Phishing prevention relies heavily on user education, email filtering, and implementing multi-factor authentication to reduce account compromise risks. Man-in-the-Middle attacks require strong encryption protocols such as TLS, secure Wi-Fi networks, and the use of VPNs to safeguard data transmission. Regular software updates and vigilant monitoring of network traffic also serve as essential defenses against both attack types.
Best Practices to Protect Yourself from Both Threats
Regularly updating software and enabling multi-factor authentication significantly reduce the risk of falling victim to phishing and man-in-the-middle attacks. Using encrypted connections such as HTTPS and VPNs safeguards data transmission against interception by attackers. Vigilant scrutiny of emails, avoiding suspicious links, and verifying website URLs are essential best practices to prevent credential theft from phishing scams and session hijacking from man-in-the-middle exploits.
Phishing Infographic
 libterm.com
libterm.com