Control flow analysis examines the order in which individual instructions, statements, or operations are executed within a program, highlighting loops, branches, and conditional paths essential for optimizing performance and debugging. It plays a crucial role in identifying unreachable code, detecting infinite loops, and ensuring the program behaves as expected during runtime. Explore the following sections to deepen your understanding and enhance your coding practices with effective control flow analysis techniques.
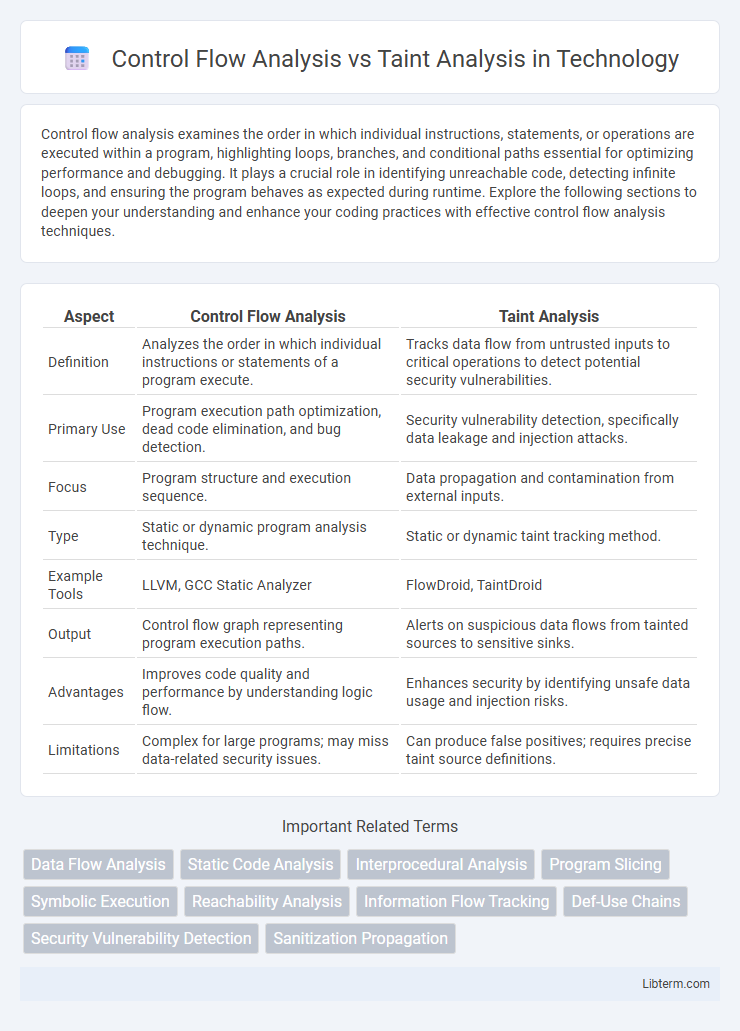
Table of Comparison
| Aspect | Control Flow Analysis | Taint Analysis |
|---|---|---|
| Definition | Analyzes the order in which individual instructions or statements of a program execute. | Tracks data flow from untrusted inputs to critical operations to detect potential security vulnerabilities. |
| Primary Use | Program execution path optimization, dead code elimination, and bug detection. | Security vulnerability detection, specifically data leakage and injection attacks. |
| Focus | Program structure and execution sequence. | Data propagation and contamination from external inputs. |
| Type | Static or dynamic program analysis technique. | Static or dynamic taint tracking method. |
| Example Tools | LLVM, GCC Static Analyzer | FlowDroid, TaintDroid |
| Output | Control flow graph representing program execution paths. | Alerts on suspicious data flows from tainted sources to sensitive sinks. |
| Advantages | Improves code quality and performance by understanding logic flow. | Enhances security by identifying unsafe data usage and injection risks. |
| Limitations | Complex for large programs; may miss data-related security issues. | Can produce false positives; requires precise taint source definitions. |
Introduction to Control Flow Analysis and Taint Analysis
Control Flow Analysis examines the order in which individual instructions, statements, or function calls are executed within a program, enabling the detection of unreachable code and potential execution paths. Taint Analysis tracks the flow of untrusted or user-controlled data (tainted data) through the software, identifying security vulnerabilities such as injection attacks and data leaks. Both techniques enhance program security by analyzing data and execution flows but focus on different aspects: Control Flow Analysis on execution paths, and Taint Analysis on data propagation.
Core Concepts: Understanding Control Flow Analysis
Control Flow Analysis examines the order in which individual instructions, statements, or function calls are executed within a program to identify potential execution paths and detect irregularities such as loops or unreachable code. It constructs a control flow graph (CFG) representing all possible routes the program might take during execution, enabling static analysis of behavior without running the code. This technique is essential for optimizing compilers, detecting dead code, and enhancing software security by identifying unexpected execution flows.
Core Concepts: Understanding Taint Analysis
Taint Analysis tracks the flow of untrusted data through a program to identify potential security vulnerabilities, marking inputs as "tainted" and monitoring their propagation. Control Flow Analysis maps the sequence of executed instructions to understand the program's behavior and decision points. Core to Taint Analysis is its ability to detect how tainted data influences variables and control structures, preventing injection attacks and data leaks.
Key Differences Between Control Flow and Taint Analysis
Control Flow Analysis examines the execution paths within a program to identify potential vulnerabilities by mapping how control moves between code blocks, while Taint Analysis tracks the flow of untrusted input data through a program to detect security risks like injection attacks. Control Flow Analysis is primarily concerned with the program's structure and logic, identifying unreachable code or infinite loops, whereas Taint Analysis focuses on data flow, monitoring how external inputs affect program variables and system calls. The key difference lies in their focus: Control Flow Analysis targets control structures and execution order, and Taint Analysis emphasizes data origin and propagation through the software.
Use Cases for Control Flow Analysis
Control Flow Analysis is primarily used in software debugging, security vulnerability detection, and performance optimization by examining the execution paths of a program. It helps identify unreachable code, infinite loops, and logic errors, enabling developers to refine application efficiency and correctness. In contrast to Taint Analysis, which tracks data flow for security breaches, Control Flow Analysis is crucial for understanding program behavior and ensuring robust software architecture.
Use Cases for Taint Analysis
Taint analysis is primarily used in cybersecurity to detect and prevent vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows by tracking the flow of untrusted input throughout a program. It helps identify how user-controlled data propagates, highlighting potential security risks in web applications, mobile apps, and network protocols. Unlike control flow analysis, which maps the execution paths of a program, taint analysis focuses on data flow to pinpoint unsafe data usage and mitigate security breaches.
Strengths and Limitations of Control Flow Analysis
Control Flow Analysis excels in mapping the execution paths within a program, enabling precise identification of potential vulnerabilities related to logical errors and unreachable code through control structure evaluation. Its limitations include difficulty handling dynamic features such as runtime code generation and insufficient granularity in tracking data flow, which can lead to missed taint sources in security contexts. Unlike Taint Analysis, which specializes in tracing the propagation of untrusted input to sensitive operations, Control Flow Analysis provides a broader view of program behavior but lacks detailed insight into data dependencies and taint propagation.
Strengths and Limitations of Taint Analysis
Taint analysis excels in tracking the flow of sensitive data through applications, effectively identifying vulnerabilities like SQL injection and cross-site scripting by marking user inputs as tainted and monitoring their propagation. However, it faces limitations in handling complex control flows and implicit flows, which can lead to false negatives or an incomplete security assessment. While control flow analysis provides a comprehensive view of program execution paths, taint analysis specifically targets data flow, making it indispensable for detecting input-based attacks but less effective for analyzing overall program behavior.
Choosing Between Control Flow and Taint Analysis
Choosing between control flow analysis and taint analysis depends on the specific security goals and context of the software. Control flow analysis excels at detecting logical errors and unintended execution paths, making it ideal for vulnerability identification related to program structure. Taint analysis is more effective for tracking data flow from untrusted sources to sensitive sinks, crucial for identifying injection flaws and data leakage.
Integrating Control Flow and Taint Analysis for Enhanced Security
Integrating control flow analysis with taint analysis enhances security by providing comprehensive tracking of both program execution paths and data propagation, enabling precise identification of potential vulnerabilities such as injection attacks or data leaks. Control flow analysis maps the possible execution paths, while taint analysis tags untrusted data and monitors its flow through the system, together improving detection of complex security flaws that isolated techniques might miss. This combined approach leverages static and dynamic analysis to reduce false positives and false negatives, optimizing vulnerability detection in software applications.
Control Flow Analysis Infographic
 libterm.com
libterm.com