Sidecar Proxy enhances microservices architecture by managing network traffic, security, and observability without altering application code. It runs alongside your service instance, enabling seamless communication and resilience in distributed systems. Explore the full article to understand how implementing a sidecar proxy can improve your system's performance and reliability.
Table of Comparison
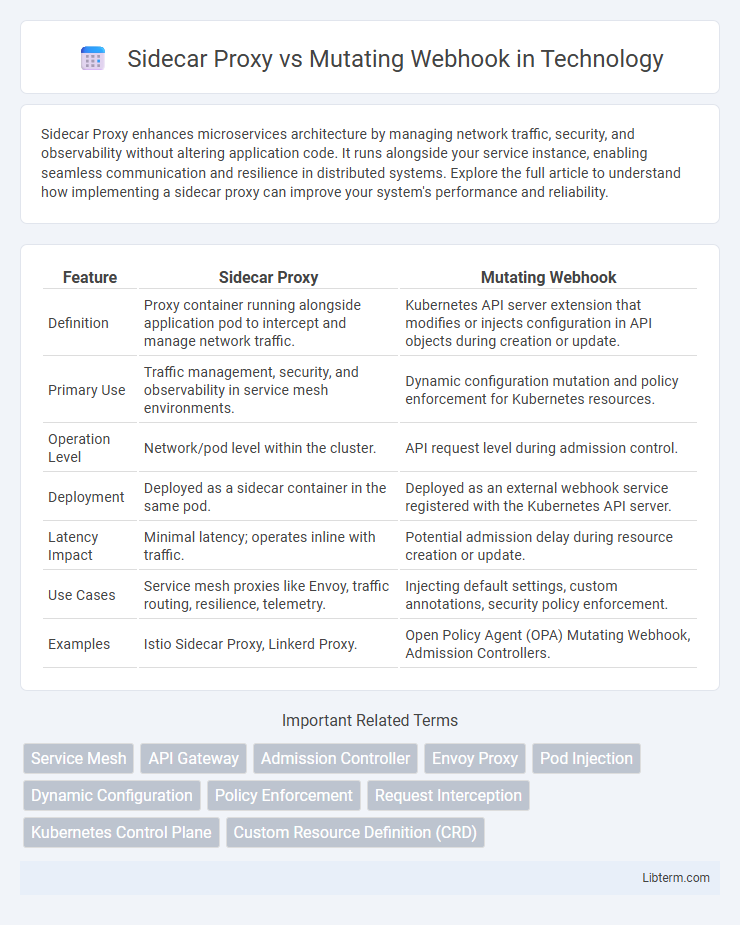
| Feature | Sidecar Proxy | Mutating Webhook |
|---|---|---|
| Definition | Proxy container running alongside application pod to intercept and manage network traffic. | Kubernetes API server extension that modifies or injects configuration in API objects during creation or update. |
| Primary Use | Traffic management, security, and observability in service mesh environments. | Dynamic configuration mutation and policy enforcement for Kubernetes resources. |
| Operation Level | Network/pod level within the cluster. | API request level during admission control. |
| Deployment | Deployed as a sidecar container in the same pod. | Deployed as an external webhook service registered with the Kubernetes API server. |
| Latency Impact | Minimal latency; operates inline with traffic. | Potential admission delay during resource creation or update. |
| Use Cases | Service mesh proxies like Envoy, traffic routing, resilience, telemetry. | Injecting default settings, custom annotations, security policy enforcement. |
| Examples | Istio Sidecar Proxy, Linkerd Proxy. | Open Policy Agent (OPA) Mutating Webhook, Admission Controllers. |
Introduction to Sidecar Proxy and Mutating Webhook
Sidecar Proxies are network proxies deployed alongside application containers to manage communication, security, and traffic routing without altering application code. Mutating Webhooks are Kubernetes admission controllers that intercept API requests to modify or validate resource configurations during object creation or updates. Both tools enhance application behavior and cluster security but operate at different layers: Sidecar Proxies at runtime network traffic and Mutating Webhooks at the Kubernetes API control plane.
Core Functionality Overview
Sidecar Proxy operates by intercepting and managing network traffic between microservices to enable features like load balancing, security, and observability without changing the application code. Mutating Webhook functions within Kubernetes as an admission controller that dynamically modifies or injects configurations into resources during their creation or update, enabling automated policy enforcement and customization. Core functionality of Sidecar Proxy centers on traffic management and service mesh integration, whereas Mutating Webhook's core lies in Kubernetes resource mutation and admission control to enforce cluster policies.
Architectural Differences
Sidecar proxies operate as separate, dedicated network containers deployed alongside application containers within the same pod, intercepting and managing network traffic transparently to enable service mesh capabilities such as load balancing and security enforcement. Mutating webhooks function as Kubernetes admission controllers that intercept API server requests to dynamically modify object configurations before persistence, focusing on declarative resource transformations rather than real-time traffic handling. The architectural distinction lies in sidecar proxies embedding network-level control within each pod at runtime, whereas mutating webhooks provide cluster-level object mutation during resource creation or update events.
Use Cases and Deployment Scenarios
Sidecar proxies are primarily used to enhance application networking by injecting proxy containers alongside application pods, enabling functionalities like traffic routing, load balancing, and observability in service mesh architectures such as Istio. Mutating webhooks serve as admission controllers that modify or validate Kubernetes API requests during resource creation or update, typically deployed for dynamic configuration changes, policy enforcement, or injecting sidecars automatically in CI/CD pipelines. Use cases for sidecar proxies include service discovery, security enforcement, and telemetry data collection, while mutating webhooks are suited for automating pod modification, custom resource management, and enforcing organizational policies at cluster admission time.
Performance Implications
Sidecar proxies introduce network latency due to traffic interception and additional processing, impacting application response times and resource consumption. Mutating webhooks operate during Kubernetes admission, affecting pod startup time but not runtime request latency. Evaluating performance requires balancing sidecar proxy overhead against webhook-induced deployment delays, especially in high-throughput environments.
Security Considerations
Sidecar proxies enhance security by isolating network traffic within service mesh environments, enforcing mutual TLS encryption and fine-grained access controls at the application layer. Mutating webhooks, while powerful for dynamic admission control, introduce risks related to runtime configuration changes that can affect cluster security posture if misconfigured or compromised. Ensuring webhook authenticity through TLS verification and strict RBAC policies is critical to prevent unauthorized or malicious mutations impacting workload integrity.
Scalability and Resource Consumption
Sidecar proxies enhance scalability by isolating network functions within each service instance, allowing independent scaling and reducing coupling in microservices architectures. Mutating webhooks can introduce latency and resource overhead on the Kubernetes API server, potentially becoming bottlenecks under high request volumes. While sidecar proxies consume memory and CPU per pod, their distributed model offers more predictable resource consumption compared to the centralized processing of mutating webhooks.
Ease of Implementation and Maintenance
Sidecar proxies require managing additional container instances alongside application pods, increasing implementation complexity and ongoing maintenance efforts. Mutating webhooks offer centralized control by intercepting API server requests, simplifying deployment and reducing the operational overhead for updating injection logic. Maintenance of mutating webhooks often involves fewer changes to application configurations compared to sidecar proxies, enabling easier scaling and version upgrades.
Integration with Kubernetes Ecosystem
Sidecar Proxy integrates deeply with the Kubernetes ecosystem by injecting proxy containers alongside application pods, enabling transparent network traffic control and observability without modifying application code. Mutating Webhook leverages Kubernetes admission controllers to dynamically alter pod specifications during creation, providing flexible policy enforcement and customization of resources before they are admitted to the cluster. Both tools enhance Kubernetes workloads but differ in operational layers: Sidecar Proxy manages runtime network interactions, while Mutating Webhook modifies configuration at deployment time.
Choosing Between Sidecar Proxy and Mutating Webhook
Choosing between a sidecar proxy and a mutating webhook depends largely on the use case and operational complexity. Sidecar proxies offer real-time network-level control and observability in service meshes like Istio, ideal for traffic management without modifying application code. Mutating webhooks provide dynamic admission control in Kubernetes, enabling automated resource mutation during object creation or updates, which is useful for enforcing policy or injecting configuration at the API level.
Sidecar Proxy Infographic
 libterm.com
libterm.com