The Admission Controller is a crucial component in Kubernetes that intercepts API requests before persistence, enforcing policies and validating resources to ensure cluster security and stability. By managing resource quotas, validating configurations, and preventing unauthorized actions, it helps maintain a predictable and reliable environment for your workloads. Discover how the Admission Controller enhances Kubernetes operations and why it matters for your cluster management in the rest of this article.
Table of Comparison
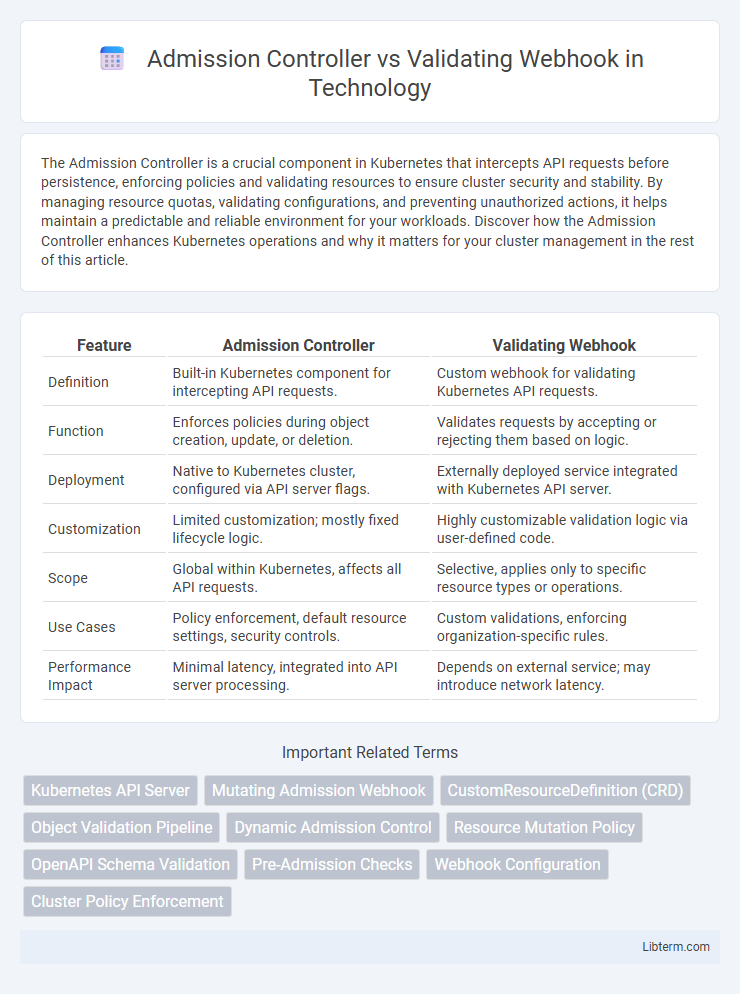
| Feature | Admission Controller | Validating Webhook |
|---|---|---|
| Definition | Built-in Kubernetes component for intercepting API requests. | Custom webhook for validating Kubernetes API requests. |
| Function | Enforces policies during object creation, update, or deletion. | Validates requests by accepting or rejecting them based on logic. |
| Deployment | Native to Kubernetes cluster, configured via API server flags. | Externally deployed service integrated with Kubernetes API server. |
| Customization | Limited customization; mostly fixed lifecycle logic. | Highly customizable validation logic via user-defined code. |
| Scope | Global within Kubernetes, affects all API requests. | Selective, applies only to specific resource types or operations. |
| Use Cases | Policy enforcement, default resource settings, security controls. | Custom validations, enforcing organization-specific rules. |
| Performance Impact | Minimal latency, integrated into API server processing. | Depends on external service; may introduce network latency. |
Introduction to Admission Controllers and Validating Webhooks
Admission Controllers are plugins that intercept Kubernetes API requests to enforce policies and validate resource configurations before they are persisted. Validating Webhooks are a specific type of Admission Controller that perform custom validation logic by sending admission requests to an external HTTP callback. Both work together to enhance cluster security and policy enforcement by ensuring that all resource modifications comply with predefined rules.
Key Concepts: Admission Controllers Explained
Admission Controllers are integral Kubernetes components that intercept API requests to enforce policies before persistence, operating synchronously with the API server to validate or mutate objects. Validating Webhooks act as dynamic Admission Controllers, enabling custom validation logic through HTTP callbacks, extending native Kubernetes policy enforcement. Both mechanisms ensure cluster security and compliance by scrutinizing resource definitions, but Validating Webhooks offer customizable, user-defined admission control beyond built-in functionality.
Overview of Validating Webhooks
Validating Webhooks in Kubernetes serve as admission controllers that intercept API requests to enforce custom validation logic before resource persistence. They enable dynamic, fine-grained policy enforcement by executing external HTTP callbacks during resource creation, update, or deletion operations. This mechanism enhances cluster security and consistency by ensuring compliance with organizational or application-specific requirements.
Core Differences Between Admission Controllers and Validating Webhooks
Admission Controllers are native Kubernetes components that enforce cluster policies by intercepting API requests before they persist, while Validating Webhooks are external HTTP callbacks that provide dynamic validation logic during resource admission. Admission Controllers operate within the Kubernetes control plane, offering built-in, static policy enforcement, whereas Validating Webhooks allow custom, extensible rule implementation managed outside the core system. The primary difference lies in their management and flexibility: Admission Controllers are tightly integrated and limited to predefined checks, whereas Validating Webhooks enable customizable, externally maintained validation without modifying the Kubernetes source code.
Use Cases for Admission Controllers
Admission Controllers enforce policies during Kubernetes resource creation, updating, or deletion to ensure compliance with organizational standards and security requirements. Use cases include enforcing resource quotas, validating pod security contexts, and mutating requests to inject sidecars or default labels automatically. Validating Webhooks specialize in dynamic, external validation logic for custom admission rules, while Admission Controllers provide built-in, native policy enforcement within the Kubernetes API server.
Common Applications of Validating Webhooks
Validating Webhooks are commonly used in Kubernetes to enforce custom policy validation during resource admission, ensuring configurations meet organizational standards before acceptance. They provide dynamic validation for API requests, such as enforcing label conventions, security policies, or resource quotas, enhancing cluster governance. Admission Controllers perform built-in checks and modifications, but Validating Webhooks extend this by enabling custom, flexible, and runtime-configurable validation logic.
Configuration and Implementation Best Practices
Admission Controllers are built-in Kubernetes components configured via API server flags to enforce cluster policies, while Validating Webhooks require external server endpoints registered in the AdmissionRegistration API for dynamic validation. Best practices for Admission Controller configuration include enabling only necessary controllers and monitoring API server flags closely, whereas Validating Webhooks demand secure TLS configurations, idempotent validation logic, and proper failure policy settings to avoid admission disruptions. Employing namespace or label selectors optimizes webhook targeting and reduces latency, while ensuring redundancy and health checks for webhook servers enhances cluster reliability during admission requests.
Security Implications and Considerations
Admission Controllers enforce security policies at the Kubernetes API server level to prevent unauthorized resource creation and modification, ensuring cluster integrity through built-in or custom logic. Validating Webhooks provide dynamic, customizable validation by intercepting API requests and rejecting those that do not meet specified security criteria, offering fine-grained control over resource admission. Both methods must be carefully secured to prevent elevation-of-privilege attacks, ensure proper authentication and authorization, and avoid Denial of Service (DoS) risks by implementing timeout and fail-closed policies.
Performance Impact on Kubernetes Clusters
Admission Controllers in Kubernetes operate synchronously within the API server, potentially introducing latency as they execute admission logic before object persistence, whereas Validating Webhooks invoke external services over the network, which can amplify response times and affect cluster performance depending on webhook service reliability and network latency. The performance impact of Admission Controllers is generally lower as they are integrated components optimized for speed, while Validating Webhooks require careful management of timeout settings and scaling of webhook services to avoid bottlenecks in high-throughput clusters. Optimizing webhook endpoint responsiveness and leveraging built-in Admission Controllers for common validation tasks can improve overall API server efficiency and minimize delays in resource admission.
Choosing the Right Approach for Your Kubernetes Environment
Admission Controllers enforce policies directly within the Kubernetes API server, offering faster decision-making and tighter integration for resource validation and mutation. Validating Webhooks provide flexible, external, and customizable validation logic, suitable for complex policies or dynamic environments requiring real-time rule updates without API server restarts. Assess cluster performance impact, policy complexity, and management overhead to choose the right approach, balancing native efficiency with extensibility in your Kubernetes environment.
Admission Controller Infographic
 libterm.com
libterm.com