Hardware Security Modules (HSMs) provide robust cryptographic key management, ensuring your sensitive data remains secure from unauthorized access and cyber threats. These dedicated devices perform encryption, decryption, and authentication processes with high efficiency and tamper-resistant safeguards. Discover how integrating an HSM can enhance your organization's security by reading the rest of the article.
Table of Comparison
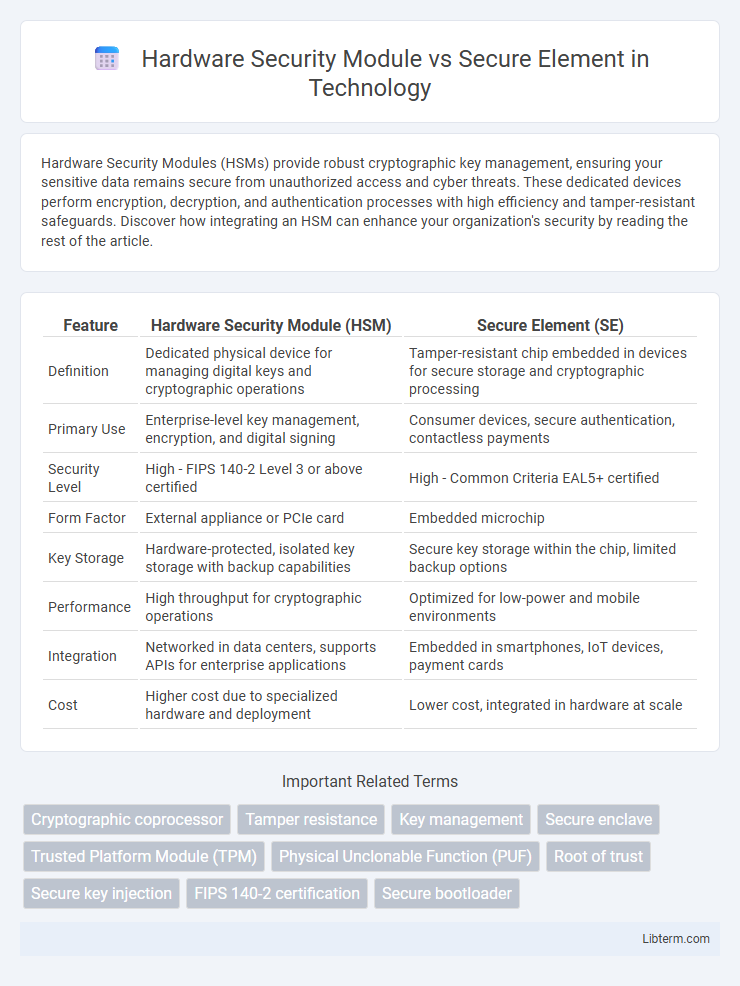
| Feature | Hardware Security Module (HSM) | Secure Element (SE) |
|---|---|---|
| Definition | Dedicated physical device for managing digital keys and cryptographic operations | Tamper-resistant chip embedded in devices for secure storage and cryptographic processing |
| Primary Use | Enterprise-level key management, encryption, and digital signing | Consumer devices, secure authentication, contactless payments |
| Security Level | High - FIPS 140-2 Level 3 or above certified | High - Common Criteria EAL5+ certified |
| Form Factor | External appliance or PCIe card | Embedded microchip |
| Key Storage | Hardware-protected, isolated key storage with backup capabilities | Secure key storage within the chip, limited backup options |
| Performance | High throughput for cryptographic operations | Optimized for low-power and mobile environments |
| Integration | Networked in data centers, supports APIs for enterprise applications | Embedded in smartphones, IoT devices, payment cards |
| Cost | Higher cost due to specialized hardware and deployment | Lower cost, integrated in hardware at scale |
Introduction to Hardware Security Module (HSM) and Secure Element (SE)
Hardware Security Module (HSM) is a physical device designed to manage digital keys securely and perform cryptographic operations, ensuring robust protection in enterprise environments. Secure Element (SE) is a tamper-resistant chip integrated into devices like smartphones and payment cards, providing hardware-based security for sensitive data and authentication processes. Both HSMs and SEs play critical roles in safeguarding cryptographic keys, but HSMs focus on high-volume, centralized key management, whereas SEs emphasize secure storage and execution in embedded systems.
Core Functions: What Do HSMs and Secure Elements Do?
Hardware Security Modules (HSMs) provide robust cryptographic key management, digital signing, and encryption services primarily for enterprise-level applications, ensuring secure key generation, storage, and lifecycle management within a tamper-resistant environment. Secure Elements (SEs) are dedicated microcontrollers designed for secure storage and execution of cryptographic operations, often embedded in mobile devices, payment cards, and IoT hardware, handling sensitive data like authentication credentials and payment information. Both focus on cryptographic security, but HSMs emphasize high-throughput, centralized key management, whereas SEs prioritize localized, device-specific protection and secure execution.
Key Differences between HSMs and Secure Elements
Hardware Security Modules (HSMs) are designed for high-performance cryptographic processing and secure key management in data centers, supporting large-scale enterprise applications with robust physical and logical security controls. Secure Elements (SEs) are compact, tamper-resistant chips embedded in devices like smartphones and IoT hardware, optimized for securing individual cryptographic keys and sensitive operations in constrained environments. The key differences lie in scale, with HSMs offering centralized, high-throughput security for multiple users, while Secure Elements provide decentralized, device-specific protection with lower resource requirements.
Security Features: HSM vs Secure Element
Hardware Security Modules (HSMs) and Secure Elements (SEs) both provide robust security features, with HSMs delivering high-performance cryptographic operations, secure key management, and tamper-resistant environments designed for enterprise-level applications. Secure Elements offer compact, embedded security with dedicated processing for secure storage, encryption, and authentication, ideal for mobile devices and IoT applications requiring strong protection against physical and logical attacks. Both technologies use tamper-evident and tamper-resistant designs, but HSMs emphasize scalability and regulatory compliance, whereas Secure Elements prioritize integration and low power consumption.
Performance and Scalability Comparison
Hardware Security Modules (HSMs) deliver high-performance cryptographic operations supporting thousands of transactions per second, making them ideal for enterprise-level scalability and complex multi-tenant environments. Secure Elements (SEs), while offering robust tamper-resistant security for embedded applications, typically handle fewer cryptographic operations and are optimized for low-power, constrained environments, limiting their scalability in large-scale deployments. Consequently, HSMs outperform SEs in throughput and scalability metrics crucial for cloud services and financial institutions requiring extensive cryptographic processing capacity.
Typical Use Cases for HSMs and Secure Elements
Hardware Security Modules (HSMs) are predominantly used in enterprise environments for cryptographic key management, digital signing, and payment processing due to their high-performance and tamper-resistant architecture. Secure Elements (SEs) are embedded in devices like smartphones and IoT gadgets to securely store credentials, execute authentication, and protect sensitive data at the hardware level. Enterprises deploy HSMs in data centers for PKI infrastructure and blockchain validation, while Secure Elements serve mobile payments, SIM cards, and secure identity verification in consumer electronics.
Integration and Deployment Considerations
Hardware Security Modules (HSMs) are typically integrated as centralized cryptographic servers within enterprise data centers, requiring significant infrastructure for deployment and maintenance, whereas Secure Elements (SEs) are embedded directly into devices like smartphones or IoT gadgets, enabling more seamless, on-device security without relying on external hardware. The deployment of HSMs demands robust network connectivity and dedicated management tools to handle scalable cryptographic operations, while SEs offer streamlined integration through standardized interfaces such as GlobalPlatform or ISO/IEC 7816, facilitating secure key storage and cryptographic processing at the hardware level. Organizations must assess factors like operational complexity, scalability, and device-level security needs when deciding between HSMs for centralized, high-throughput environments and SEs for distributed, low-latency applications.
Cost Implications and Total Cost of Ownership
Hardware Security Modules (HSMs) typically involve higher upfront costs due to their advanced cryptographic capabilities and enterprise-grade hardware, making them suitable for large-scale deployments requiring robust security. Secure Elements (SEs), as embedded chips designed for specific applications, generally offer lower acquisition and integration costs but may incur additional expenses over time for updates and limited scalability. Total Cost of Ownership (TCO) for HSMs includes maintenance, support, and potential cloud integration fees, while SEs emphasize lower initial investment with possible higher cumulative costs linked to lifecycle management and firmware upgrades.
Regulatory Compliance and Industry Standards
Hardware Security Modules (HSMs) and Secure Elements (SEs) both play critical roles in regulatory compliance by providing robust cryptographic key management and secure storage solutions aligned with standards such as FIPS 140-2/3 and Common Criteria. HSMs are typically certified under stringent industry regulations for data centers and cloud providers, enabling compliance with frameworks like PCI-DSS, GDPR, and HIPAA through strong hardware-based encryption and tamper resistance. Secure Elements, embedded in devices like smartphones and payment cards, conform to industry standards including EMVCo and GlobalPlatform, ensuring secure execution environments that meet regulatory requirements for identity verification and secure transactions.
Choosing the Right Solution: HSM or Secure Element?
Choosing between a Hardware Security Module (HSM) and a Secure Element depends on the specific security needs and use cases, as HSMs provide robust cryptographic key management and high-performance encryption ideal for enterprise environments, while Secure Elements offer tamper-resistant hardware designed for secure storage and execution in constrained devices like smartphones and IoT. Evaluating factors such as scalability, integration complexity, and compliance requirements ensures alignment with organizational security policies and risk tolerance. Selecting the right solution optimizes data protection, regulatory adherence, and operational efficiency across digital infrastructure.
Hardware Security Module Infographic
 libterm.com
libterm.com