CAS (Certified Automation Specialist) certification validates your expertise in automation systems, control processes, and industrial automation technologies. Earning CAS demonstrates proficiency in designing, implementing, and managing automation solutions that enhance operational efficiency and productivity. Explore the full article to discover how obtaining CAS can elevate your career in automation.
Table of Comparison
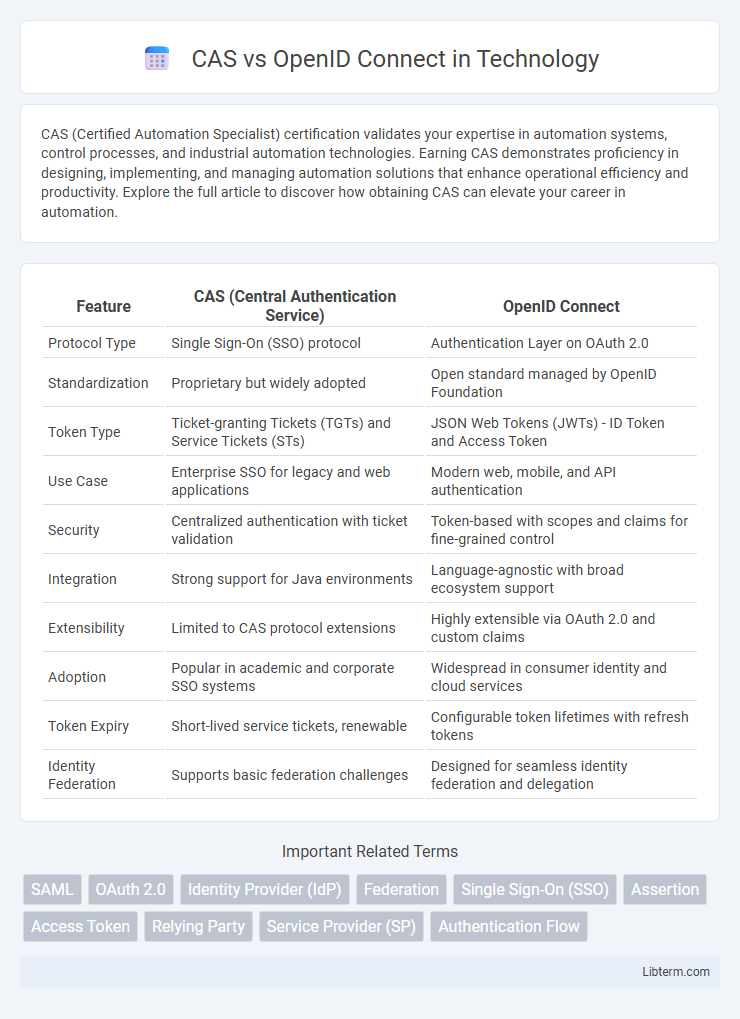
| Feature | CAS (Central Authentication Service) | OpenID Connect |
|---|---|---|
| Protocol Type | Single Sign-On (SSO) protocol | Authentication Layer on OAuth 2.0 |
| Standardization | Proprietary but widely adopted | Open standard managed by OpenID Foundation |
| Token Type | Ticket-granting Tickets (TGTs) and Service Tickets (STs) | JSON Web Tokens (JWTs) - ID Token and Access Token |
| Use Case | Enterprise SSO for legacy and web applications | Modern web, mobile, and API authentication |
| Security | Centralized authentication with ticket validation | Token-based with scopes and claims for fine-grained control |
| Integration | Strong support for Java environments | Language-agnostic with broad ecosystem support |
| Extensibility | Limited to CAS protocol extensions | Highly extensible via OAuth 2.0 and custom claims |
| Adoption | Popular in academic and corporate SSO systems | Widespread in consumer identity and cloud services |
| Token Expiry | Short-lived service tickets, renewable | Configurable token lifetimes with refresh tokens |
| Identity Federation | Supports basic federation challenges | Designed for seamless identity federation and delegation |
Introduction to CAS and OpenID Connect
CAS (Central Authentication Service) is a single sign-on protocol designed to provide secure user authentication across multiple applications through a centralized server. OpenID Connect is an identity layer built on OAuth 2.0 that enables clients to verify the identity of users based on authentication performed by an authorization server, supporting modern web and mobile applications. Both CAS and OpenID Connect facilitate seamless user authentication but differ in protocols and integration methods, with CAS focusing on ticket-based authentication and OpenID Connect leveraging JSON Web Tokens (JWT) for standardized identity claims.
Key Concepts and Protocol Structures
CAS (Central Authentication Service) operates using a ticket-based protocol where a client obtains a ticket from the CAS server to access multiple applications, emphasizing a single sign-on (SSO) experience. OpenID Connect builds on OAuth 2.0 and utilizes JSON Web Tokens (JWTs) to provide identity verification, enabling secure API authorization with ID tokens, access tokens, and refresh tokens. CAS focuses on ticket validation through service tickets and proxy tickets, while OpenID Connect leverages standardized endpoints such as authorization, token, and userinfo endpoints to facilitate authentication and user information retrieval.
How CAS Works: Overview and Workflow
CAS (Central Authentication Service) operates through a ticket-based authentication mechanism where users first authenticate with the CAS server, which then issues a service ticket for accessing specific applications. When a user requests access to a CAS-enabled service, the service redirects the user to the CAS server for authentication; upon successful login, the CAS server provides a service ticket that the application verifies by contacting the CAS server's validation endpoint. This workflow ensures single sign-on (SSO) capabilities by centralizing authentication and allowing multiple services to trust the CAS server for user identity verification.
How OpenID Connect Works: Overview and Workflow
OpenID Connect operates as an identity layer on top of the OAuth 2.0 protocol, enabling secure user authentication and authorization via JSON Web Tokens (JWTs). The workflow involves the client application redirecting the user to the OpenID Provider (OP) for authentication, where the OP verifies the user's credentials and returns an ID token and access token. These tokens allow the client to securely identify the user and access authorized resources without handling sensitive user credentials directly.
Authentication Mechanisms Compared
CAS (Central Authentication Service) employs a ticket-based system where users authenticate once and receive a service ticket for accessing multiple applications within a single domain, prioritizing seamless single sign-on (SSO) experience. OpenID Connect (OIDC) builds on OAuth 2.0, using JWT (JSON Web Tokens) to securely transmit identity information, enabling robust federated authentication across diverse platforms and applications. Unlike CAS, OpenID Connect supports stronger token-based authentication with standardized scopes and claims, enhancing token validation and user identity verification processes.
Security Features: CAS vs OpenID Connect
CAS (Central Authentication Service) emphasizes secure single sign-on with strong encryption protocols and supports multifactor authentication to enhance security. OpenID Connect, built on OAuth 2.0, offers robust token-based authentication with ID tokens and scopes for fine-grained access control, enabling dynamic client registration and strong replay attack protection. Both protocols provide secure user authentication but differ in token management, with OpenID Connect leveraging JSON Web Tokens (JWT) for stateless security and CAS primarily relying on server-side ticket validation.
Integration and Compatibility Considerations
CAS (Central Authentication Service) and OpenID Connect differ significantly in integration and compatibility considerations. CAS offers straightforward integration with legacy systems and supports various protocols like SAML and OAuth, making it suitable for enterprise environments with diverse authentication needs. OpenID Connect, built on OAuth 2.0, provides seamless compatibility with modern web and mobile applications, enabling standardized identity federation and supporting JSON-based token formats for enhanced interoperability across platforms.
Use Cases and Industry Adoption
CAS (Central Authentication Service) excels in enterprise environments requiring single sign-on (SSO) for internal applications, especially in higher education and government sectors, due to its simplicity and centralized authentication model. OpenID Connect, built on OAuth 2.0, is widely adopted in consumer-facing web and mobile applications, enabling secure delegated authentication across diverse platforms including social media and cloud services. Industry adoption favors OpenID Connect for its flexibility and support in modern distributed systems, while CAS remains strong in legacy systems and institutional use cases demanding standardized, reliable SSO solutions.
Pros and Cons of CAS and OpenID Connect
CAS (Central Authentication Service) offers robust single sign-on capabilities tailored for enterprise environments with strong support for legacy systems and straightforward implementation. OpenID Connect, built on OAuth 2.0, provides enhanced security features like token-based authentication and seamless integration with modern web and mobile applications. CAS may lack flexibility and modern protocol support compared to OpenID Connect, which supports scalability and comprehensive identity federation but can introduce complexity in setup and token management.
Choosing the Right Protocol for Your Needs
Choosing between CAS and OpenID Connect depends on your organization's identity management requirements and existing infrastructure. CAS offers a simple, centralized authentication system suited for academic and enterprise environments, while OpenID Connect provides a more flexible, modern protocol built on OAuth 2.0, supporting diverse applications and enhanced security features like token introspection and dynamic client registration. Evaluate factors such as scalability, interoperability, and the need for delegated authorization to select the protocol that aligns with your security policies and user experience goals.
CAS Infographic
 libterm.com
libterm.com