SQL Injection exploits vulnerabilities in your database interactions by inserting malicious code into input fields, allowing attackers to manipulate queries and access sensitive data. Preventing SQL Injection involves using prepared statements, parameterized queries, and rigorous input validation to secure your application's backend. Discover effective techniques and best practices in the rest of this article to protect your systems from this common threat.
Table of Comparison
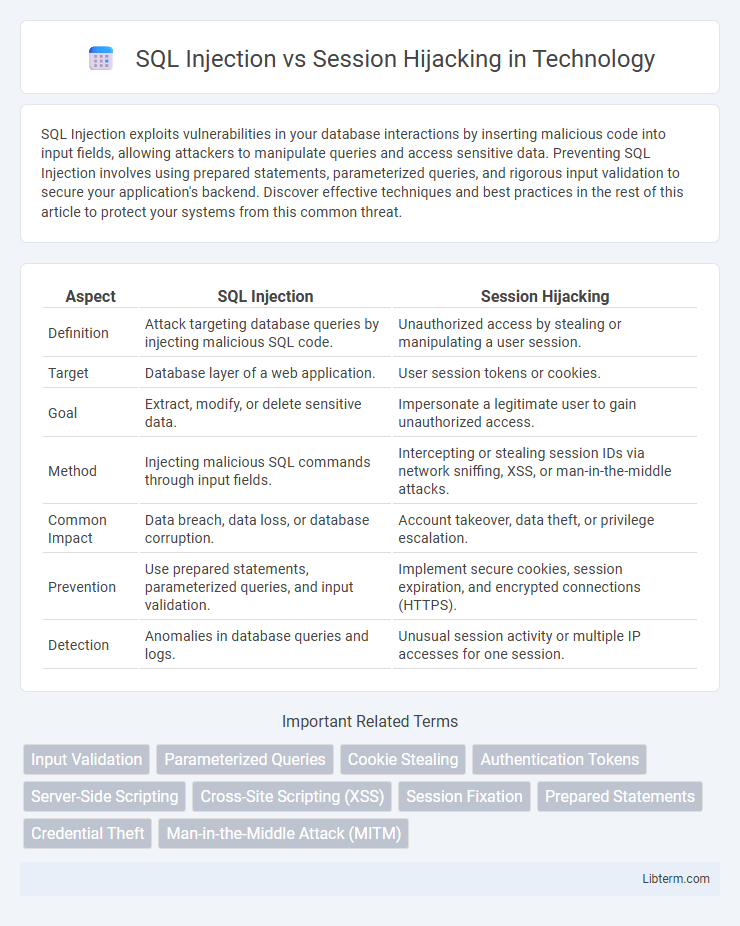
| Aspect | SQL Injection | Session Hijacking |
|---|---|---|
| Definition | Attack targeting database queries by injecting malicious SQL code. | Unauthorized access by stealing or manipulating a user session. |
| Target | Database layer of a web application. | User session tokens or cookies. |
| Goal | Extract, modify, or delete sensitive data. | Impersonate a legitimate user to gain unauthorized access. |
| Method | Injecting malicious SQL commands through input fields. | Intercepting or stealing session IDs via network sniffing, XSS, or man-in-the-middle attacks. |
| Common Impact | Data breach, data loss, or database corruption. | Account takeover, data theft, or privilege escalation. |
| Prevention | Use prepared statements, parameterized queries, and input validation. | Implement secure cookies, session expiration, and encrypted connections (HTTPS). |
| Detection | Anomalies in database queries and logs. | Unusual session activity or multiple IP accesses for one session. |
Introduction to SQL Injection and Session Hijacking
SQL Injection exploits vulnerabilities in database query execution by inserting malicious SQL code, enabling unauthorized data access or manipulation. Session Hijacking targets active user sessions by stealing session tokens, allowing attackers to impersonate legitimate users and gain unauthorized access. Both techniques compromise security but focus on different attack vectors: database manipulation versus session exploitation.
Definition of SQL Injection
SQL Injection is a web security vulnerability that allows attackers to interfere with the queries an application makes to its database by injecting malicious SQL code, often resulting in unauthorized data access or manipulation. Session Hijacking, on the other hand, involves stealing a valid session token to impersonate a legitimate user and gain unauthorized access to an active session. SQL Injection targets the backend database, exploiting input validation weaknesses, while Session Hijacking focuses on compromising user sessions and authentication mechanisms.
Definition of Session Hijacking
Session hijacking is a cyberattack where an attacker takes control of a user's active session by stealing or predicting the session identifier, allowing unauthorized access to sensitive information or functionalities. This differs from SQL Injection, which manipulates database queries to extract or alter data. Session hijacking targets the user's authentication state, making it a critical threat to session security.
Common Attack Techniques
SQL Injection exploits vulnerabilities in database query handling by injecting malicious SQL code to manipulate or access sensitive data. Session Hijacking involves intercepting or stealing active session tokens, often through methods like cross-site scripting (XSS) or network packet sniffing, to impersonate legitimate users. Both attacks leverage weaknesses in web application security but target different components: backend databases versus user session management.
Risk Factors and Vulnerable Scenarios
SQL injection exploits vulnerabilities in web applications that improperly sanitize user inputs, allowing attackers to manipulate database queries and access sensitive data, posing significant risks to data integrity and confidentiality. Session hijacking targets flaws in session management, such as weak session IDs or unsecured cookies, enabling attackers to impersonate legitimate users and gain unauthorized access to protected resources. High-risk scenarios include poorly coded login forms for SQL injection and unsecured Wi-Fi networks or unencrypted sessions for session hijacking.
Real-World Examples
SQL Injection exploits vulnerabilities in database queries, exemplified by the 2017 Equifax breach, where attackers accessed sensitive data of 147 million users through flawed input validation. Session Hijacking involves stealing or manipulating session tokens to impersonate users, demonstrated in the 2011 Sony PlayStation Network attack that compromised over 77 million accounts by intercepting session information. Both attack types highlight critical security gaps in input sanitization and session management practices within web applications.
Detection and Prevention Strategies
SQL Injection detection relies on monitoring unusual database queries and input anomalies using web application firewalls and automated scanning tools. Preventive strategies include parameterized queries, input validation, and least privilege database access. Session Hijacking detection involves tracking suspicious session activities and IP address inconsistencies, while prevention focuses on secure cookies, implementing HTTPS, and regenerating session IDs after login.
Impact on Data Security
SQL Injection compromises data integrity by allowing attackers to manipulate and extract sensitive information directly from databases, leading to unauthorized access and potential data corruption. Session Hijacking threatens data confidentiality by intercepting valid user sessions, enabling attackers to impersonate legitimate users and gain unauthorized access to protected resources. Both attacks undermine data security, but SQL Injection primarily risks data exposure and alteration, while Session Hijacking targets user authentication and session management vulnerabilities.
Best Practices for Mitigation
Implementing prepared statements and parameterized queries remains the most effective method to prevent SQL Injection by ensuring user inputs are properly sanitized. For mitigating Session Hijacking, enforce secure cookie attributes such as HttpOnly and Secure, alongside using session timeouts and regenerating session IDs after login. Employ multi-layered security measures including web application firewalls, regular vulnerability assessments, and strong authentication protocols to comprehensively reduce risks of these attacks.
Conclusion: Comparing SQL Injection and Session Hijacking
SQL Injection exploits vulnerabilities in database queries to gain unauthorized access to or manipulate data, while Session Hijacking targets active user sessions to impersonate legitimate users and steal sensitive information. Both attacks compromise security but differ in methodology and impact, with SQL Injection focusing on backend database exploitation and Session Hijacking on user authentication processes. Effective defense requires robust input validation for SQL Injection and secure session management practices to prevent Session Hijacking.
SQL Injection Infographic
 libterm.com
libterm.com