OAuth2 Authorization Code Flow is a secure method for obtaining access tokens by exchanging an authorization code received after user authentication. This flow enhances security by keeping credentials off the client and requiring server-to-server communication to obtain tokens. Discover how this process safeguards your applications and ensures secure user access by reading the full article.
Table of Comparison
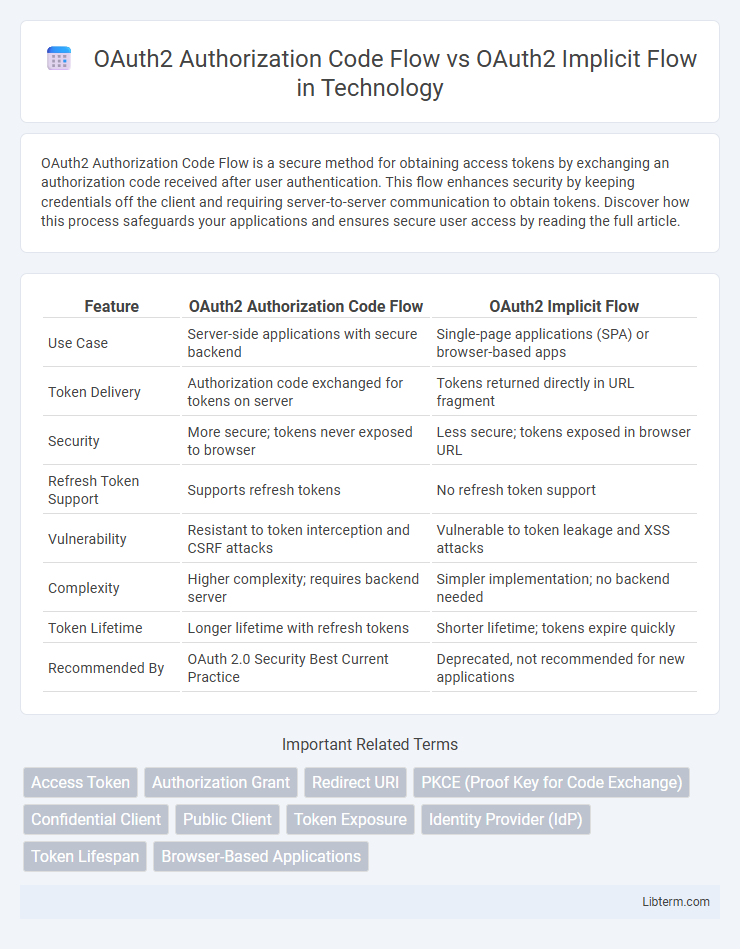
| Feature | OAuth2 Authorization Code Flow | OAuth2 Implicit Flow |
|---|---|---|
| Use Case | Server-side applications with secure backend | Single-page applications (SPA) or browser-based apps |
| Token Delivery | Authorization code exchanged for tokens on server | Tokens returned directly in URL fragment |
| Security | More secure; tokens never exposed to browser | Less secure; tokens exposed in browser URL |
| Refresh Token Support | Supports refresh tokens | No refresh token support |
| Vulnerability | Resistant to token interception and CSRF attacks | Vulnerable to token leakage and XSS attacks |
| Complexity | Higher complexity; requires backend server | Simpler implementation; no backend needed |
| Token Lifetime | Longer lifetime with refresh tokens | Shorter lifetime; tokens expire quickly |
| Recommended By | OAuth 2.0 Security Best Current Practice | Deprecated, not recommended for new applications |
Introduction to OAuth2 Flows
OAuth2 Authorization Code Flow involves exchanging an authorization code for an access token, providing enhanced security by keeping tokens off the browser and enabling secure server-side token handling. OAuth2 Implicit Flow directly returns access tokens in the redirect URL, designed primarily for client-side applications but with increased vulnerability due to token exposure in the URL. These flows address different use cases, where Authorization Code Flow suits server-based apps and Implicit Flow caters to browser-based or mobile applications requiring faster, token-only exchanges.
What is the Authorization Code Flow?
The Authorization Code Flow in OAuth2 is a secure authentication process where the client application receives an authorization code from the authorization server before exchanging it for an access token. This flow separates the client credentials from the access token, minimizing the risk of token exposure to unauthorized parties. It is primarily used by confidential clients, such as web applications, where the client secret can be securely stored.
What is the Implicit Flow?
The OAuth2 Implicit Flow is a simplified authorization process mainly designed for browser-based or single-page applications where the client cannot securely store a secret. It involves directly obtaining an access token from the authorization server without exchanging an authorization code, reducing the number of steps but increasing exposure to token interception risks. Unlike the Authorization Code Flow, the Implicit Flow bypasses the backend server, making it less secure but more suited for public clients with limited backend capabilities.
Key Differences Between Authorization Code and Implicit Flows
OAuth2 Authorization Code Flow involves exchanging an authorization code for an access token via a secure backend, enhancing security by keeping tokens off the user-agent and minimizing exposure to interception. In contrast, OAuth2 Implicit Flow directly returns the access token in the URL fragment, suitable for single-page applications but less secure due to token exposure in the browser and lack of backend verification. Key differences include token exchange method, security posture, and use case suitability, with Authorization Code Flow favored for confidential clients and Implicit Flow for public clients without secure backends.
Security Implications of Each Flow
The OAuth2 Authorization Code Flow enhances security by exchanging an authorization code for tokens on the server side, minimizing token exposure to the user-agent and reducing the risk of token interception or leakage. In contrast, the OAuth2 Implicit Flow delivers tokens directly in the browser via URL fragments, increasing vulnerability to token theft through browser history, phishing, or malicious scripts. Due to these risks, the Authorization Code Flow with PKCE (Proof Key for Code Exchange) is now recommended for most applications, including Single Page Applications (SPAs), as it significantly mitigates the security weaknesses inherent in the Implicit Flow.
Use Cases for Authorization Code Flow
OAuth2 Authorization Code Flow is ideal for server-side applications requiring secure access to protected resources by exchanging an authorization code for an access token, ensuring tokens are never exposed to the user agent. It is commonly used for web applications with backend servers that can securely store client secrets and refresh tokens, supporting long-lived sessions and enhanced security. This flow is particularly suited for scenarios involving sensitive user data and APIs, such as financial services or enterprise services requiring robust authentication and token management.
Use Cases for Implicit Flow
OAuth2 Implicit Flow is primarily designed for public clients such as single-page applications (SPAs) where storing client secrets securely is not feasible. It enables user agents like browsers to receive access tokens directly from the authorization endpoint without exchanging an authorization code, optimizing for environments with limited backend capabilities. Common use cases include mobile apps and JavaScript-based web apps requiring quick token acquisition without server-side token handling.
Deprecated Status and Modern Recommendations
OAuth2 Authorization Code Flow is the recommended standard for secure authentication, as it supports server-side token exchange and minimizes exposure of tokens to the user-agent, unlike the OAuth2 Implicit Flow which directly returns tokens in the URL fragment. The OAuth2 Implicit Flow is now deprecated by the Internet Engineering Task Force (IETF) due to various security vulnerabilities, including token interception and lack of refresh token support. Modern best practices advocate for Authorization Code Flow with Proof Key for Code Exchange (PKCE) to enhance security, especially in single-page applications and mobile apps.
Choosing the Right OAuth2 Flow for Your Application
Choosing the right OAuth2 flow depends on your application's security requirements and client type, with Authorization Code Flow recommended for server-side applications due to its ability to securely exchange an authorization code for tokens via a backend. Implicit Flow, now largely deprecated, was designed for single-page applications (SPAs) but exposes tokens directly in the browser, increasing vulnerability risks. Prioritizing the Authorization Code Flow with Proof Key for Code Exchange (PKCE) offers enhanced security for both native and web apps by preventing token interception and replay attacks.
Conclusion: Best Practices for OAuth2 Flows
OAuth2 Authorization Code Flow ensures higher security by exchanging an authorization code for tokens on a backend server, preventing exposure of tokens to the browser and mitigating risks like token leakage. OAuth2 Implicit Flow, designed for public clients like single-page applications, directly returns tokens in the URL, increasing vulnerability to interception and should be avoided in favor of the Authorization Code Flow with PKCE whenever possible. Best practices recommend adopting the Authorization Code Flow with PKCE for all client types to enhance security, simplify token management, and comply with modern security standards.
OAuth2 Authorization Code Flow Infographic
 libterm.com
libterm.com